In this age of electronic devices, where screens dominate our lives yet the appeal of tangible printed objects isn't diminished. Whether it's for educational purposes for creative projects, simply to add an extra personal touch to your home, printables for free have become a valuable resource. With this guide, you'll dive through the vast world of "Cyber Security Risk Management Strategy Example," exploring what they are, how they can be found, and how they can enhance various aspects of your daily life.
Get Latest Cyber Security Risk Management Strategy Example Below

Cyber Security Risk Management Strategy Example
Cyber Security Risk Management Strategy Example -
You can establish a strong cybersecurity posture by understanding your risk profile prioritizing effectively leveraging affordable tools and fostering a culture of security awareness Remember the cybersecurity landscape is
A cyber risk management framework can help organizations effectively assess mitigate and monitor risks and define security processes and procedures to address them Here are several commonly used cyber risk
The Cyber Security Risk Management Strategy Example are a huge range of printable, free materials available online at no cost. The resources are offered in a variety types, like worksheets, templates, coloring pages and much more. The appealingness of Cyber Security Risk Management Strategy Example lies in their versatility and accessibility.
More of Cyber Security Risk Management Strategy Example
Cyber Risk Assessment Template My XXX Hot Girl
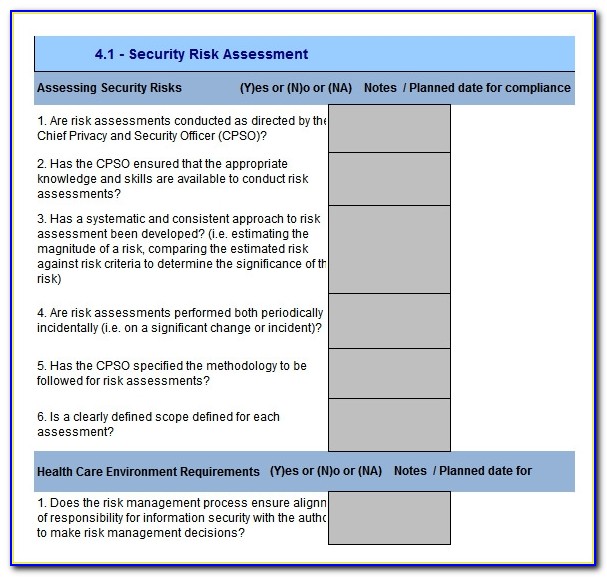
Cyber Risk Assessment Template My XXX Hot Girl
Risk oversight of cybersecurity practices can ensure that the strategy protects the most valuable assets where a breach would pose the greatest potential business damage whether in terms of reputation regulatory
A robust cybersecurity risk management strategy is about managing the effects of uncertainty in a cost effective manner and efficiently using limited resources Ideally risk management helps identify risks early
Printables that are free have gained enormous appeal due to many compelling reasons:
-
Cost-Efficiency: They eliminate the necessity of purchasing physical copies or expensive software.
-
customization We can customize printing templates to your own specific requirements in designing invitations and schedules, or even decorating your house.
-
Educational Benefits: Educational printables that can be downloaded for free are designed to appeal to students from all ages, making them a vital tool for teachers and parents.
-
Easy to use: Instant access to a myriad of designs as well as templates, which saves time as well as effort.
Where to Find more Cyber Security Risk Management Strategy Example
Information Security Risk Management ISO IEC 27001 2017

Information Security Risk Management ISO IEC 27001 2017
A Comprehensive Flexible Risk Based Approach The Risk Management Framework RMF provides a process that integrates security privacy and cyber supply chain risk management activities into the system
Cyber risk management also called cybersecurity risk management is the process of identifying prioritizing managing and monitoring risks to information systems Cyber risk
Now that we've piqued your interest in Cyber Security Risk Management Strategy Example, let's explore where you can find these hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a large collection with Cyber Security Risk Management Strategy Example for all reasons.
- Explore categories such as the home, decor, organizational, and arts and crafts.
2. Educational Platforms
- Educational websites and forums often offer worksheets with printables that are free with flashcards and other teaching materials.
- This is a great resource for parents, teachers and students in need of additional sources.
3. Creative Blogs
- Many bloggers provide their inventive designs and templates for no cost.
- The blogs covered cover a wide range of topics, including DIY projects to party planning.
Maximizing Cyber Security Risk Management Strategy Example
Here are some innovative ways create the maximum value use of printables for free:
1. Home Decor
- Print and frame stunning artwork, quotes or festive decorations to decorate your living areas.
2. Education
- Use these printable worksheets free of charge for reinforcement of learning at home and in class.
3. Event Planning
- Design invitations for banners, invitations and decorations for special events such as weddings, birthdays, and other special occasions.
4. Organization
- Make sure you are organized with printable calendars checklists for tasks, as well as meal planners.
Conclusion
Cyber Security Risk Management Strategy Example are a treasure trove of fun and practical tools that can meet the needs of a variety of people and hobbies. Their access and versatility makes them a wonderful addition to every aspect of your life, both professional and personal. Explore the vast world of Cyber Security Risk Management Strategy Example to open up new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables that are free truly available for download?
- Yes you can! You can print and download these files for free.
-
Does it allow me to use free printables for commercial use?
- It depends on the specific usage guidelines. Always verify the guidelines provided by the creator before utilizing printables for commercial projects.
-
Do you have any copyright concerns when using Cyber Security Risk Management Strategy Example?
- Certain printables might have limitations concerning their use. Check the terms and conditions provided by the author.
-
How can I print Cyber Security Risk Management Strategy Example?
- Print them at home using the printer, or go to an in-store print shop to get superior prints.
-
What program do I need to open printables at no cost?
- A majority of printed materials are with PDF formats, which can be opened with free software such as Adobe Reader.
A Cyber risk Self Assessment That Makes A Difference Waident

The Financial Industry Cyber Security Laggards Risk Management Monitor
Check more sample of Cyber Security Risk Management Strategy Example below
2022 Project Risk Management Plan Template Fillable Printable Pdf Riset
Cybersecurity Wbm Cyber Security

IT Ransomware Protection Mameloo
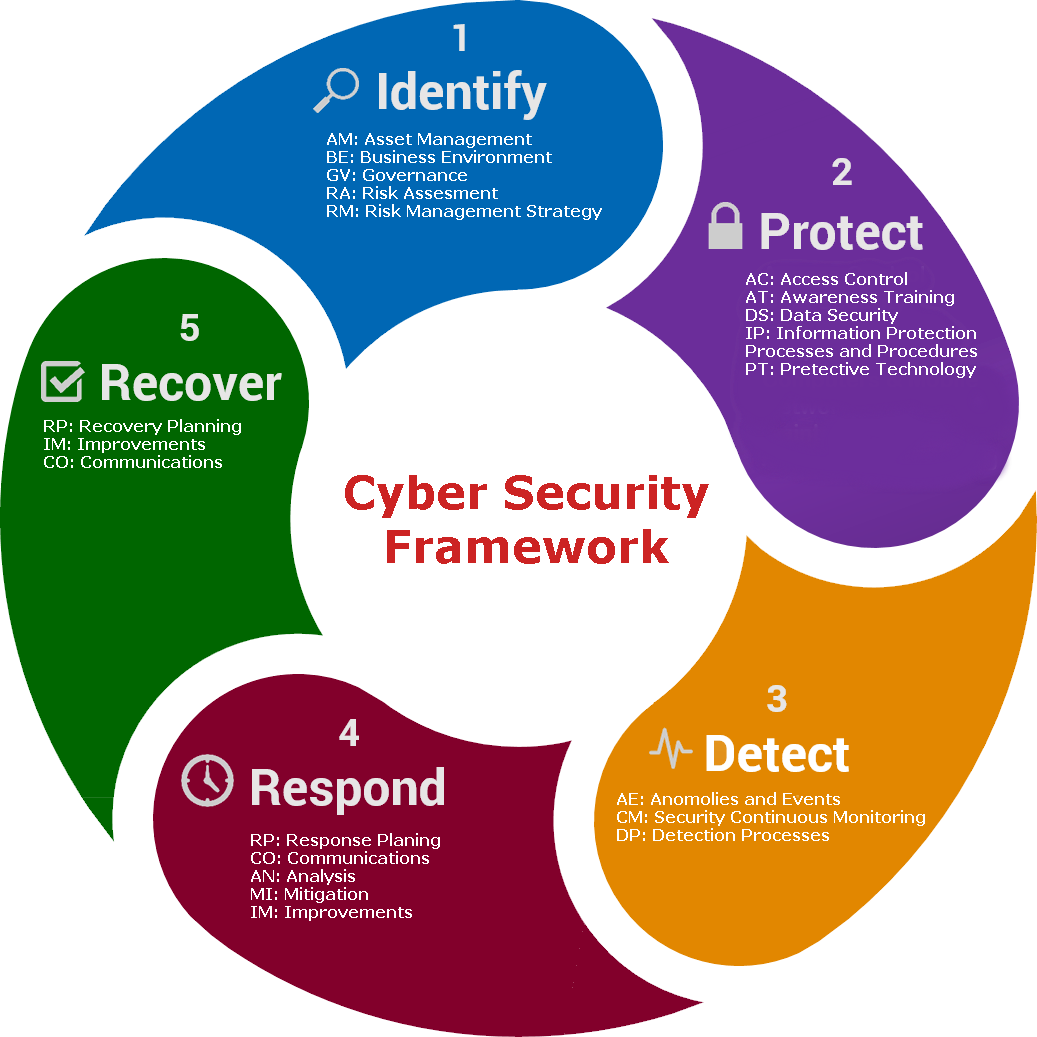
rmf csf cybersecurity Risk Management Cyber Security Awareness

The Importance Of Cybersecurity In The Maritime Industry SHIP IP LTD
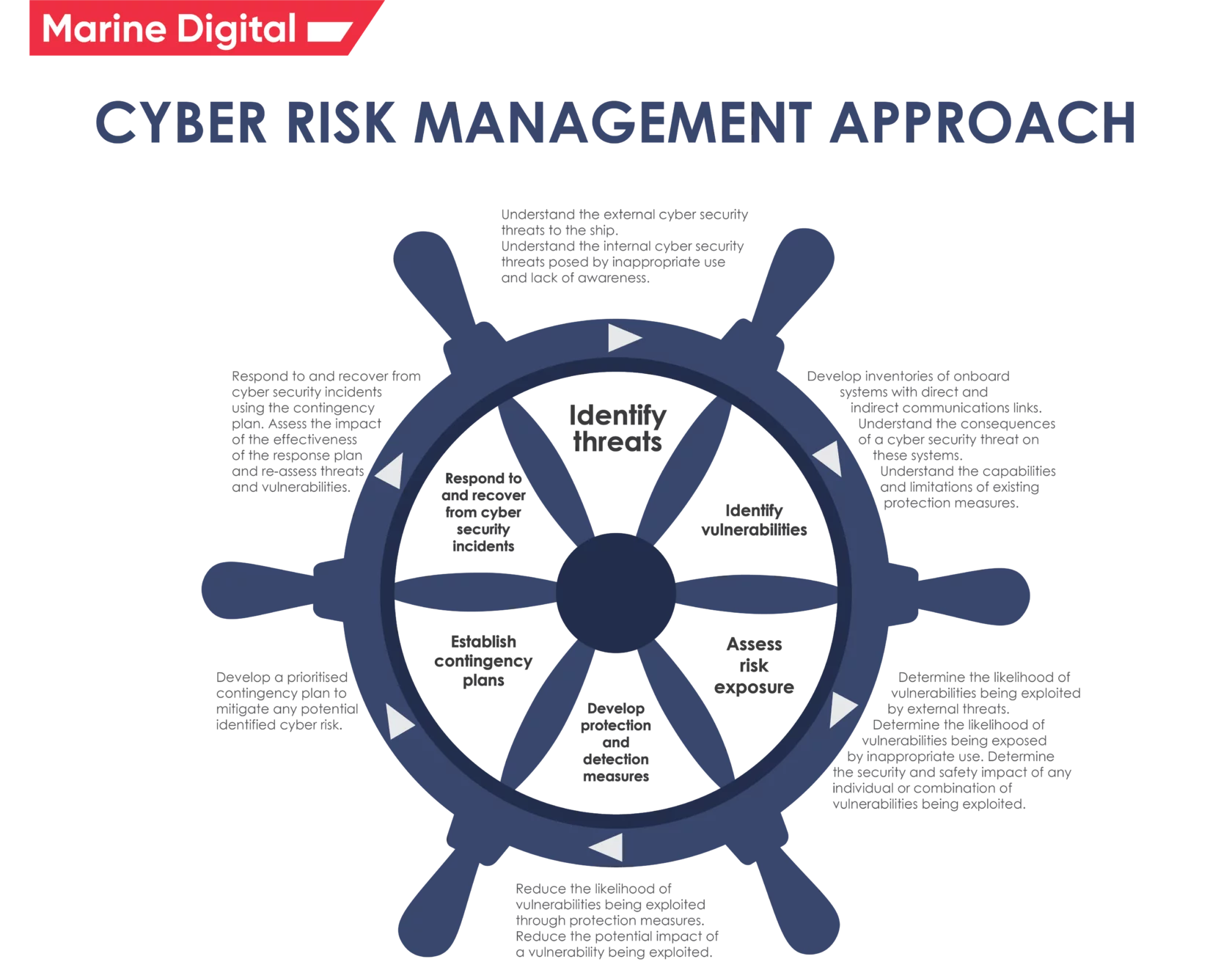
Cybersecurity Risk Management What Is It How To Implement It In 2023
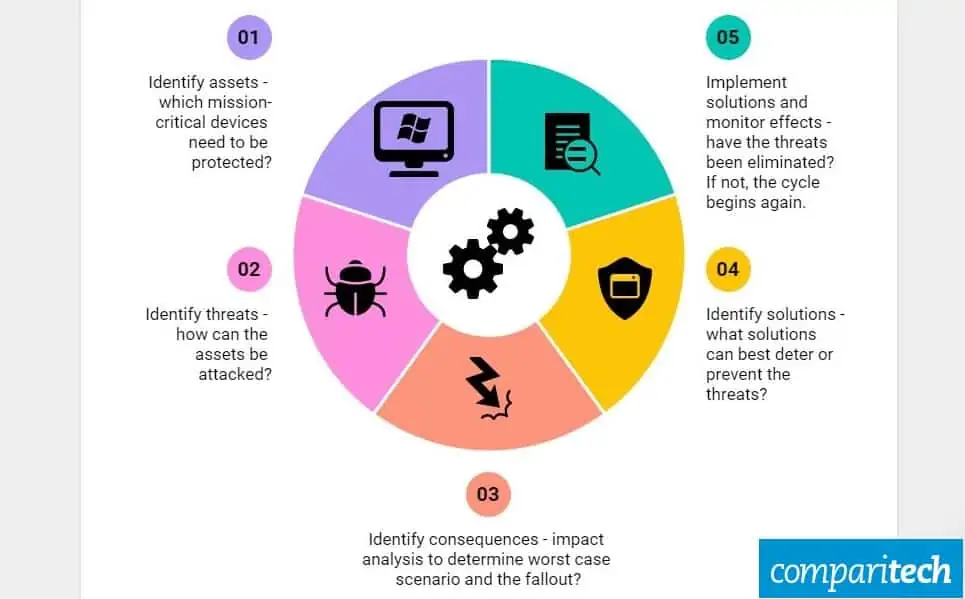

https://www.imperva.com/learn/data-sec…
A cyber risk management framework can help organizations effectively assess mitigate and monitor risks and define security processes and procedures to address them Here are several commonly used cyber risk
https://www.ibm.com/security/digital-assets/...
These assessments can include risk quantification third party security risk identification penetration testing to find weaknesses in one s own systems as well as cyber breach
A cyber risk management framework can help organizations effectively assess mitigate and monitor risks and define security processes and procedures to address them Here are several commonly used cyber risk
These assessments can include risk quantification third party security risk identification penetration testing to find weaknesses in one s own systems as well as cyber breach

rmf csf cybersecurity Risk Management Cyber Security Awareness

Cybersecurity Wbm Cyber Security

The Importance Of Cybersecurity In The Maritime Industry SHIP IP LTD

Cybersecurity Risk Management What Is It How To Implement It In 2023

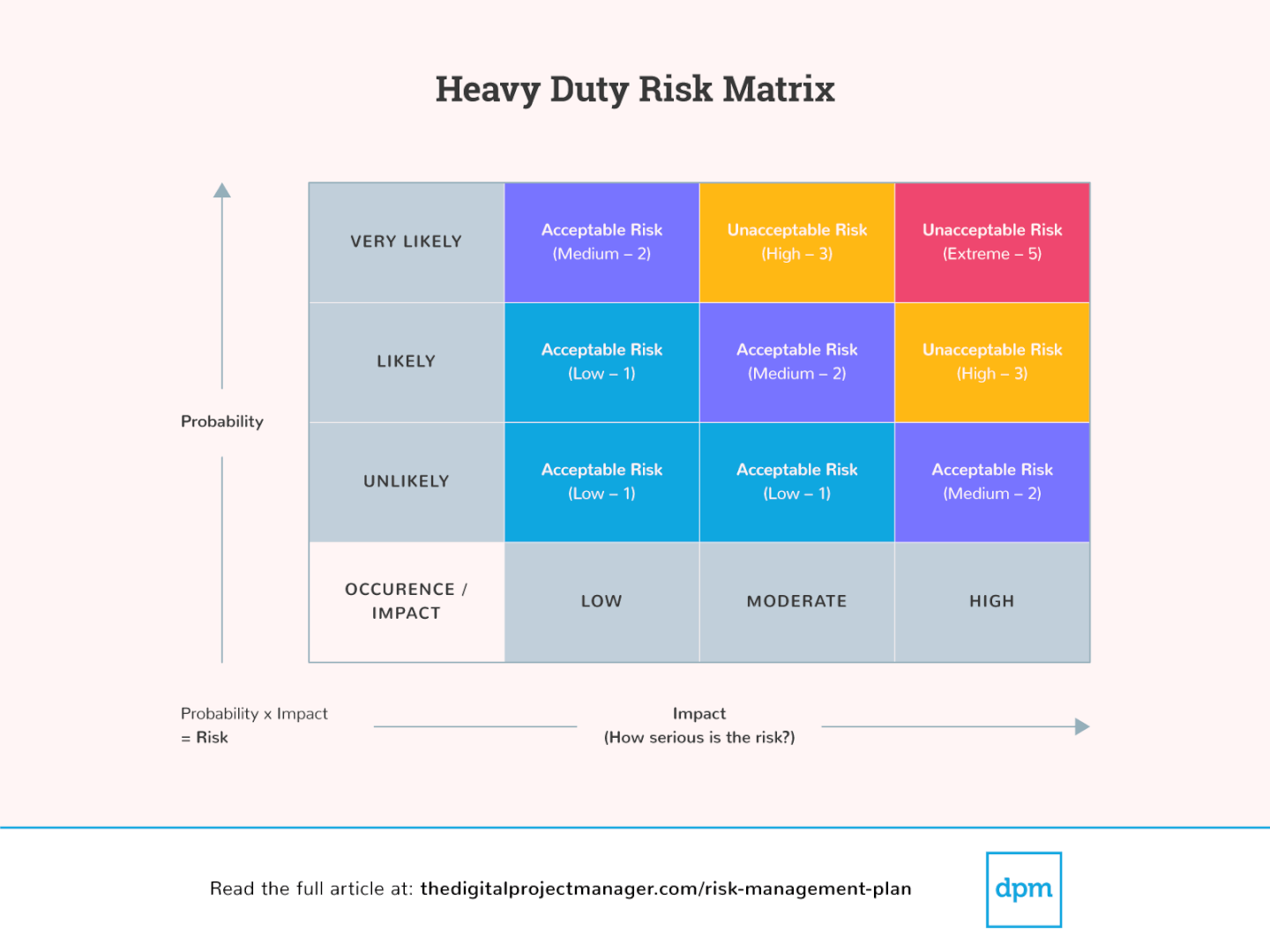
Cyber Security To Manage Risk Matrix247

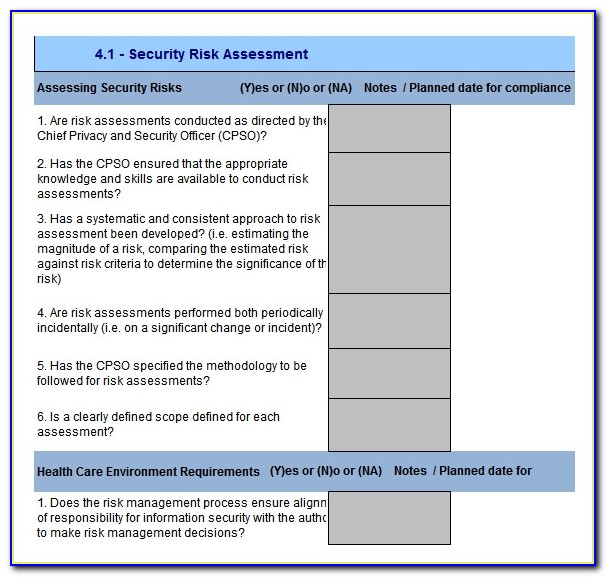
Cyber Security Risk Assessment Report Template Advanced Etical Haking

Cyber Security Risk Assessment Report Template Advanced Etical Haking

Managing Risk Capability In Financial Organizations