In this digital age, when screens dominate our lives The appeal of tangible printed items hasn't gone away. Whether it's for educational purposes for creative projects, simply to add an individual touch to your home, printables for free are now a useful source. For this piece, we'll take a dive deeper into "List Of Symmetric And Asymmetric Encryption Algorithms," exploring what they are, how to locate them, and ways they can help you improve many aspects of your lives.
Get Latest List Of Symmetric And Asymmetric Encryption Algorithms Below

List Of Symmetric And Asymmetric Encryption Algorithms
List Of Symmetric And Asymmetric Encryption Algorithms -
Java ArrayList Java ArrayList ArrayList AbstractList
C C C STL
Printables for free include a vast variety of printable, downloadable items that are available online at no cost. These resources come in many kinds, including worksheets templates, coloring pages, and more. The value of List Of Symmetric And Asymmetric Encryption Algorithms is in their variety and accessibility.
More of List Of Symmetric And Asymmetric Encryption Algorithms
Cryptography CyberSecurity Studio
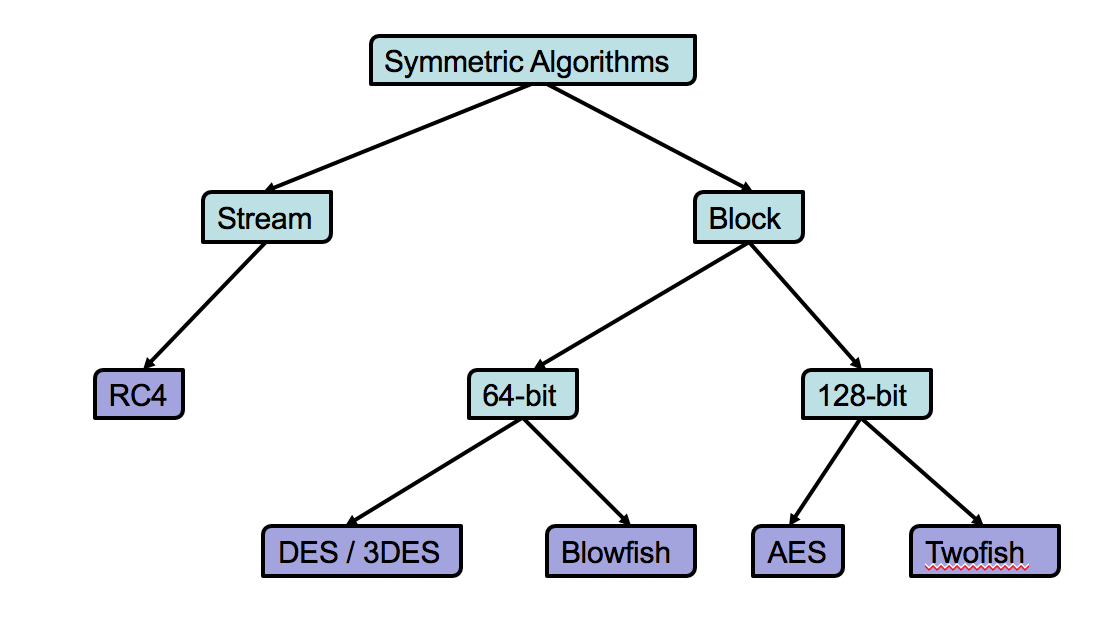
Cryptography CyberSecurity Studio
List sort cmp None key None reverse False cmp key
List append obj 2 list count obj 3 list extend seq 4
The List Of Symmetric And Asymmetric Encryption Algorithms have gained huge popularity because of a number of compelling causes:
-
Cost-Effective: They eliminate the requirement of buying physical copies or expensive software.
-
Personalization We can customize printables to your specific needs, whether it's designing invitations to organize your schedule or even decorating your home.
-
Educational Benefits: Printables for education that are free provide for students of all ages. This makes them a useful source for educators and parents.
-
Convenience: Quick access to an array of designs and templates, which saves time as well as effort.
Where to Find more List Of Symmetric And Asymmetric Encryption Algorithms
Cryptography CyberSecurity Studio
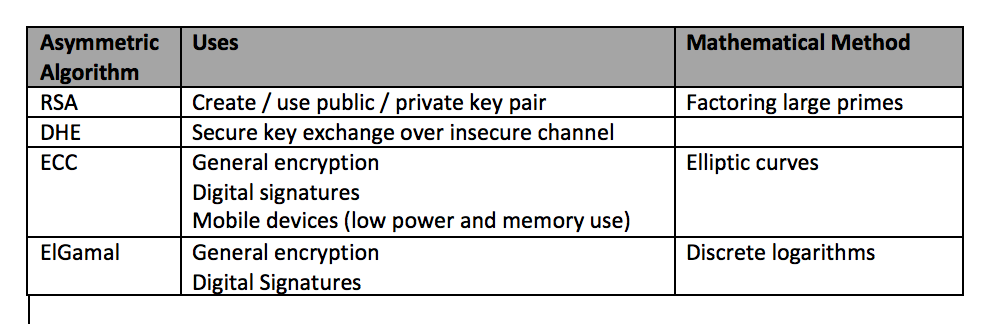
Cryptography CyberSecurity Studio
Python List list Python list
List sort key None reverse False key
After we've peaked your curiosity about List Of Symmetric And Asymmetric Encryption Algorithms We'll take a look around to see where you can find these treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy have a large selection of List Of Symmetric And Asymmetric Encryption Algorithms designed for a variety reasons.
- Explore categories like furniture, education, management, and craft.
2. Educational Platforms
- Educational websites and forums often offer worksheets with printables that are free as well as flashcards and other learning materials.
- Ideal for teachers, parents, and students seeking supplemental resources.
3. Creative Blogs
- Many bloggers are willing to share their original designs as well as templates for free.
- These blogs cover a broad selection of subjects, all the way from DIY projects to party planning.
Maximizing List Of Symmetric And Asymmetric Encryption Algorithms
Here are some unique ways how you could make the most of List Of Symmetric And Asymmetric Encryption Algorithms:
1. Home Decor
- Print and frame gorgeous images, quotes, or seasonal decorations that will adorn your living spaces.
2. Education
- Use printable worksheets for free to reinforce learning at home, or even in the classroom.
3. Event Planning
- Make invitations, banners and decorations for special occasions such as weddings or birthdays.
4. Organization
- Keep your calendars organized by printing printable calendars including to-do checklists, daily lists, and meal planners.
Conclusion
List Of Symmetric And Asymmetric Encryption Algorithms are a treasure trove of practical and innovative resources for a variety of needs and interests. Their availability and versatility make them a valuable addition to each day life. Explore the many options that is List Of Symmetric And Asymmetric Encryption Algorithms today, and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are the printables you get for free gratis?
- Yes you can! You can print and download these materials for free.
-
Can I download free printables in commercial projects?
- It's all dependent on the usage guidelines. Be sure to read the rules of the creator before using any printables on commercial projects.
-
Do you have any copyright issues with printables that are free?
- Certain printables may be subject to restrictions on usage. Check these terms and conditions as set out by the designer.
-
How do I print printables for free?
- You can print them at home with printing equipment or visit any local print store for higher quality prints.
-
What software do I need in order to open List Of Symmetric And Asymmetric Encryption Algorithms?
- The majority of PDF documents are provided in PDF format. They is open with no cost software, such as Adobe Reader.
Cryptography CyberSecurity Studio
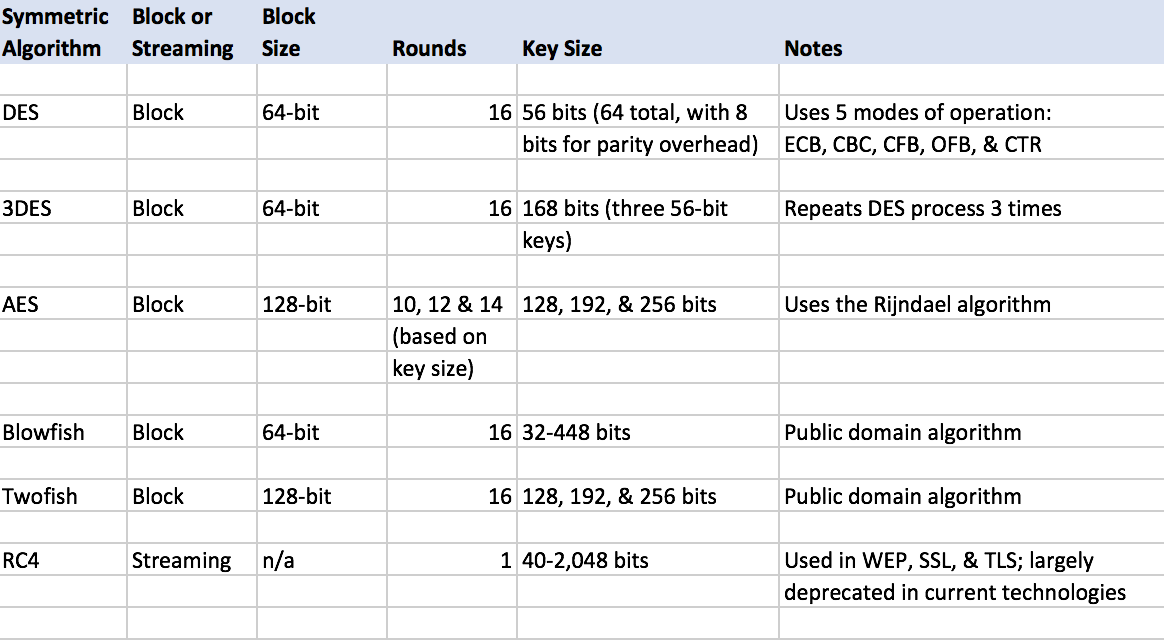
Encryption Internet Security
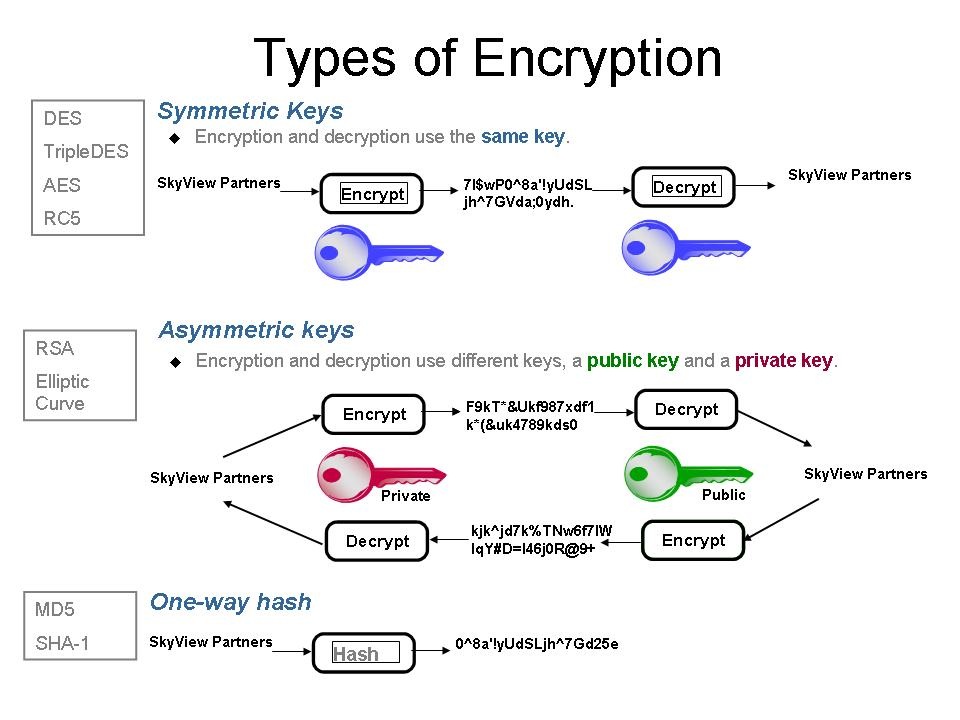
Check more sample of List Of Symmetric And Asymmetric Encryption Algorithms below
Beginners Guide To Cryptography Quick

Encryption And Decryption Jean s Blog

Asymmetric Encryption How Does It Work Applications And Advantages
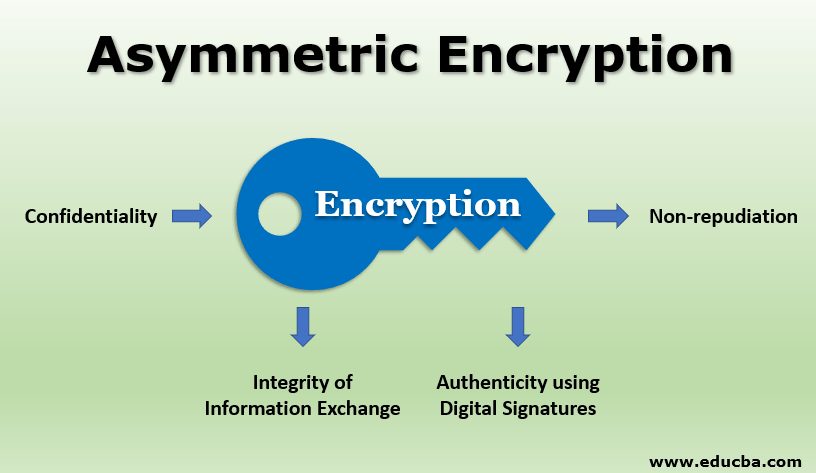
Symmetric And Asymmetric Encryption
Intro To The AES 256 Cipher Boot dev
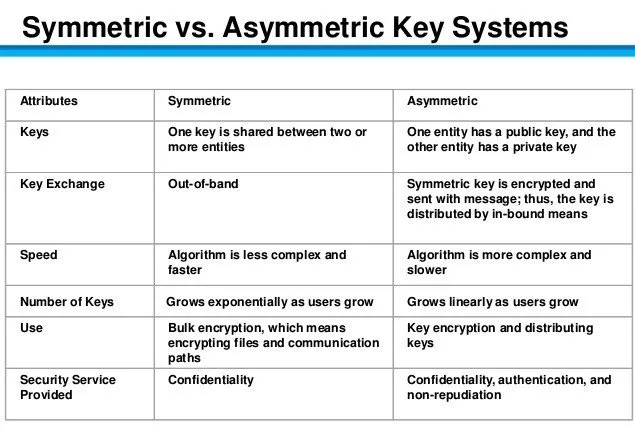
Symmetric And Asymmetric Key Encryption Explained In Plain English
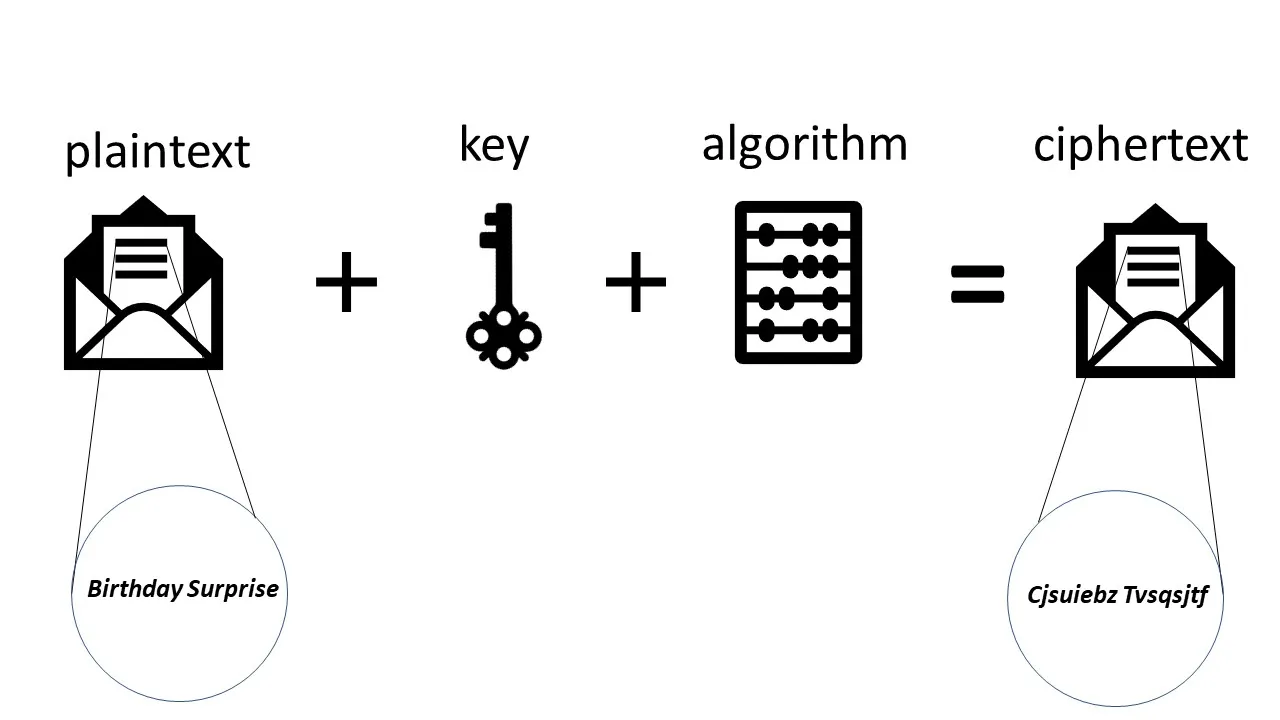


https://www.runoob.com › python-list-slicing.html
My list 2 5 2 5 2 5 5 sub list
C C C STL
My list 2 5 2 5 2 5 5 sub list
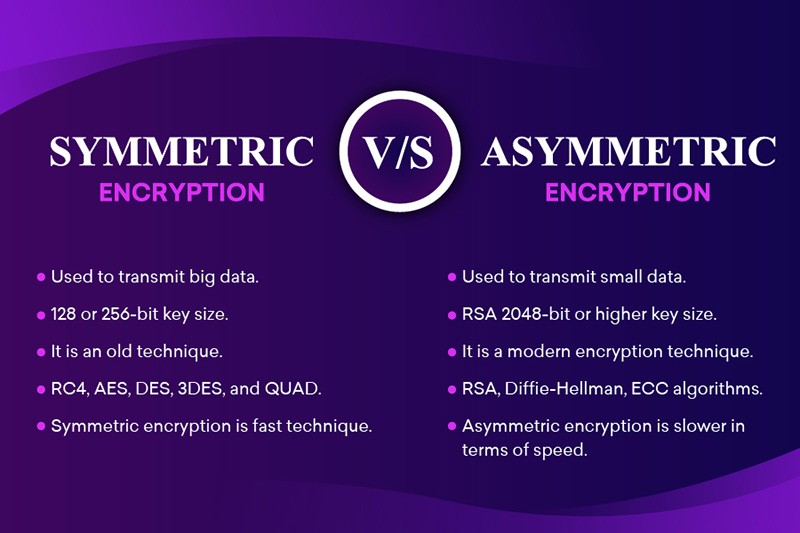
Symmetric And Asymmetric Encryption

Encryption And Decryption Jean s Blog

Intro To The AES 256 Cipher Boot dev

Symmetric And Asymmetric Key Encryption Explained In Plain English

Http Https
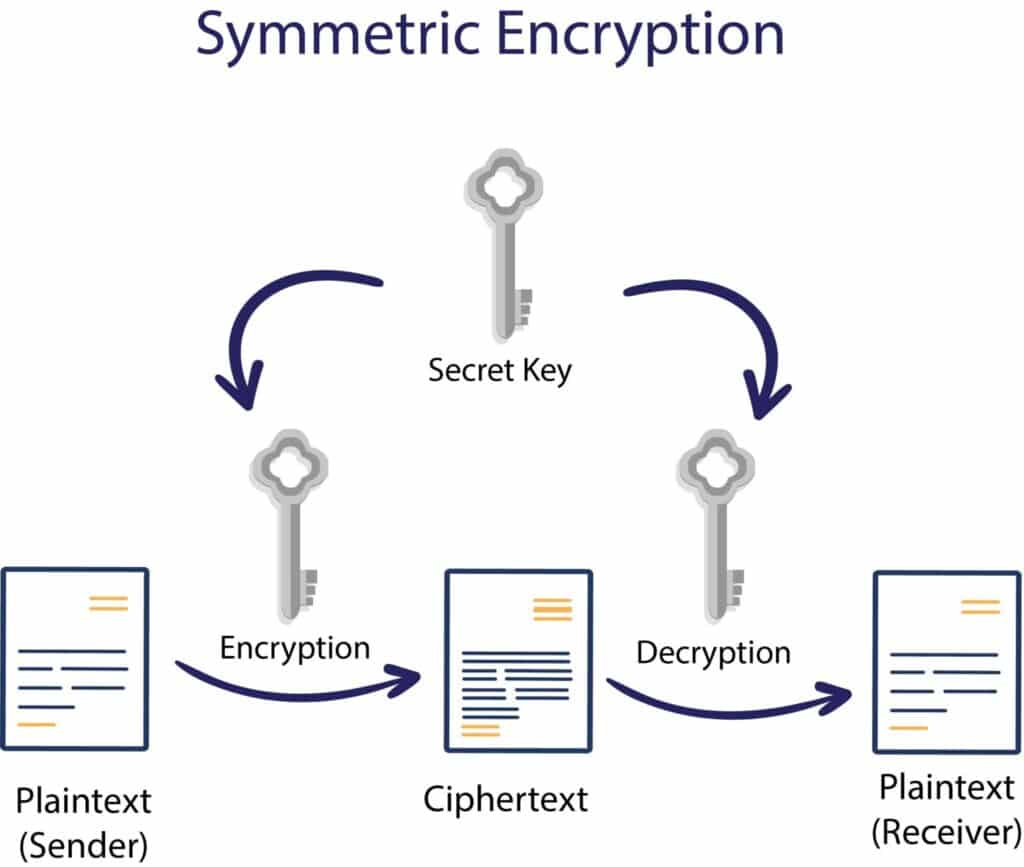
What Is The Role Of Encryption In E Commerce Explain Encryption E

What Is The Role Of Encryption In E Commerce Explain Encryption E

What Is Asymmetric Cryptography Definition From SearchSecurity