In this age of electronic devices, when screens dominate our lives, the charm of tangible, printed materials hasn't diminished. If it's to aid in education, creative projects, or simply to add an extra personal touch to your area, Privileged Access Management Examples can be an excellent resource. The following article is a take a dive into the world "Privileged Access Management Examples," exploring what they are, how they are, and how they can improve various aspects of your lives.
Get Latest Privileged Access Management Examples Below

Privileged Access Management Examples
Privileged Access Management Examples -
How a PAM solution can help you manage all the privileged account within your environment How to use unique identifiable accounts without creating personal accounts for all administrators How a secure proxy helps you to mitigate a pass the hash attack
Organizations implement privileged access management PAM to protect against the threats posed by credential theft and privilege misuse PAM refers to a comprehensive cybersecurity strategy comprising people processes and technology to control monitor secure and audit all human and non human privileged identities and activities
Privileged Access Management Examples encompass a wide collection of printable content that can be downloaded from the internet at no cost. They are available in a variety of types, like worksheets, coloring pages, templates and many more. The appealingness of Privileged Access Management Examples is in their versatility and accessibility.
More of Privileged Access Management Examples
What Is Privileged Access Management Why It Should Be A Security Priority

What Is Privileged Access Management Why It Should Be A Security Priority
Find the top Privileged Access Management with Gartner Compare and filter by verified product reviews and choose the software that s right for your organization
Privileged Access Management is a subset access solution that s a part of IAM PAM is generally accepted as a smaller package that deals with solutions and tools required for the security and safeguarding of privileged accounts for networks and devices
Privileged Access Management Examples have garnered immense appeal due to many compelling reasons:
-
Cost-Efficiency: They eliminate the need to buy physical copies or expensive software.
-
customization You can tailor the templates to meet your individual needs for invitations, whether that's creating them for your guests, organizing your schedule or decorating your home.
-
Educational Benefits: The free educational worksheets offer a wide range of educational content for learners of all ages, which makes these printables a powerful instrument for parents and teachers.
-
Simple: Quick access to the vast array of design and templates saves time and effort.
Where to Find more Privileged Access Management Examples
The Top 10 Privileged Access Management PAM Solutions 2022 Expert

The Top 10 Privileged Access Management PAM Solutions 2022 Expert
Privileged access management PAM is a system that assigns higher permission levels to accounts with access to critical resources and admin level controls PAM is based on the principle of least privilege which is crucial to modern cybersecurity best practices
Privileged access management PAM consists of the cybersecurity strategies and technologies for exerting control over the elevated privileged access and permissions for identities users accounts processes and systems across an IT environment
After we've peaked your curiosity about Privileged Access Management Examples Let's find out where you can discover these hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer a vast selection of Privileged Access Management Examples designed for a variety purposes.
- Explore categories like furniture, education, crafting, and organization.
2. Educational Platforms
- Educational websites and forums typically provide worksheets that can be printed for free as well as flashcards and other learning materials.
- This is a great resource for parents, teachers and students looking for extra sources.
3. Creative Blogs
- Many bloggers share their imaginative designs with templates and designs for free.
- These blogs cover a broad array of topics, ranging including DIY projects to planning a party.
Maximizing Privileged Access Management Examples
Here are some innovative ways how you could make the most use of printables for free:
1. Home Decor
- Print and frame beautiful art, quotes, or seasonal decorations to adorn your living areas.
2. Education
- Use these printable worksheets free of charge to aid in learning at your home or in the classroom.
3. Event Planning
- Designs invitations, banners and decorations for special occasions like weddings and birthdays.
4. Organization
- Keep your calendars organized by printing printable calendars checklists for tasks, as well as meal planners.
Conclusion
Privileged Access Management Examples are a treasure trove of fun and practical tools for a variety of needs and interest. Their accessibility and flexibility make them an invaluable addition to both personal and professional life. Explore the vast array of Privileged Access Management Examples to unlock new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables for free really absolutely free?
- Yes they are! You can download and print the resources for free.
-
Can I use the free templates for commercial use?
- It's based on specific terms of use. Always consult the author's guidelines prior to using the printables in commercial projects.
-
Are there any copyright problems with printables that are free?
- Certain printables could be restricted in their usage. Make sure you read the terms and condition of use as provided by the creator.
-
How do I print printables for free?
- Print them at home with either a printer at home or in any local print store for the highest quality prints.
-
What software is required to open printables free of charge?
- The majority of PDF documents are provided in the PDF format, and can be opened with free software like Adobe Reader.
Essentials Of Privileged Access Management Fortra
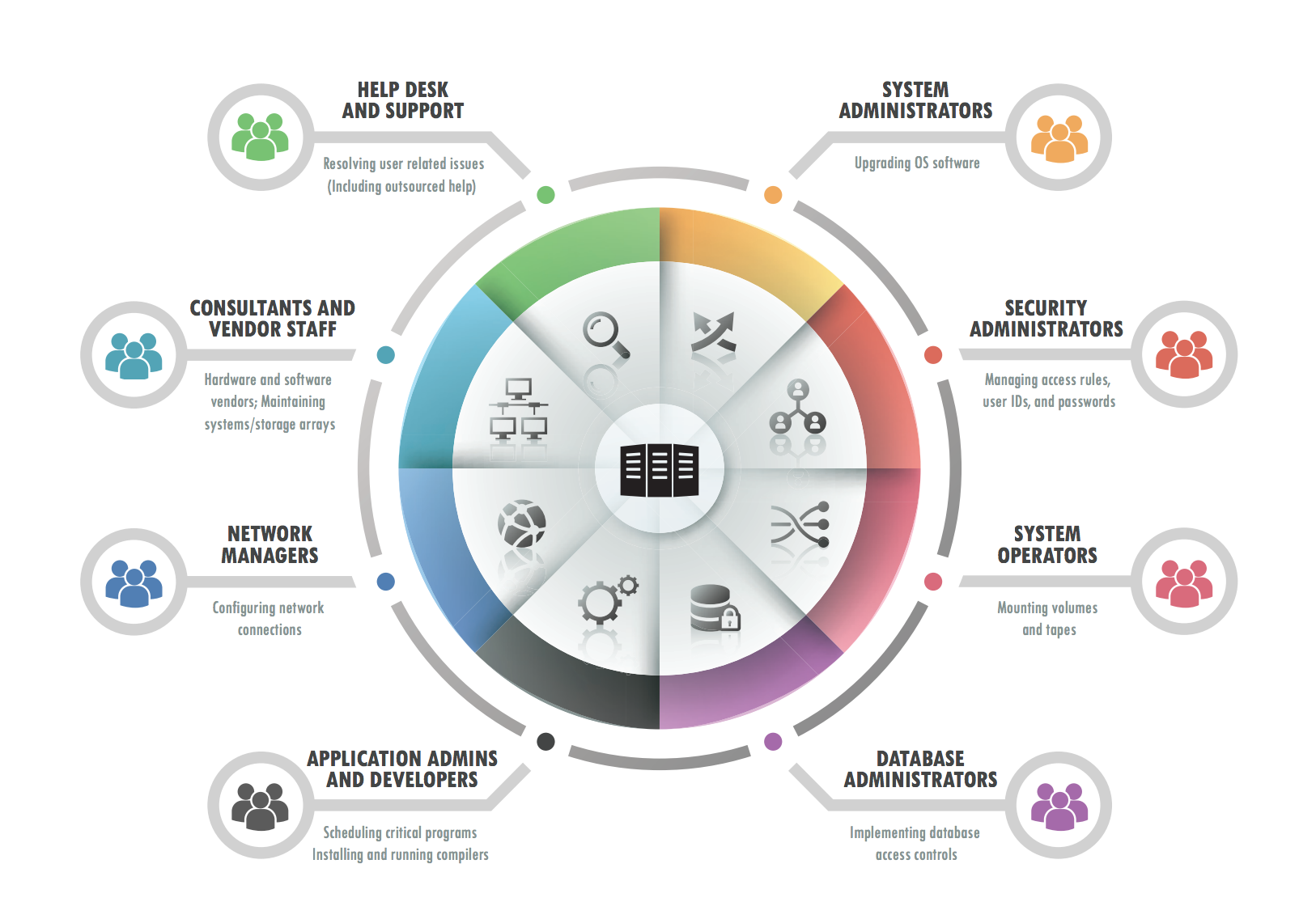
What Is Privileged Access Management PAM Delinea
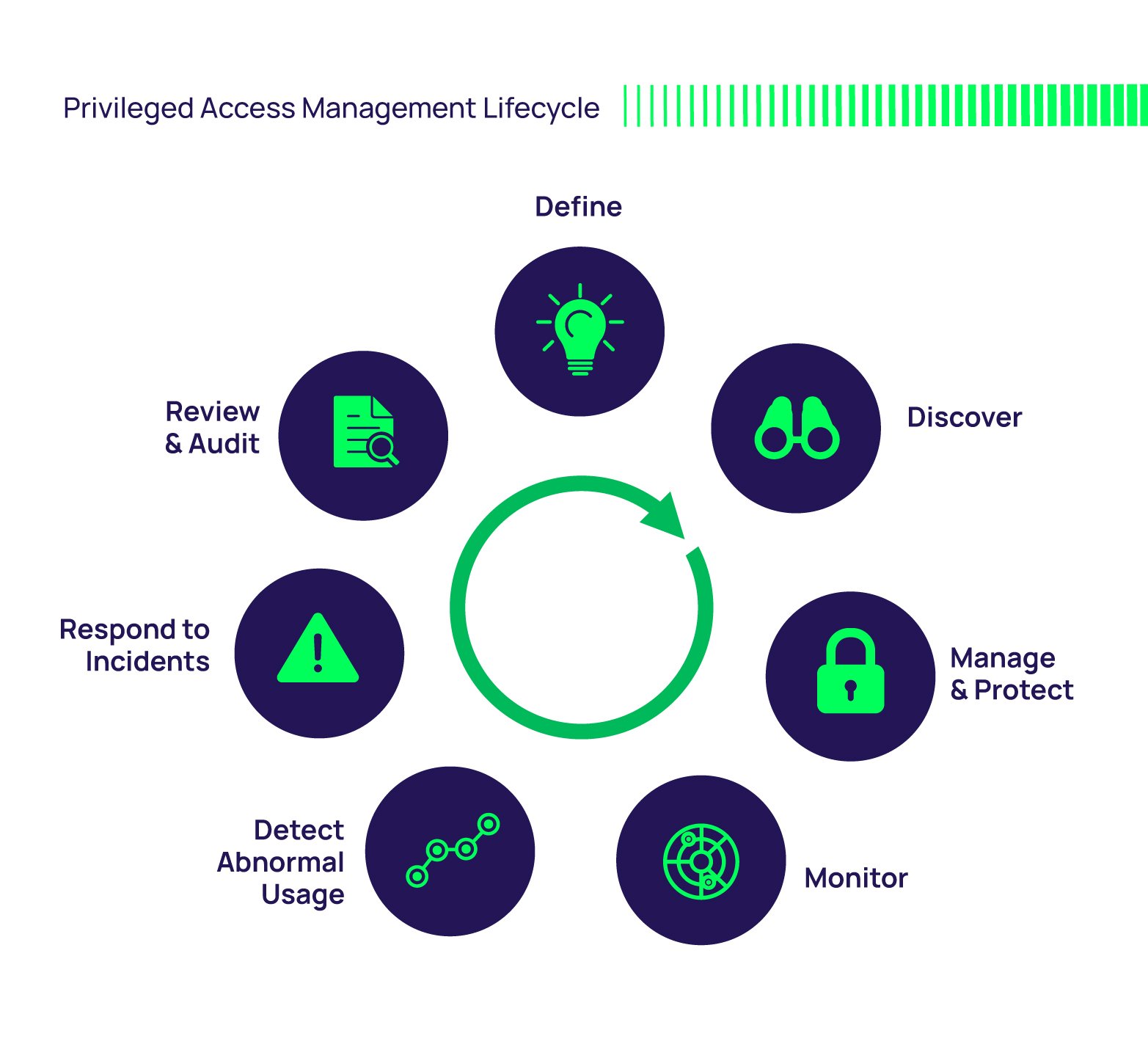
Check more sample of Privileged Access Management Examples below
Privileged Access Management PAM Bitsiel nl

The Importance Of Privileged Access Management Ninawa Clibrary
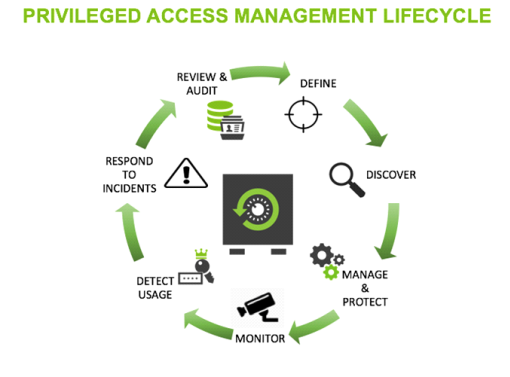
Sichern Des Privilegierten Zugriffs Enterprise Zugriffsmodell

Privileged Access Workstation VMware

Privileged Access Management For Active Directory Domain Services
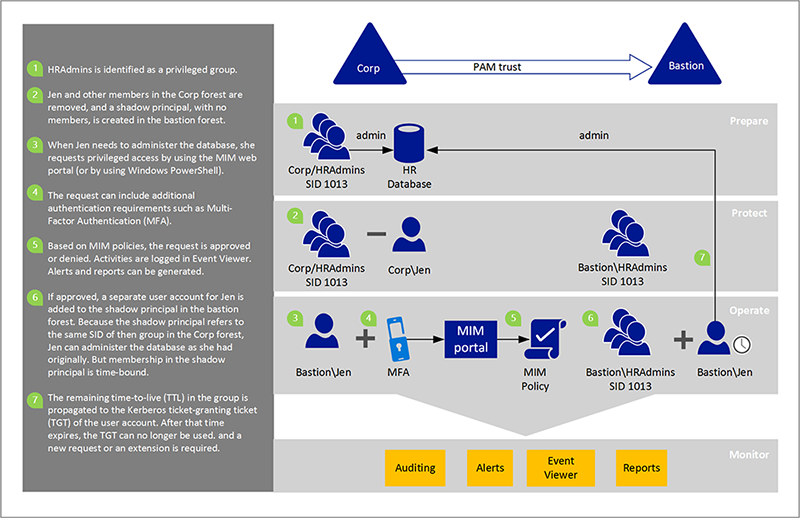
What Is Privileged Access Management PAM


https://www.cyberark.com/what-is/privileged-access-management
Organizations implement privileged access management PAM to protect against the threats posed by credential theft and privilege misuse PAM refers to a comprehensive cybersecurity strategy comprising people processes and technology to control monitor secure and audit all human and non human privileged identities and activities

https://www.crowdstrike.com/en-us/cybersecurity...
Privileged access management works by enforcing security procedures and controls that limit and monitor privileged account access It consists of secure authentication authorization and auditing techniques that help ensure only authorized individuals have access to sensitive systems and data
Organizations implement privileged access management PAM to protect against the threats posed by credential theft and privilege misuse PAM refers to a comprehensive cybersecurity strategy comprising people processes and technology to control monitor secure and audit all human and non human privileged identities and activities
Privileged access management works by enforcing security procedures and controls that limit and monitor privileged account access It consists of secure authentication authorization and auditing techniques that help ensure only authorized individuals have access to sensitive systems and data

Privileged Access Workstation VMware

The Importance Of Privileged Access Management Ninawa Clibrary

Privileged Access Management For Active Directory Domain Services

What Is Privileged Access Management PAM

Privileged Access Management PAM Refers To A Class Of solutions
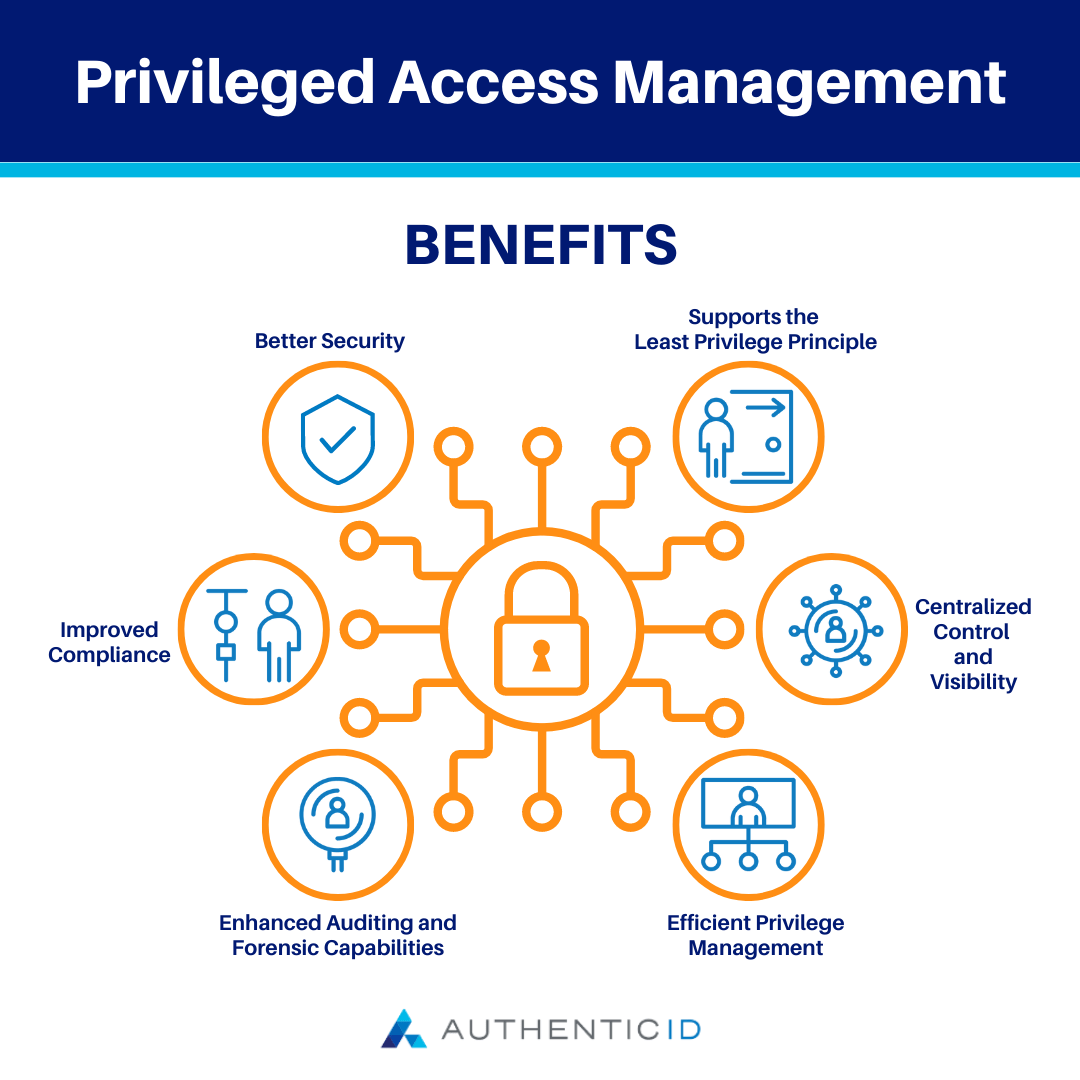
What Is Privileged Access Management PAM AuthenticID

What Is Privileged Access Management PAM AuthenticID
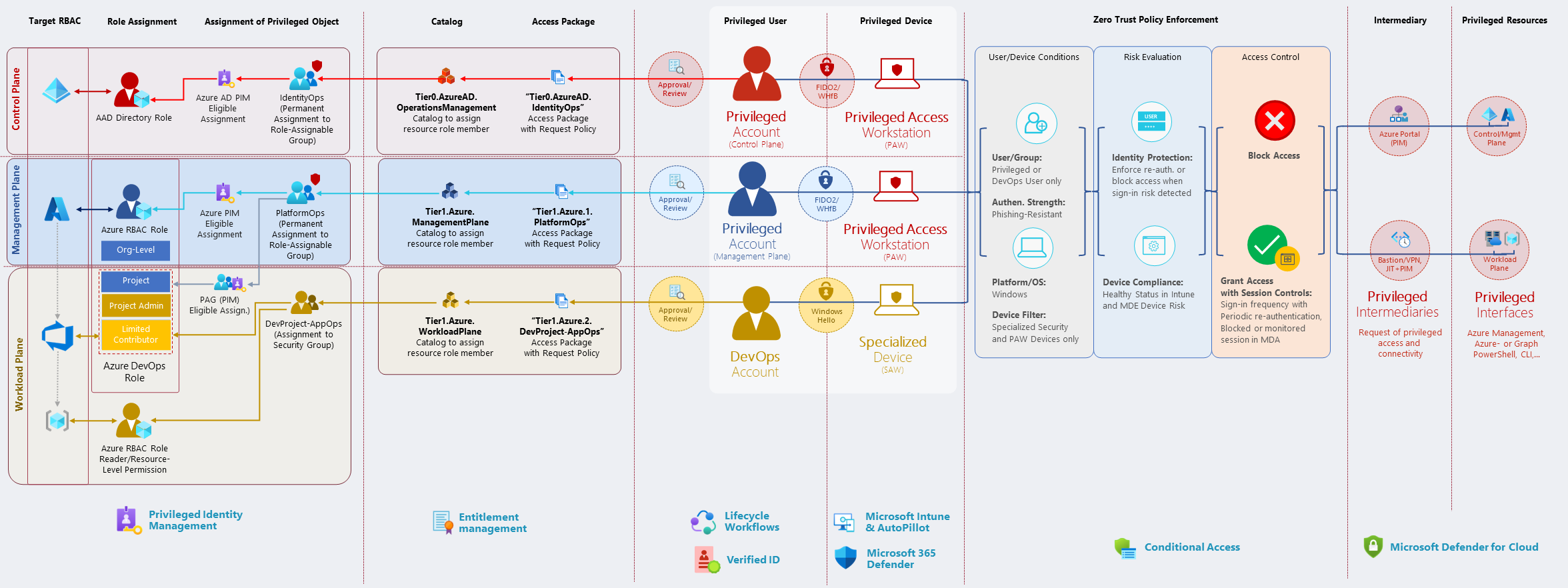
Securing Privileged User Access With Azure AD Conditional Access And