In the age of digital, when screens dominate our lives but the value of tangible, printed materials hasn't diminished. Be it for educational use for creative projects, simply adding personal touches to your area, Private Key Encryption Example have proven to be a valuable resource. With this guide, you'll take a dive into the world "Private Key Encryption Example," exploring what they are, how you can find them, and the ways that they can benefit different aspects of your lives.
Get Latest Private Key Encryption Example Below

Private Key Encryption Example
Private Key Encryption Example -
Wenn Sie in einem Inkognitofenster surfen und ein weiteres ffnen wird Ihre private Browsersitzung im neuen Fenster fortgesetzt Schlie en Sie alle Inkognitofenster um den
Private personal 1 private adj
Private Key Encryption Example provide a diverse collection of printable documents that can be downloaded online at no cost. The resources are offered in a variety types, like worksheets, templates, coloring pages, and more. The great thing about Private Key Encryption Example lies in their versatility as well as accessibility.
More of Private Key Encryption Example
Public Key Private Key Encryption Example Arqma Coin

Public Key Private Key Encryption Example Arqma Coin
If it s private only you can view the playlist Click Create To create a playlist from a Short Go to the watch page of a Short that you want in the playlist Click More Save Create new playlist
For a more private and secure browsing experience you can use Chrome s safety features like Safety Check and Safe Browsing Compromised passwords If you notice an unfamiliar activity
Print-friendly freebies have gained tremendous recognition for a variety of compelling motives:
-
Cost-Efficiency: They eliminate the need to buy physical copies of the software or expensive hardware.
-
Flexible: The Customization feature lets you tailor print-ready templates to your specific requirements such as designing invitations making your schedule, or even decorating your home.
-
Educational Value Education-related printables at no charge offer a wide range of educational content for learners of all ages. This makes them an invaluable tool for parents and teachers.
-
Convenience: The instant accessibility to a plethora of designs and templates saves time and effort.
Where to Find more Private Key Encryption Example
Public Key Private Key Encryption Example Arqma Coin

Public Key Private Key Encryption Example Arqma Coin
ODM OEM
If you browse on an Incognito window and you open another one your private browsing session continues in the new window To exit Incognito mode close all Incognito windows If you find a
Now that we've piqued your curiosity about Private Key Encryption Example and other printables, let's discover where you can discover these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer a vast selection of Private Key Encryption Example to suit a variety of objectives.
- Explore categories like furniture, education, organizational, and arts and crafts.
2. Educational Platforms
- Educational websites and forums frequently offer free worksheets and worksheets for printing Flashcards, worksheets, and other educational tools.
- Great for parents, teachers and students who are in need of supplementary resources.
3. Creative Blogs
- Many bloggers share their creative designs as well as templates for free.
- The blogs covered cover a wide spectrum of interests, including DIY projects to party planning.
Maximizing Private Key Encryption Example
Here are some innovative ways ensure you get the very most of Private Key Encryption Example:
1. Home Decor
- Print and frame gorgeous artwork, quotes, or even seasonal decorations to decorate your living spaces.
2. Education
- Print out free worksheets and activities to help reinforce your learning at home or in the classroom.
3. Event Planning
- Invitations, banners and decorations for special events like weddings and birthdays.
4. Organization
- Stay organized with printable planners for to-do list, lists of chores, and meal planners.
Conclusion
Private Key Encryption Example are a treasure trove of innovative and useful resources that satisfy a wide range of requirements and interest. Their access and versatility makes they a beneficial addition to both professional and personal life. Explore the vast array of Private Key Encryption Example to open up new possibilities!
Frequently Asked Questions (FAQs)
-
Are Private Key Encryption Example really gratis?
- Yes you can! You can print and download these resources at no cost.
-
Can I use the free printables for commercial uses?
- It's determined by the specific terms of use. Be sure to read the rules of the creator prior to printing printables for commercial projects.
-
Are there any copyright concerns with Private Key Encryption Example?
- Certain printables could be restricted regarding their use. Be sure to review the terms of service and conditions provided by the creator.
-
How can I print Private Key Encryption Example?
- Print them at home with an printer, or go to a print shop in your area for better quality prints.
-
What program do I require to view printables free of charge?
- Most PDF-based printables are available with PDF formats, which can be opened using free software like Adobe Reader.
DKIM Twilio

Symmetric Encryption IB Computer Science
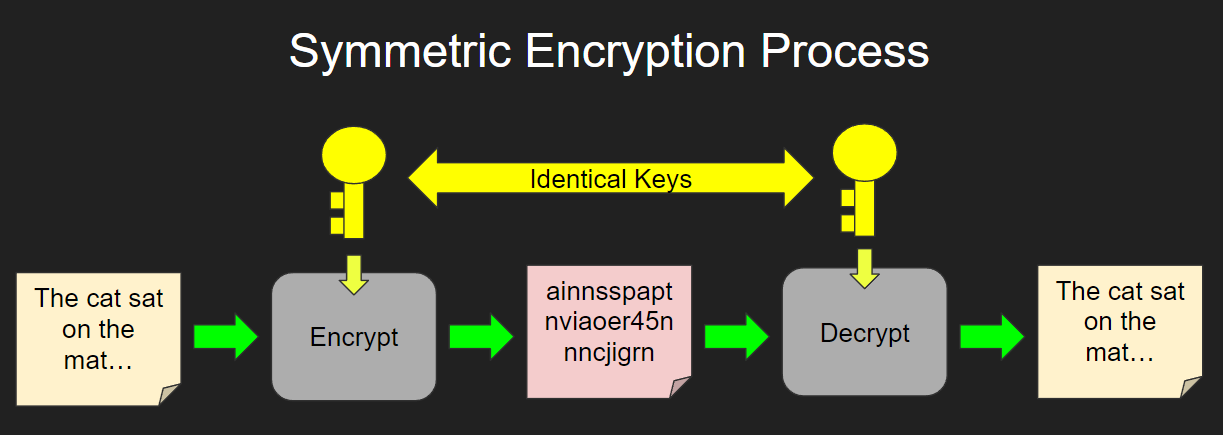
Check more sample of Private Key Encryption Example below
PGP Encryption Activities Activities UiPath Community Forum

What Is Encryption Vrogue co
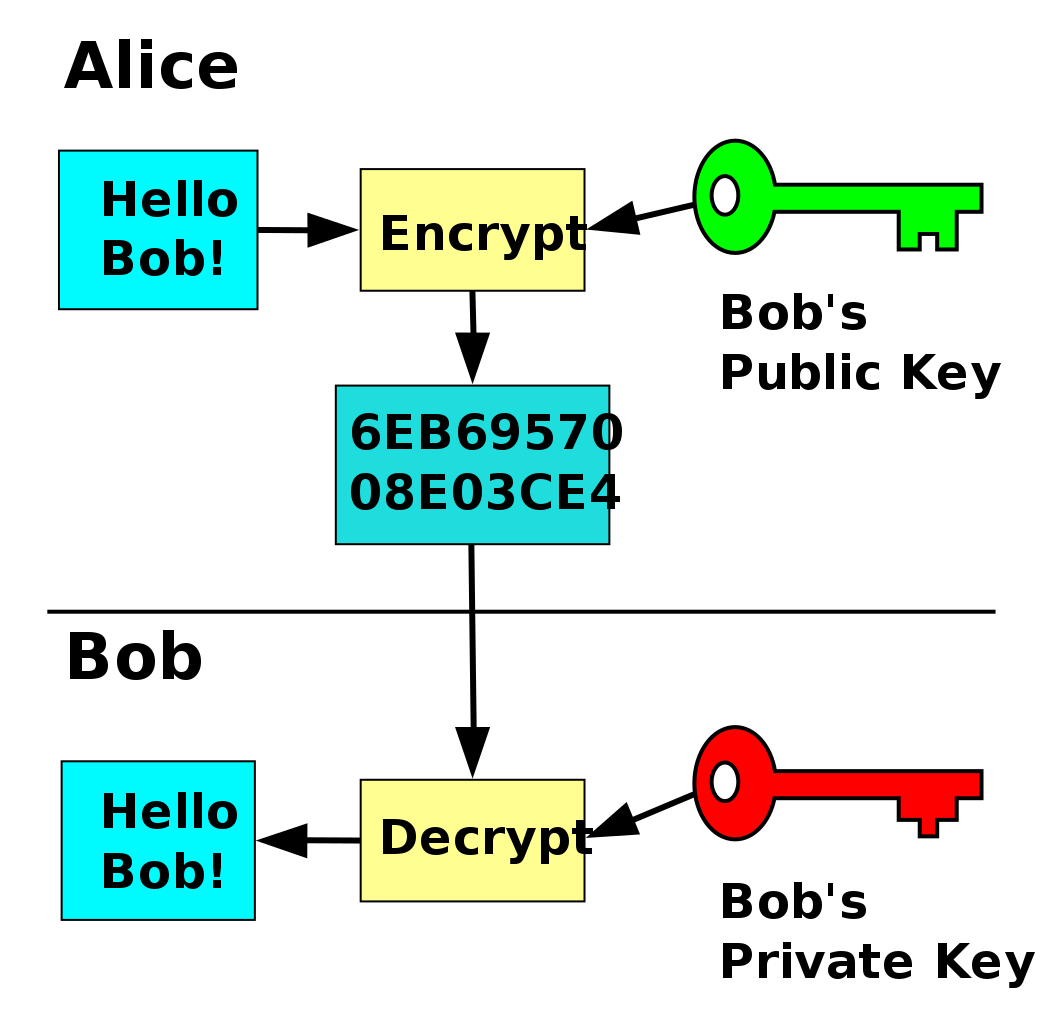
Public Key Encryption How Does Public Key Encryption Work
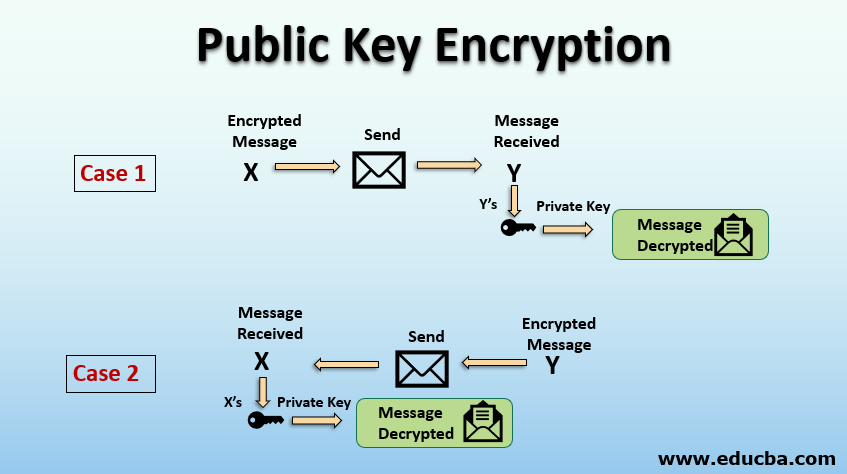
Public And Private Key Encryption System News Com
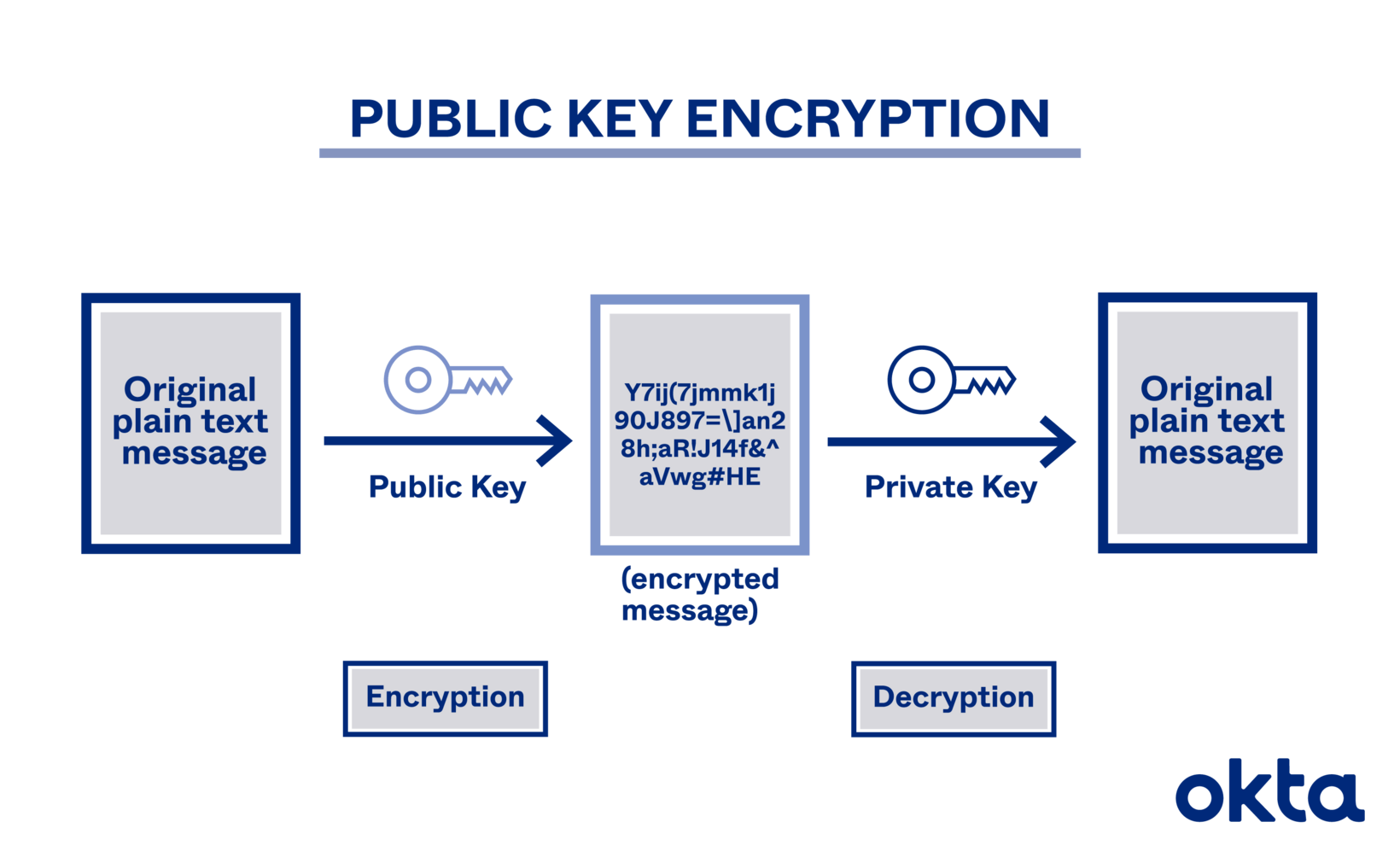
Public Key Cryptography Algorithms

Asymmetric Encryption How Asymmetric Encryption Works



https://support.google.com › calendar › answer
On events you mark as Private Guest lists of events without See guest list permission Subscribe to email alerts for future events or when you create change cancel or respond to
Private personal 1 private adj
On events you mark as Private Guest lists of events without See guest list permission Subscribe to email alerts for future events or when you create change cancel or respond to

Public And Private Key Encryption System News Com

What Is Encryption Vrogue co

Public Key Cryptography Algorithms

Asymmetric Encryption How Asymmetric Encryption Works
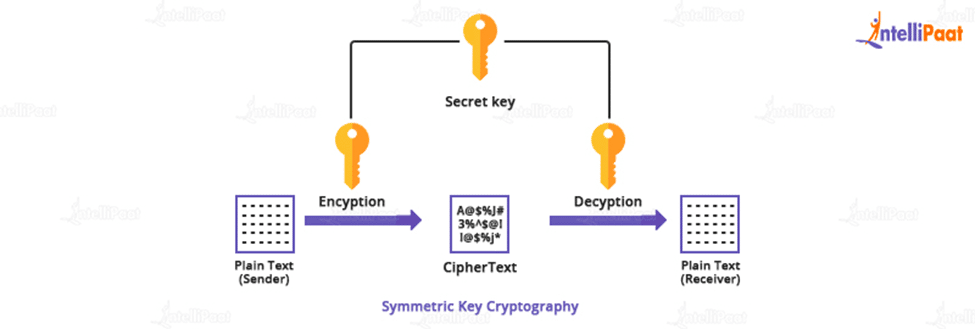
What Is Secret Key Cryptography A Beginner s Guide With Examples

How Public Key Encryption Ensures Data Integrity

How Public Key Encryption Ensures Data Integrity

What Is Secret Key Cryptography A Complete Guide Helenix