In a world where screens dominate our lives The appeal of tangible printed objects isn't diminished. For educational purposes, creative projects, or simply adding some personal flair to your area, How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages are a great source. Here, we'll dive through the vast world of "How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages," exploring what they are, where they can be found, and the ways that they can benefit different aspects of your daily life.
Get Latest How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages Below
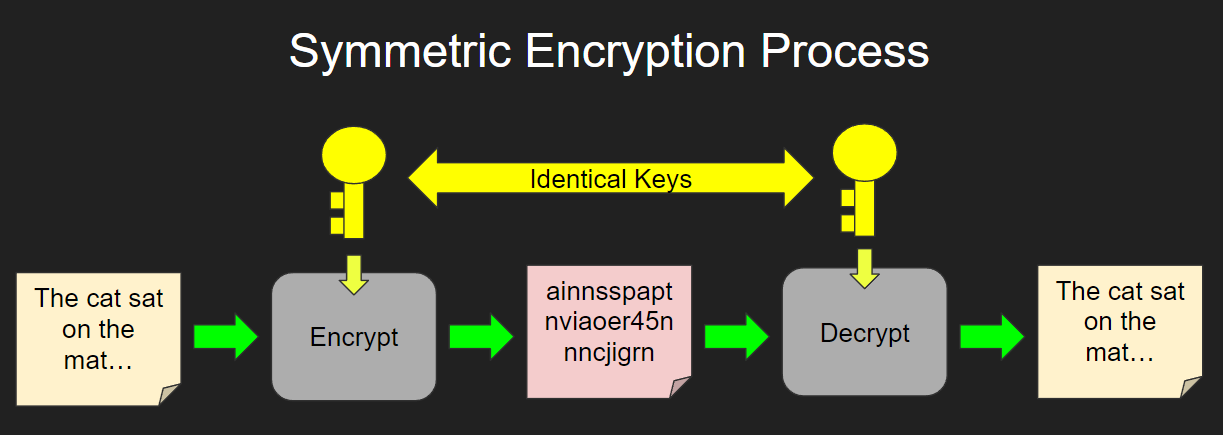
How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages
How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages -
Too many attempts
Many of many for example many students like playing computer games
How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages provide a diverse range of downloadable, printable documents that can be downloaded online at no cost. They are available in a variety of forms, like worksheets templates, coloring pages and many more. The beauty of How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages is their versatility and accessibility.
More of How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages
Encryption Choices Rsa Vs Aes Explained Prey

Encryption Choices Rsa Vs Aes Explained Prey
step step increment increment attempt
Many thanks for coming here It will be highly appreciated if you offer any suggestion 2021 03
Print-friendly freebies have gained tremendous popularity due to numerous compelling reasons:
-
Cost-Efficiency: They eliminate the necessity of purchasing physical copies or costly software.
-
Flexible: Your HTML0 customization options allow you to customize printing templates to your own specific requirements whether you're designing invitations for your guests, organizing your schedule or decorating your home.
-
Educational Value: Printing educational materials for no cost can be used by students of all ages, which makes the perfect aid for parents as well as educators.
-
Accessibility: Access to a variety of designs and templates reduces time and effort.
Where to Find more How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages
An Exploration Of Symmetric Key Cryptography History Working And

An Exploration Of Symmetric Key Cryptography History Working And
They asked a great many questions about England 2 Let s look at the question of security Issue
MacBook Pro Mac mini iMac iMac M4 CPU GPU 8
If we've already piqued your curiosity about How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages Let's take a look at where you can discover these hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy have a large selection of How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages suitable for many needs.
- Explore categories such as interior decor, education, management, and craft.
2. Educational Platforms
- Educational websites and forums frequently offer worksheets with printables that are free with flashcards and other teaching materials.
- Ideal for parents, teachers as well as students searching for supplementary resources.
3. Creative Blogs
- Many bloggers provide their inventive designs or templates for download.
- These blogs cover a wide selection of subjects, that includes DIY projects to party planning.
Maximizing How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages
Here are some inventive ways to make the most of printables for free:
1. Home Decor
- Print and frame gorgeous artwork, quotes, as well as seasonal decorations, to embellish your living spaces.
2. Education
- Use these printable worksheets free of charge to enhance learning at home as well as in the class.
3. Event Planning
- Invitations, banners and decorations for special events such as weddings, birthdays, and other special occasions.
4. Organization
- Keep track of your schedule with printable calendars with to-do lists, planners, and meal planners.
Conclusion
How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages are a treasure trove filled with creative and practical information that can meet the needs of a variety of people and preferences. Their availability and versatility make them an essential part of every aspect of your life, both professional and personal. Explore the endless world of How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages to explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages truly completely free?
- Yes, they are! You can print and download these tools for free.
-
Does it allow me to use free printables for commercial purposes?
- It depends on the specific usage guidelines. Be sure to read the rules of the creator prior to printing printables for commercial projects.
-
Do you have any copyright issues when you download How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages?
- Certain printables could be restricted regarding their use. Be sure to review the terms and condition of use as provided by the designer.
-
How can I print printables for free?
- You can print them at home with either a printer or go to a local print shop for high-quality prints.
-
What program do I need to run printables for free?
- Most printables come in the format of PDF, which can be opened using free programs like Adobe Reader.
What Is Symmetric Key Encryption Advantages And Vulnerabilities

The Ultimate Guide To Symmetric Encryption
Check more sample of How Many Keys Are Used In Symmetric Encryption To Encrypt And Decrypt Messages below
What Is Zero Knowledge Encryption Chainlink Blog
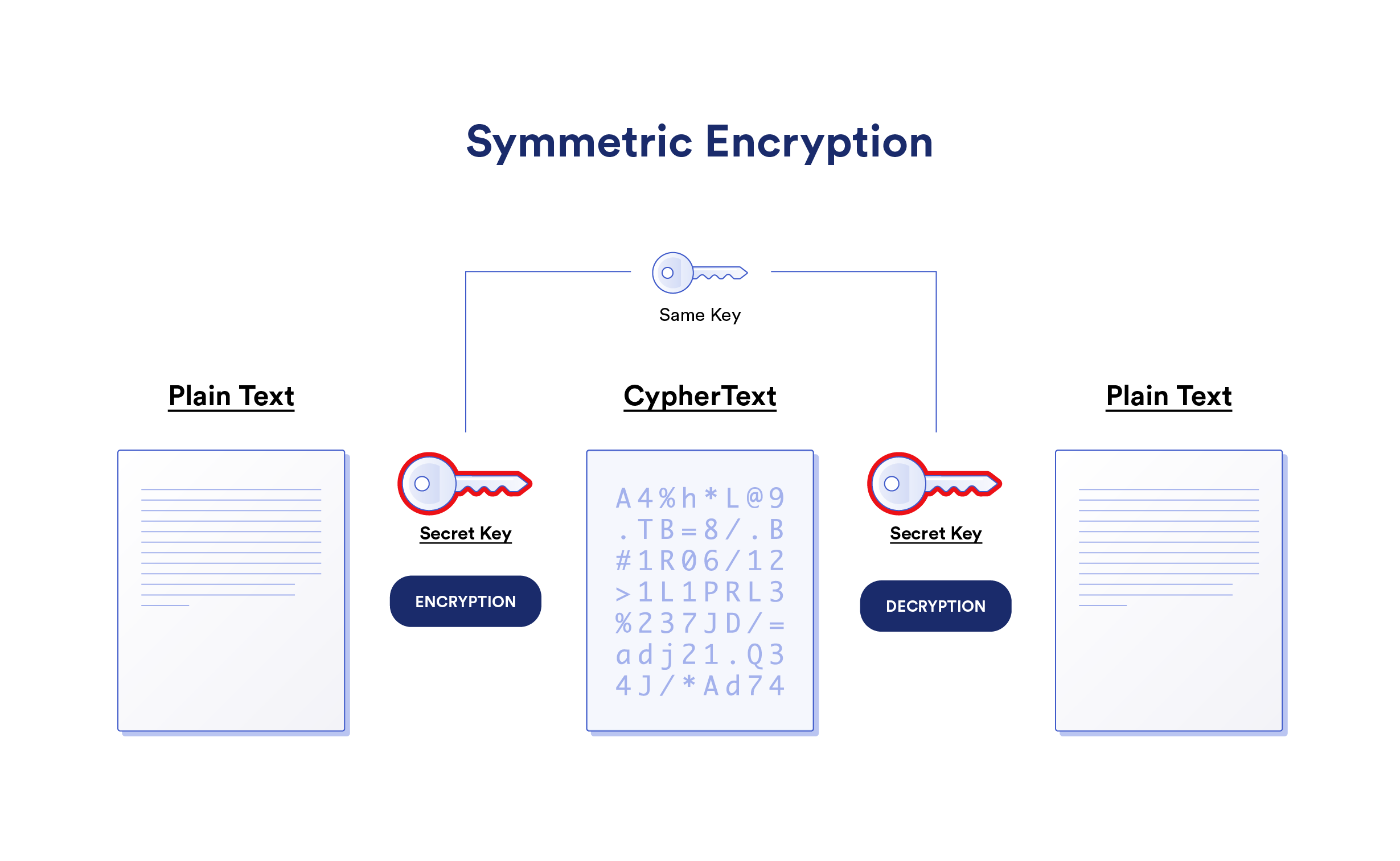
What Is Symmetric Key Cryptography Encryption Security Wiki

How To Reply To Email In Outlook With Teams Meeting Printable Online
Symmetric Vs Asymmetric Encryption Differences Explained

How To Decrypt Encrypted Schematic Calamity

DKIM Twilio

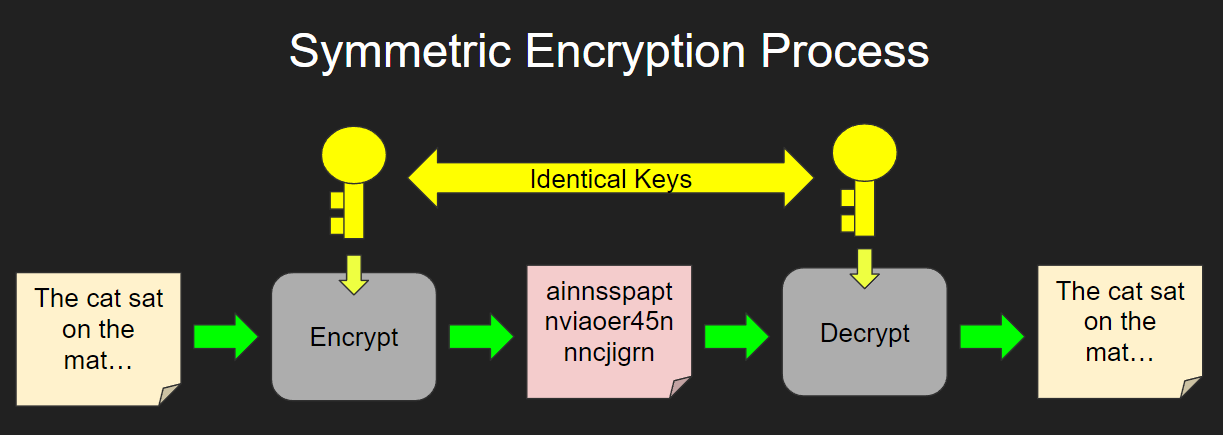
https://www.zhihu.com › question
Many of many for example many students like playing computer games

https://www.zhihu.com › question
error too many attempts made for this increment
Many of many for example many students like playing computer games
error too many attempts made for this increment

Symmetric Vs Asymmetric Encryption Differences Explained

What Is Symmetric Key Cryptography Encryption Security Wiki

How To Decrypt Encrypted Schematic Calamity

DKIM Twilio
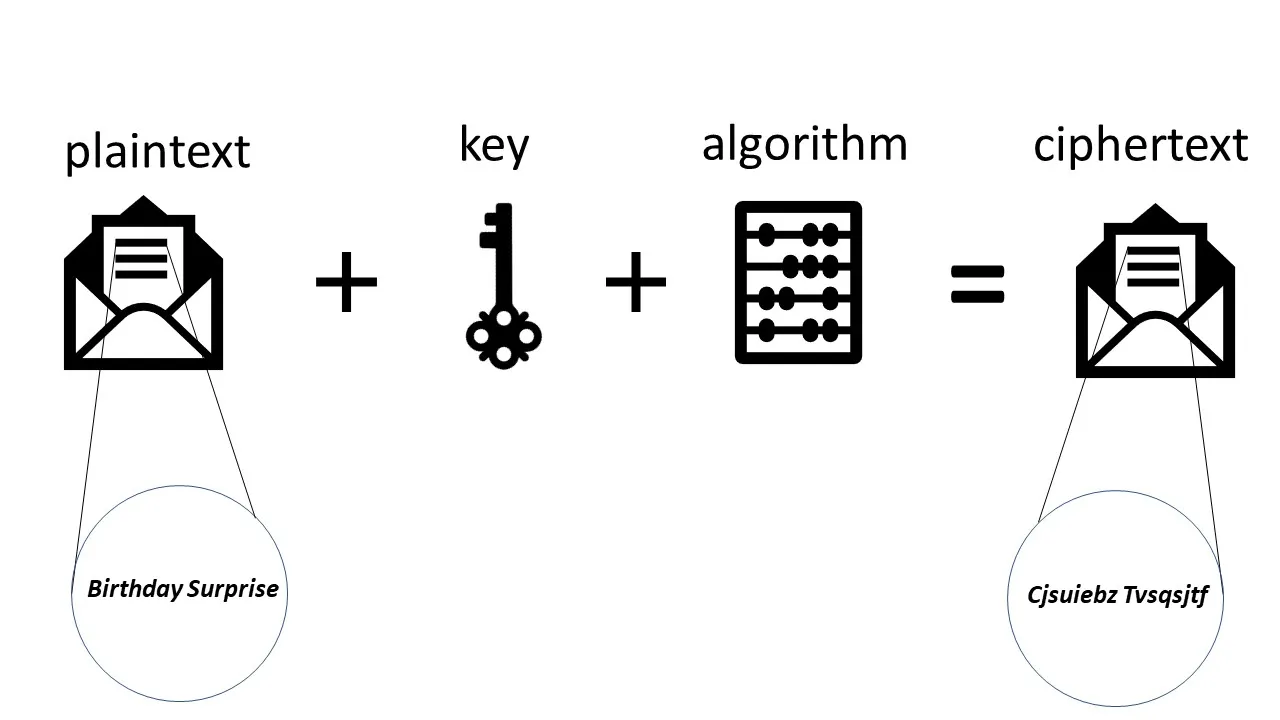
Symmetric And Asymmetric Key Encryption Explained In Plain English
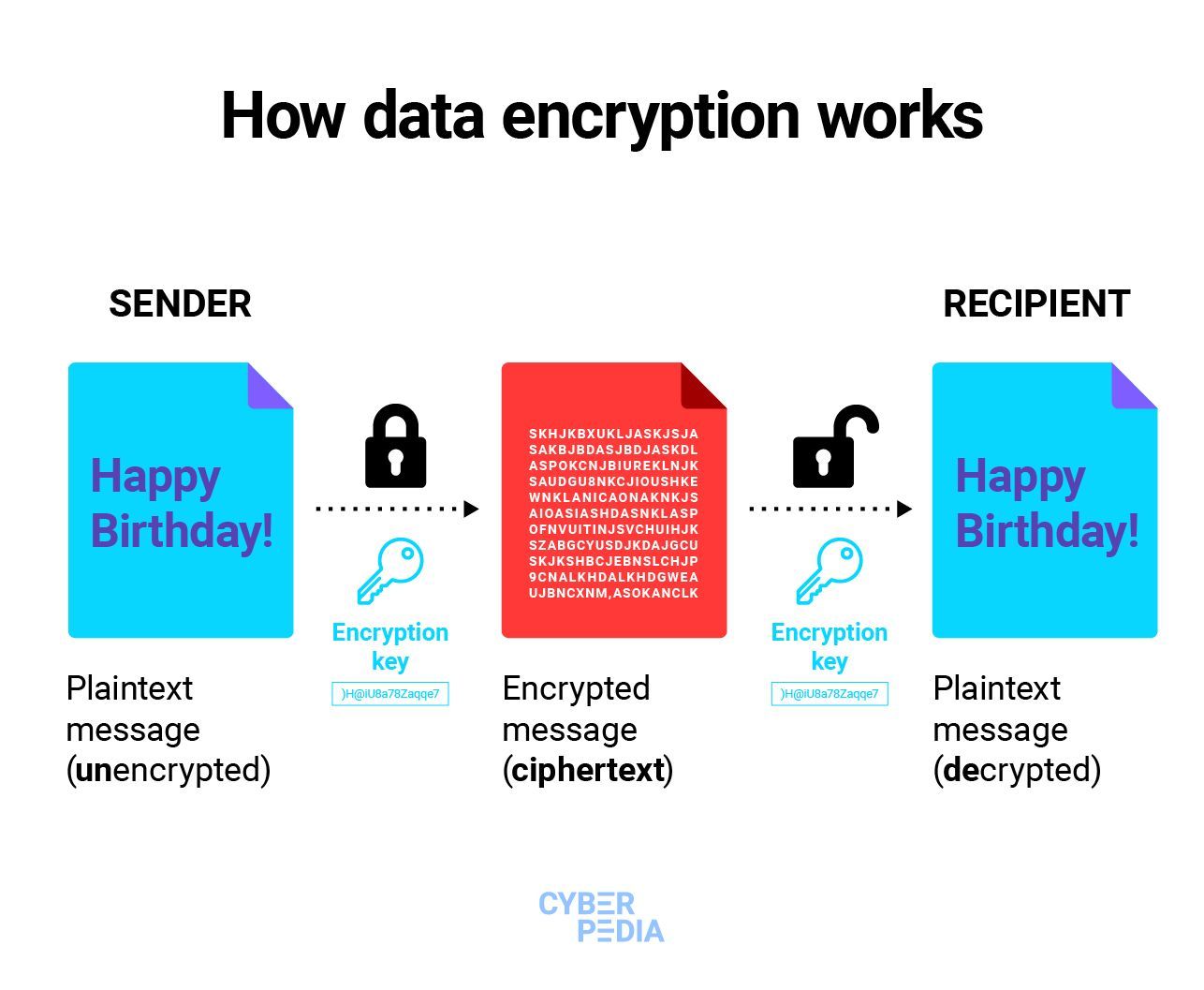
What Is Data Encryption Definition And Best Practices Egnyte The Best

What Is Data Encryption Definition And Best Practices Egnyte The Best
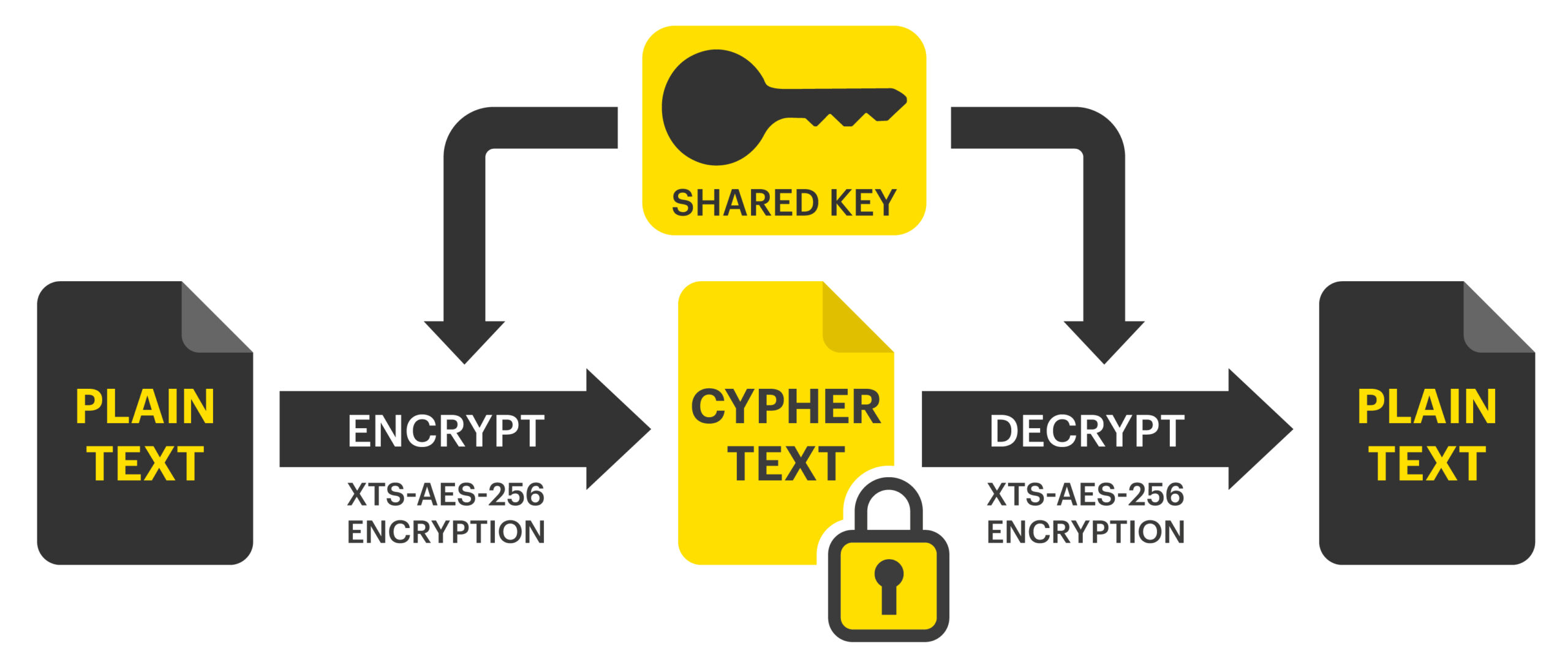
Encryption A Beginner s Guide Start Learning With StorMagic