In this age of technology, where screens have become the dominant feature of our lives but the value of tangible printed products hasn't decreased. No matter whether it's for educational uses for creative projects, simply adding an extra personal touch to your area, Public Key Encryption Algorithm Example have become an invaluable resource. We'll dive deeper into "Public Key Encryption Algorithm Example," exploring what they are, how to find them, and how they can enrich various aspects of your daily life.
Get Latest Public Key Encryption Algorithm Example Below
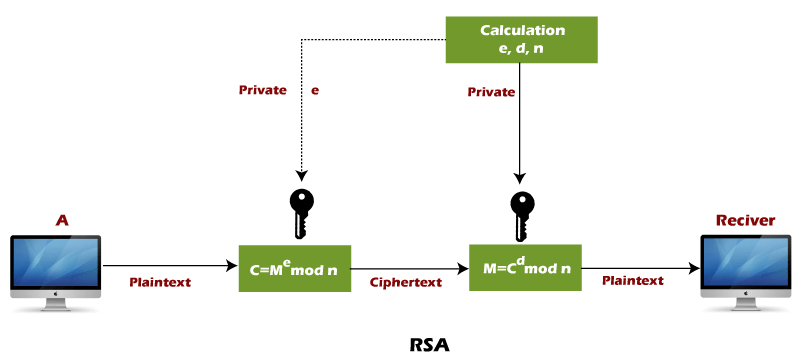
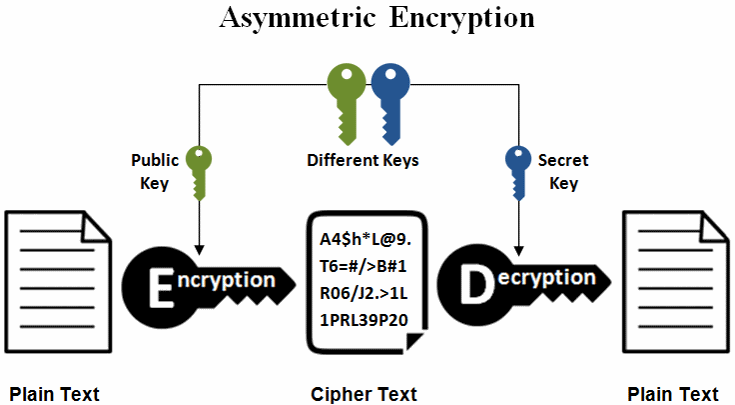
Public Key Encryption Algorithm Example
Public Key Encryption Algorithm Example -
You will be required to login to your Public Mobile Community Account to contact CS Agent Once you are finished making the ticket with CS Agent please ensure that you monitor for
Solved This is my first month payment and I am not able to create an account I tried so many times but it s not working
Public Key Encryption Algorithm Example cover a large array of printable materials available online at no cost. These resources come in many styles, from worksheets to templates, coloring pages and more. The attraction of printables that are free is their versatility and accessibility.
More of Public Key Encryption Algorithm Example
RSA Encryption Brilliant Math Science Wiki

RSA Encryption Brilliant Math Science Wiki
Hey Community We are excited to announce that starting today we re introducing eSIM availability to both new and existing subscribers along with the rollout of multiple
I ve been a customer of Public Mobile for 5 years and I use PM for all my 2 factor authentication Recently I ve been having to travel internationally frequently and have found
Print-friendly freebies have gained tremendous popularity due to a variety of compelling reasons:
-
Cost-Efficiency: They eliminate the need to buy physical copies or costly software.
-
customization: There is the possibility of tailoring printables to fit your particular needs whether you're designing invitations making your schedule, or even decorating your home.
-
Educational value: Free educational printables are designed to appeal to students from all ages, making these printables a powerful device for teachers and parents.
-
Convenience: instant access many designs and templates will save you time and effort.
Where to Find more Public Key Encryption Algorithm Example
RSA Encryption System

RSA Encryption System
1 Administrator Default Public All Users
Received a text saying Public Mobile is having issues transferring my number I read from other forum pages that there is a TELUS support number I can call to get live support to re trigger
After we've peaked your interest in Public Key Encryption Algorithm Example We'll take a look around to see where you can find these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer a huge selection of Public Key Encryption Algorithm Example suitable for many goals.
- Explore categories like furniture, education, organization, and crafts.
2. Educational Platforms
- Educational websites and forums often provide worksheets that can be printed for free or flashcards as well as learning tools.
- The perfect resource for parents, teachers and students looking for extra resources.
3. Creative Blogs
- Many bloggers offer their unique designs and templates for no cost.
- These blogs cover a broad range of interests, that range from DIY projects to party planning.
Maximizing Public Key Encryption Algorithm Example
Here are some innovative ways that you can make use of printables that are free:
1. Home Decor
- Print and frame gorgeous artwork, quotes or seasonal decorations to adorn your living spaces.
2. Education
- Print worksheets that are free to help reinforce your learning at home and in class.
3. Event Planning
- Design invitations and banners and decorations for special occasions like weddings and birthdays.
4. Organization
- Keep your calendars organized by printing printable calendars as well as to-do lists and meal planners.
Conclusion
Public Key Encryption Algorithm Example are an abundance of practical and imaginative resources that meet a variety of needs and interest. Their accessibility and versatility make them an invaluable addition to both professional and personal lives. Explore the many options of Public Key Encryption Algorithm Example now and unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables available for download really for free?
- Yes you can! You can print and download these tools for free.
-
Can I use the free printables for commercial uses?
- It's contingent upon the specific rules of usage. Always review the terms of use for the creator prior to using the printables in commercial projects.
-
Are there any copyright violations with Public Key Encryption Algorithm Example?
- Some printables may contain restrictions on use. Always read these terms and conditions as set out by the creator.
-
How do I print printables for free?
- Print them at home using either a printer at home or in a local print shop for higher quality prints.
-
What software will I need to access printables for free?
- Most printables come in the format of PDF, which is open with no cost software, such as Adobe Reader.
Asymmetric Key Cryptography RSA Encryption Algorithm Asymmetric

Encryption A Beginner s Guide Start Learning With StorMagic
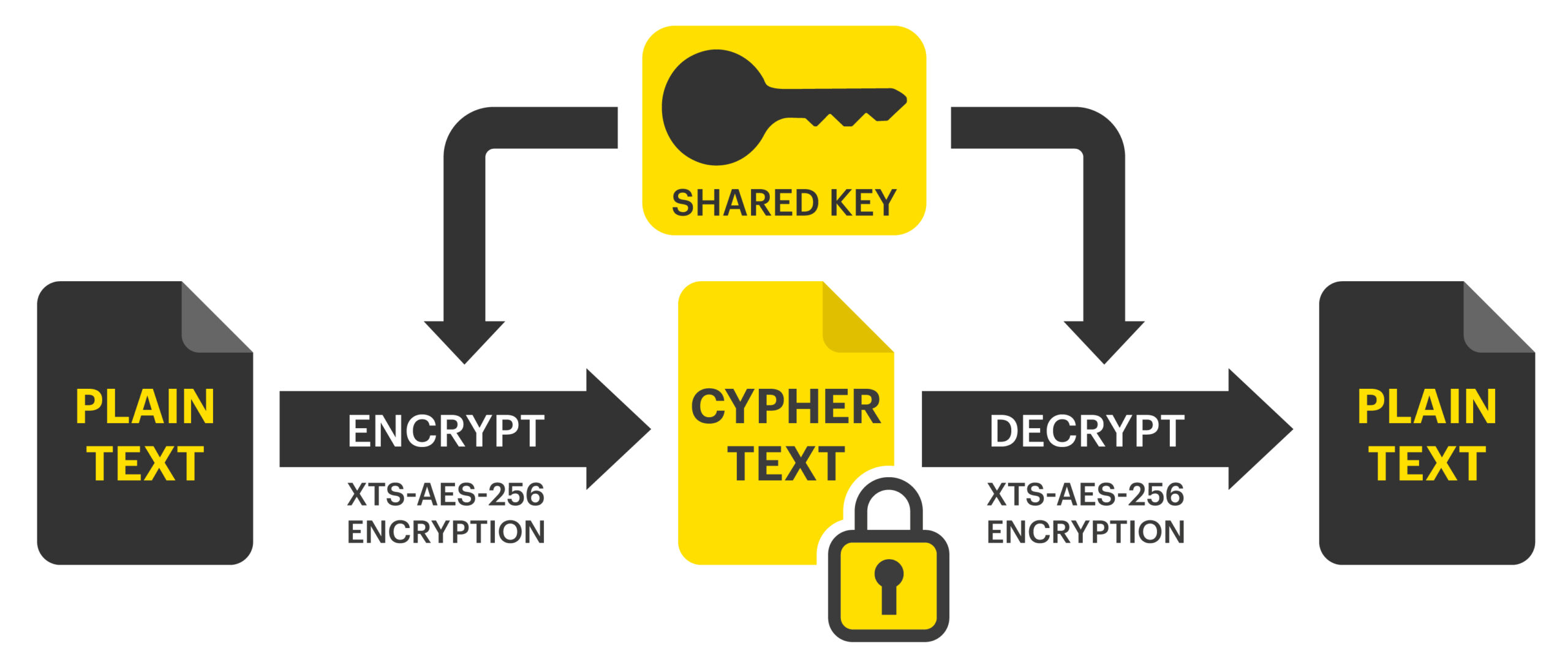
Check more sample of Public Key Encryption Algorithm Example below
RSA Encryption Algorithm Javatpoint Encryption Algorithms

RSA Algorithm Secure Your Data With Public Key Encryption
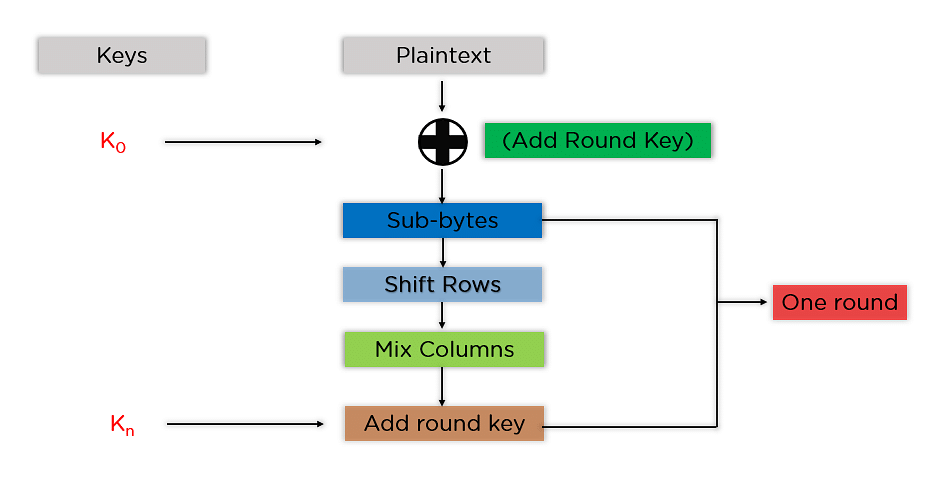
Encryption Choices Rsa Vs Aes Explained Prey

Public Key Encryption What Is Public Cryptography Okta AU NZ

Edu Resources RSA Algorithm RSA Algorithm Explain With Example

Symmetric Encryption Algorithms Live Long Encrypt Security Boulevard


https://productioncommunity.publicmobile.ca › Get-Support › Account...
Solved This is my first month payment and I am not able to create an account I tried so many times but it s not working

https://productioncommunity.publicmobile.ca › Get-Support › bd-p › ...
Pack Your Bags Public Mobile s Trip to Mexico Contest is Here Hello Community We re thrilled to announce an exciting contest to celebrate our new CAN US MEX plans Get ready to spice
Solved This is my first month payment and I am not able to create an account I tried so many times but it s not working
Pack Your Bags Public Mobile s Trip to Mexico Contest is Here Hello Community We re thrilled to announce an exciting contest to celebrate our new CAN US MEX plans Get ready to spice

Public Key Encryption What Is Public Cryptography Okta AU NZ

RSA Algorithm Secure Your Data With Public Key Encryption

Edu Resources RSA Algorithm RSA Algorithm Explain With Example

Symmetric Encryption Algorithms Live Long Encrypt Security Boulevard
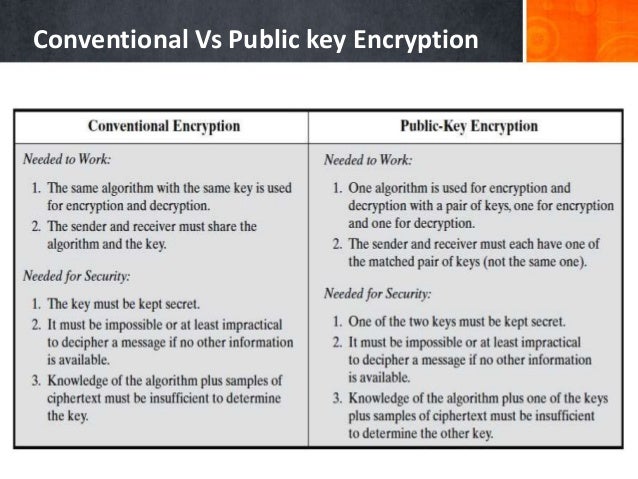
Public Key Encryption Algorithm Example
ECC Encryption Decryption CodeAhoy

ECC Encryption Decryption CodeAhoy

Symmetric Key Encryption Complete Guide To Symmetric Key Encryption