In a world in which screens are the norm and the appeal of physical printed items hasn't gone away. Whatever the reason, whether for education project ideas, artistic or just adding an individual touch to your home, printables for free are now a vital source. For this piece, we'll dive deeper into "Privilege Escalation Examples," exploring their purpose, where to find them, and how they can enrich various aspects of your lives.
Get Latest Privilege Escalation Examples Below

Privilege Escalation Examples
Privilege Escalation Examples -
LinPEAS Linux Privilege Escalation Awesome Script LinPEAS is a script that searches for possible paths to escalate privileges on Linux Unix MacOS hosts The checks are explained on book hacktricks xyz Check the Local Linux Privilege Escalation checklist from book hacktricks xyz
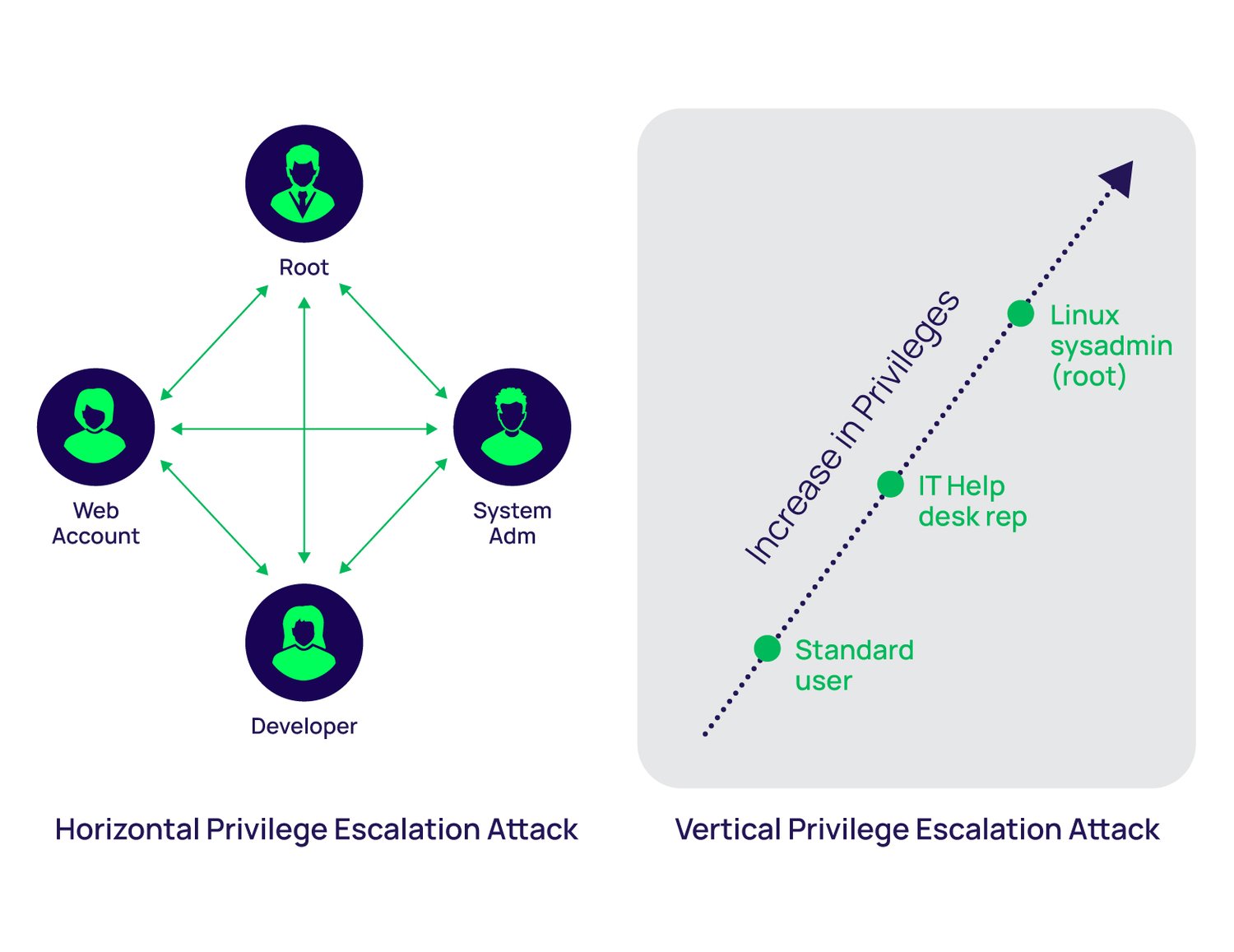
Here s an example of how a horizontal privilege escalation attack might unfold An attacker uses stolen credentials to access a host with regular privileges within a company s network The attacker identifies a file server within the network that has sensitive data Multiple users can access it but they can only read and write files
Printables for free cover a broad collection of printable documents that can be downloaded online at no cost. These materials come in a variety of forms, like worksheets templates, coloring pages and much more. The benefit of Privilege Escalation Examples is their flexibility and accessibility.
More of Privilege Escalation Examples
Privilege Escalation On Linux With Examples

Privilege Escalation On Linux With Examples
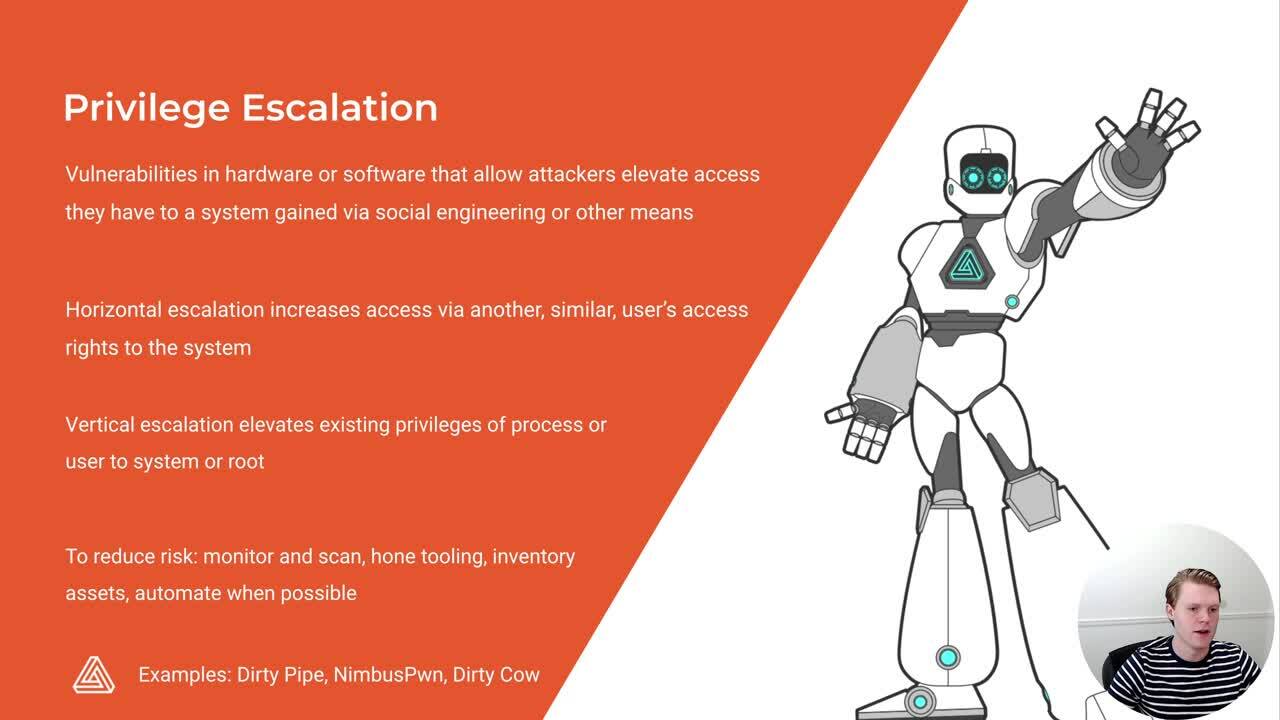
Examples of Privilege Escalation Attacks Privilege escalation attacks commonly involve infecting a network or application with malware a broad category that includes the following Worms Self contained programs that replicate themselves and spread copies to other computers
Examples of Privilege Escalation Attacks There are some common examples of hacking are discussed below along with the explanation Windows Sticky keys Windows Sysinternals Process Injection Linux Password User
Printables that are free have gained enormous popularity due to a variety of compelling reasons:
-
Cost-Efficiency: They eliminate the requirement of buying physical copies of the software or expensive hardware.
-
The ability to customize: It is possible to tailor designs to suit your personal needs when it comes to designing invitations to organize your schedule or even decorating your home.
-
Education Value Education-related printables at no charge are designed to appeal to students of all ages. This makes them a valuable tool for parents and educators.
-
Easy to use: immediate access numerous designs and templates helps save time and effort.
Where to Find more Privilege Escalation Examples
100 OFF Linux Privilege Escalation Examples From Zero To Hero OSCP

100 OFF Linux Privilege Escalation Examples From Zero To Hero OSCP
Alternatively using a silver ticket an attacker can create multiple ticket granting service TGS tickets for a specific service without communicating with the domain controller DC on a network How Privilege Escalation Attacks Work
For example privilege escalation can transform a simple malware infection into a catastrophic data breach Privilege escalations allow attackers to open up new attack vectors on a target system For example it can involve Gaining access to
We hope we've stimulated your curiosity about Privilege Escalation Examples Let's see where they are hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy have a large selection and Privilege Escalation Examples for a variety goals.
- Explore categories like decorating your home, education, organizational, and arts and crafts.
2. Educational Platforms
- Forums and educational websites often provide worksheets that can be printed for free for flashcards, lessons, and worksheets. materials.
- It is ideal for teachers, parents and students who are in need of supplementary sources.
3. Creative Blogs
- Many bloggers offer their unique designs and templates, which are free.
- These blogs cover a broad spectrum of interests, that range from DIY projects to planning a party.
Maximizing Privilege Escalation Examples
Here are some fresh ways in order to maximize the use use of printables that are free:
1. Home Decor
- Print and frame stunning artwork, quotes, and seasonal decorations, to add a touch of elegance to your living spaces.
2. Education
- Use printable worksheets for free for reinforcement of learning at home also in the classes.
3. Event Planning
- Make invitations, banners and decorations for special events such as weddings or birthdays.
4. Organization
- Be organized by using printable calendars for to-do list, lists of chores, and meal planners.
Conclusion
Privilege Escalation Examples are an abundance with useful and creative ideas that can meet the needs of a variety of people and passions. Their access and versatility makes they a beneficial addition to both professional and personal life. Explore the vast world of Privilege Escalation Examples to uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Do printables with no cost really gratis?
- Yes you can! You can print and download these files for free.
-
Does it allow me to use free printables for commercial purposes?
- It's contingent upon the specific rules of usage. Make sure you read the guidelines for the creator before using printables for commercial projects.
-
Are there any copyright rights issues with Privilege Escalation Examples?
- Some printables could have limitations in their usage. Be sure to check the terms and conditions set forth by the designer.
-
How do I print Privilege Escalation Examples?
- You can print them at home using printing equipment or visit a local print shop to purchase superior prints.
-
What software do I require to open Privilege Escalation Examples?
- The majority of printed documents are in the format of PDF, which is open with no cost programs like Adobe Reader.
Linux Privilege Escalation Examples From Zero To Hero OSCP

Linux Privilege Escalation Examples From Zero To Hero OSCP SoftArchive

Check more sample of Privilege Escalation Examples below
Linux Privilege Escalation Examples From Zero To Hero OSCP SoftArchive

Linux Privilege Escalation Examples From Zero To Hero OSCP

Linux Privilege Escalation Examples From Zero To Hero OSCP

Privilege Escalation On Linux With Examples
What Is Privilege Escalation YouTube

Privilege Escalation Attacks Types Examples And Defense

https://www.proofpoint.com/us/blog/identity-threat...
Here s an example of how a horizontal privilege escalation attack might unfold An attacker uses stolen credentials to access a host with regular privileges within a company s network The attacker identifies a file server within the network that has sensitive data Multiple users can access it but they can only read and write files

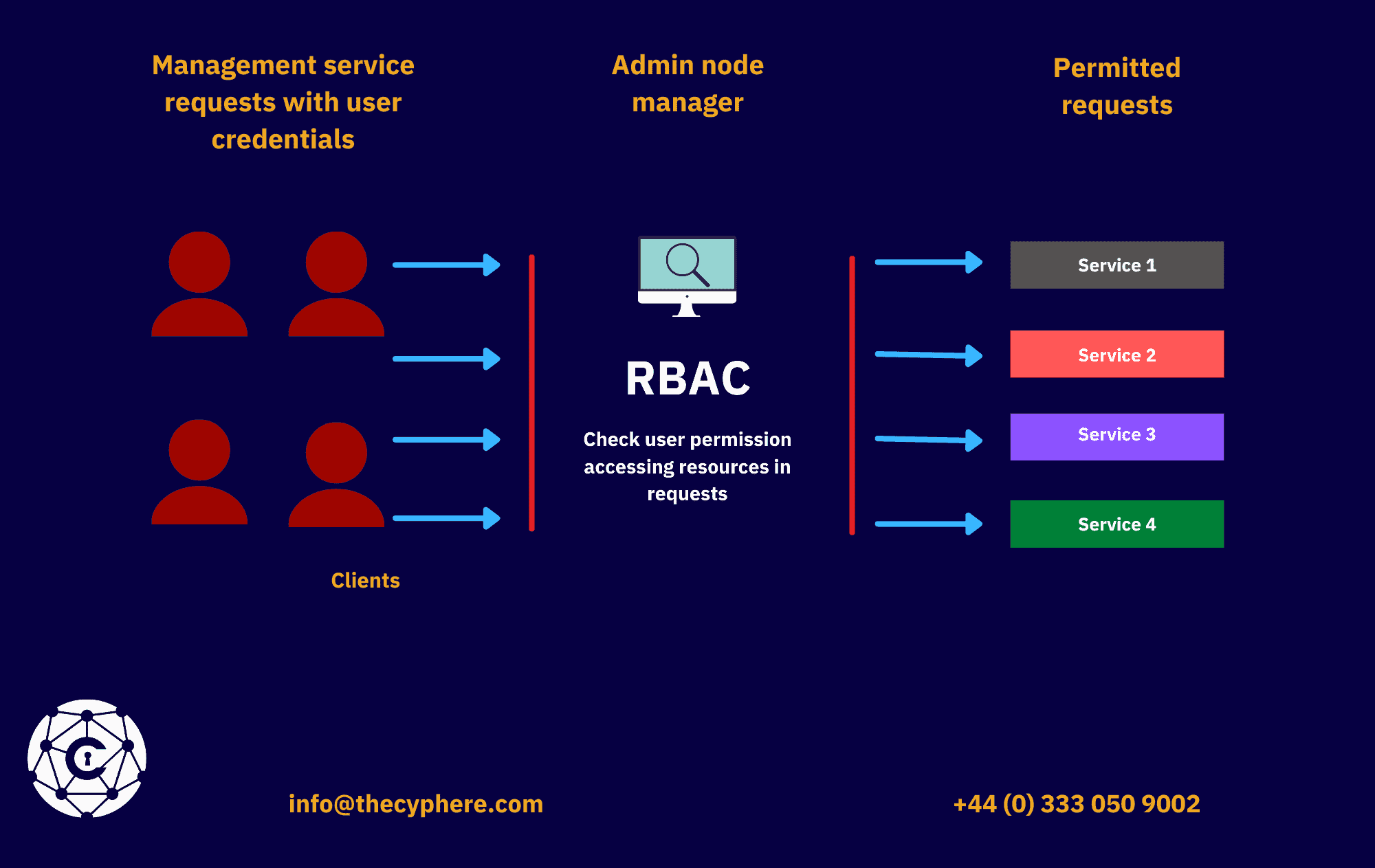
https://delinea.com/blog/windows-privilege-escalation
A recent example known as Print Nightmare CVE 2021 34527 is a vulnerability in the Print Spooler that enabled an attacker to perform remote code execution and privilege escalation An example of privilege escalation using Print Nightmare to create an Admin User on the system is below
Here s an example of how a horizontal privilege escalation attack might unfold An attacker uses stolen credentials to access a host with regular privileges within a company s network The attacker identifies a file server within the network that has sensitive data Multiple users can access it but they can only read and write files
A recent example known as Print Nightmare CVE 2021 34527 is a vulnerability in the Print Spooler that enabled an attacker to perform remote code execution and privilege escalation An example of privilege escalation using Print Nightmare to create an Admin User on the system is below

Privilege Escalation On Linux With Examples

Linux Privilege Escalation Examples From Zero To Hero OSCP

What Is Privilege Escalation YouTube

Privilege Escalation Attacks Types Examples And Defense

74 Methods For Privilege Escalation Part 2 HADESS
What Is Privilege Escalation

What Is Privilege Escalation

Linux Privilege Escalation Cheatsheet For Oscp Hacking Dream Vrogue