In the digital age, with screens dominating our lives but the value of tangible printed products hasn't decreased. In the case of educational materials for creative projects, just adding an element of personalization to your home, printables for free have become a valuable resource. Through this post, we'll dive through the vast world of "Categories Of Security Threats In Cryptography And Network Security," exploring the benefits of them, where to get them, as well as how they can improve various aspects of your daily life.
Get Latest Categories Of Security Threats In Cryptography And Network Security Below

Categories Of Security Threats In Cryptography And Network Security
Categories Of Security Threats In Cryptography And Network Security -
If you use inbox categories find emails under one of the categories category primary category social
Select categories that complete the statement This business IS a rather than this business HAS a The goal is to describe your business holistically rather than a list of all the services it
Categories Of Security Threats In Cryptography And Network Security encompass a wide variety of printable, downloadable items that are available online at no cost. They are available in numerous types, like worksheets, templates, coloring pages, and more. The appealingness of Categories Of Security Threats In Cryptography And Network Security is their versatility and accessibility.
More of Categories Of Security Threats In Cryptography And Network Security
Cryptography And Network Security Scaler Topics

Cryptography And Network Security Scaler Topics
Create an account Tip To use Gmail for your business a Google Workspace account might be better for you than a personal Google Account
Google Sheets supports cell formulas typically found in most desktop spreadsheet packages Functions can be used to create formulas that manipulate data and calculate strings and
Print-friendly freebies have gained tremendous appeal due to many compelling reasons:
-
Cost-Effective: They eliminate the necessity of purchasing physical copies or costly software.
-
Flexible: It is possible to tailor print-ready templates to your specific requirements such as designing invitations planning your schedule or even decorating your house.
-
Educational Worth: Education-related printables at no charge provide for students of all ages. This makes the perfect tool for teachers and parents.
-
It's easy: Fast access many designs and templates will save you time and effort.
Where to Find more Categories Of Security Threats In Cryptography And Network Security
Network Security Threats And Vulnerabilities NordLayer Learn

Network Security Threats And Vulnerabilities NordLayer Learn
In Outlook Use folders rules and categories In Gmail Use labels and search filters Gmail doesn t use folders You can drag messages into labels similar to the way you drag items into
Open Gmail In the search box at the top click Show search options Enter your search criteria If you want to check that your search worked correctly see what emails show up by clicking
We hope we've stimulated your interest in Categories Of Security Threats In Cryptography And Network Security Let's take a look at where they are hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy have a large selection and Categories Of Security Threats In Cryptography And Network Security for a variety needs.
- Explore categories like decorations for the home, education and the arts, and more.
2. Educational Platforms
- Educational websites and forums typically provide worksheets that can be printed for free or flashcards as well as learning materials.
- Perfect for teachers, parents and students looking for additional resources.
3. Creative Blogs
- Many bloggers share their innovative designs and templates for free.
- The blogs are a vast variety of topics, that range from DIY projects to planning a party.
Maximizing Categories Of Security Threats In Cryptography And Network Security
Here are some unique ways that you can make use use of printables that are free:
1. Home Decor
- Print and frame beautiful art, quotes, or festive decorations to decorate your living spaces.
2. Education
- Print out free worksheets and activities to enhance learning at home, or even in the classroom.
3. Event Planning
- Design invitations, banners and decorations for special events such as weddings or birthdays.
4. Organization
- Stay organized with printable calendars or to-do lists. meal planners.
Conclusion
Categories Of Security Threats In Cryptography And Network Security are an abundance of useful and creative resources that can meet the needs of a variety of people and needs and. Their accessibility and versatility make them a fantastic addition to both professional and personal life. Explore the wide world that is Categories Of Security Threats In Cryptography And Network Security today, and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are Categories Of Security Threats In Cryptography And Network Security really free?
- Yes they are! You can print and download these documents for free.
-
Can I use the free printables in commercial projects?
- It depends on the specific conditions of use. Always review the terms of use for the creator prior to printing printables for commercial projects.
-
Do you have any copyright issues with Categories Of Security Threats In Cryptography And Network Security?
- Certain printables could be restricted concerning their use. Make sure to read the terms and regulations provided by the author.
-
How can I print printables for free?
- You can print them at home with a printer or visit the local print shop for superior prints.
-
What software must I use to open printables free of charge?
- Most printables come in the PDF format, and can be opened using free software such as Adobe Reader.
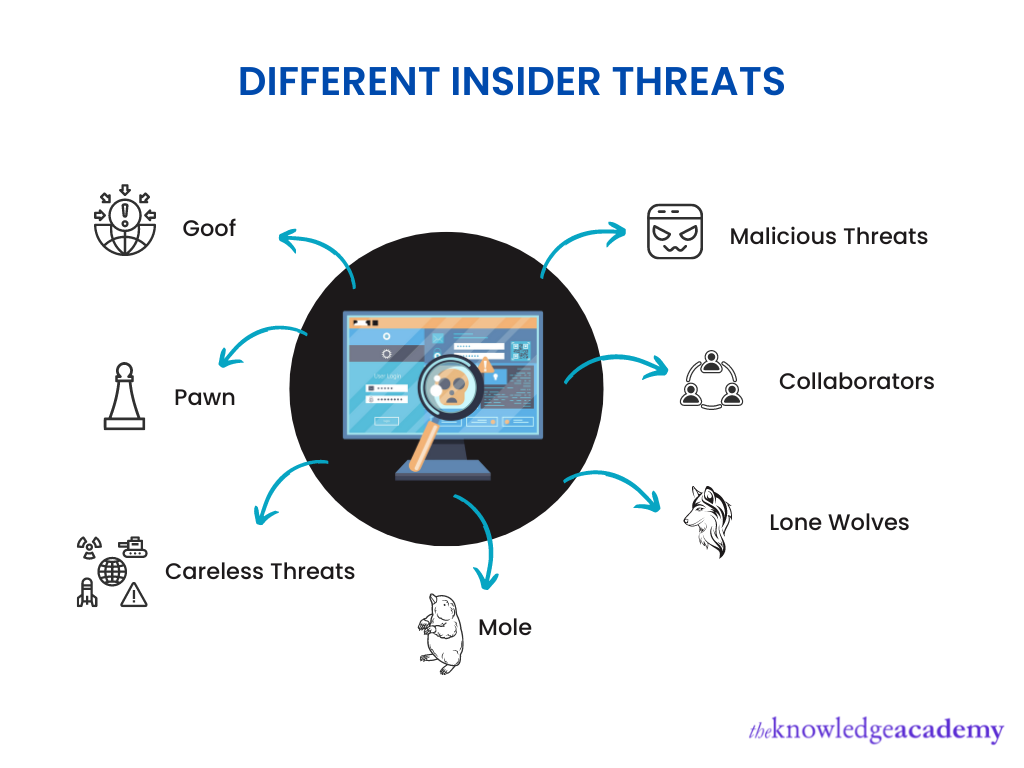
What Is Insider Threats In Cyber Security
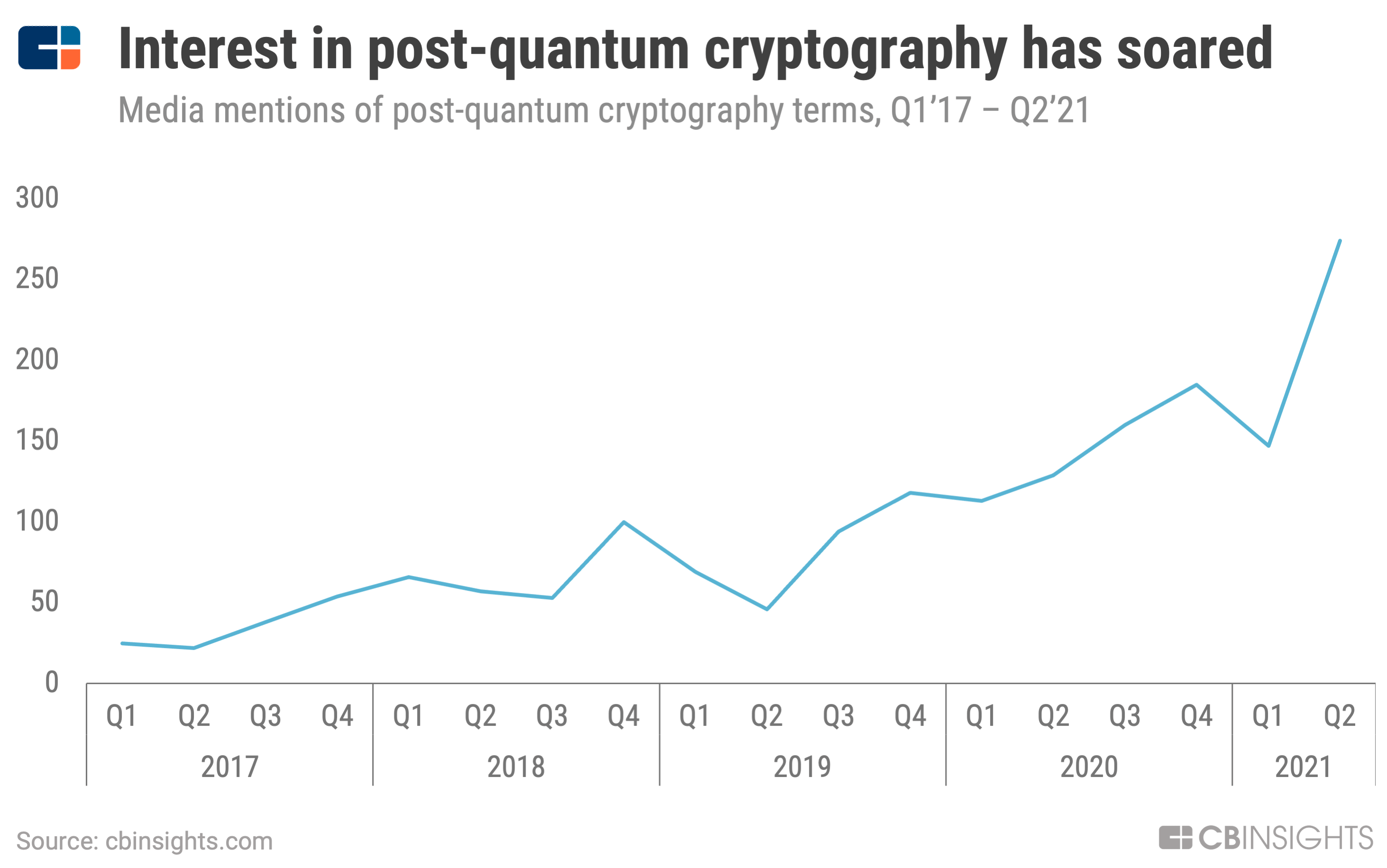
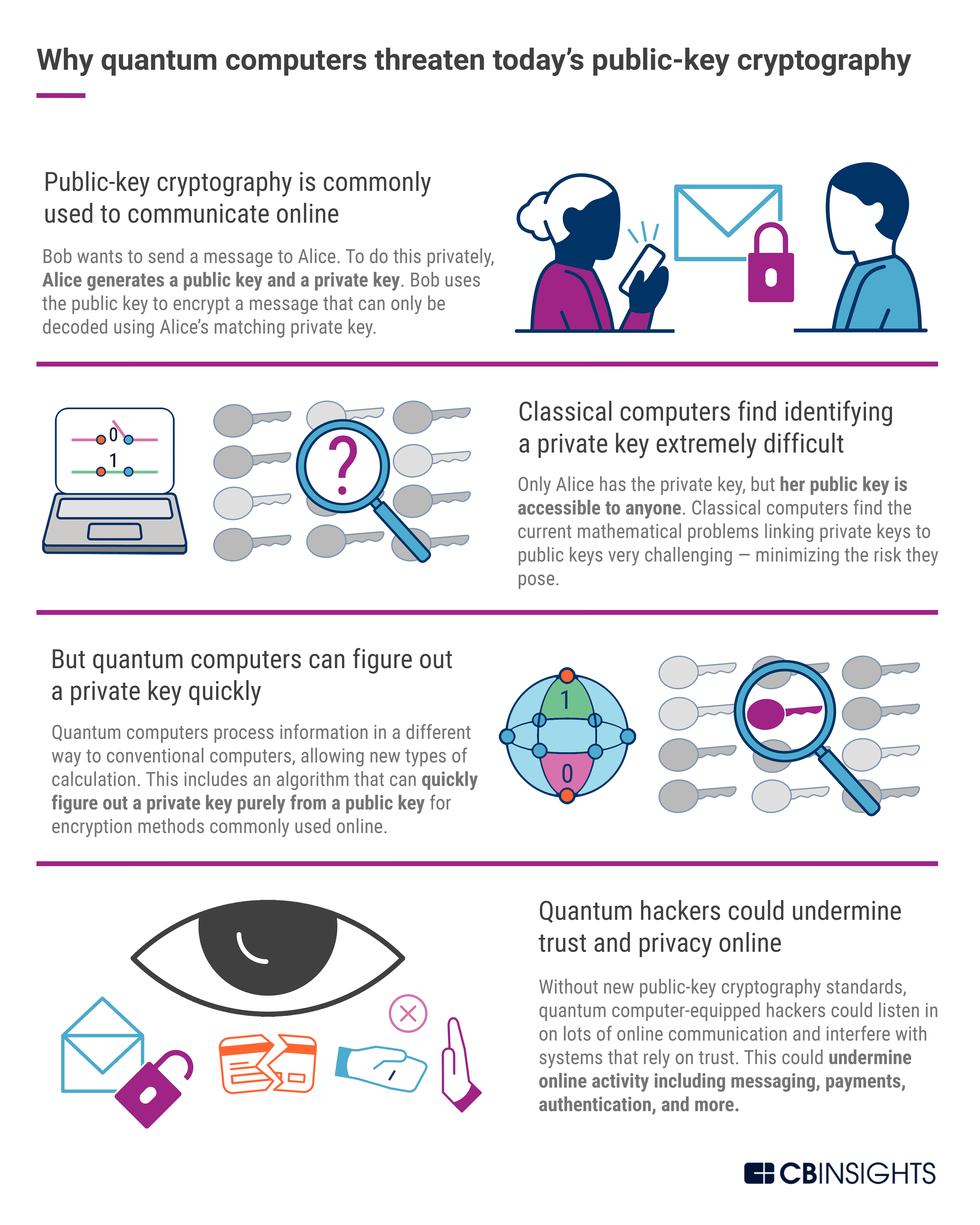
Post Quantum Cryptography A Look At How To Withstand Quantum Computer
Check more sample of Categories Of Security Threats In Cryptography And Network Security below
Post Quantum Cryptography A Look At How To Withstand Quantum Computer
Advantages Disadvantages Of Learning Ethical Hacking
What Is Cryptography Cryptographic Algorithms Types Of

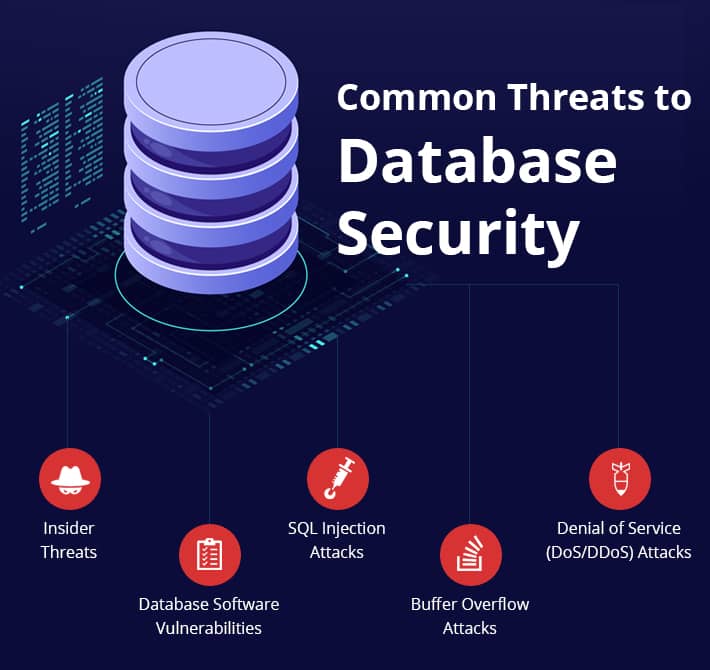
What Is Database Security Common Threats Best Practices
O Que Criptografia E Como Isso Afeta Voc Diariamente TecMundo
10 Most Common Cybersecurity Vulnerabilities CyberGhost VPN

https://support.google.com › business › answer
Select categories that complete the statement This business IS a rather than this business HAS a The goal is to describe your business holistically rather than a list of all the services it

https://support.google.com › merchants › answer
Some product categories such as Apparel Accessories Mobile Phones or Software impose additional required fields If Google incorrectly assigns your product to one of these categories
Select categories that complete the statement This business IS a rather than this business HAS a The goal is to describe your business holistically rather than a list of all the services it
Some product categories such as Apparel Accessories Mobile Phones or Software impose additional required fields If Google incorrectly assigns your product to one of these categories

What Is Database Security Common Threats Best Practices

Advantages Disadvantages Of Learning Ethical Hacking

O Que Criptografia E Como Isso Afeta Voc Diariamente TecMundo
10 Most Common Cybersecurity Vulnerabilities CyberGhost VPN
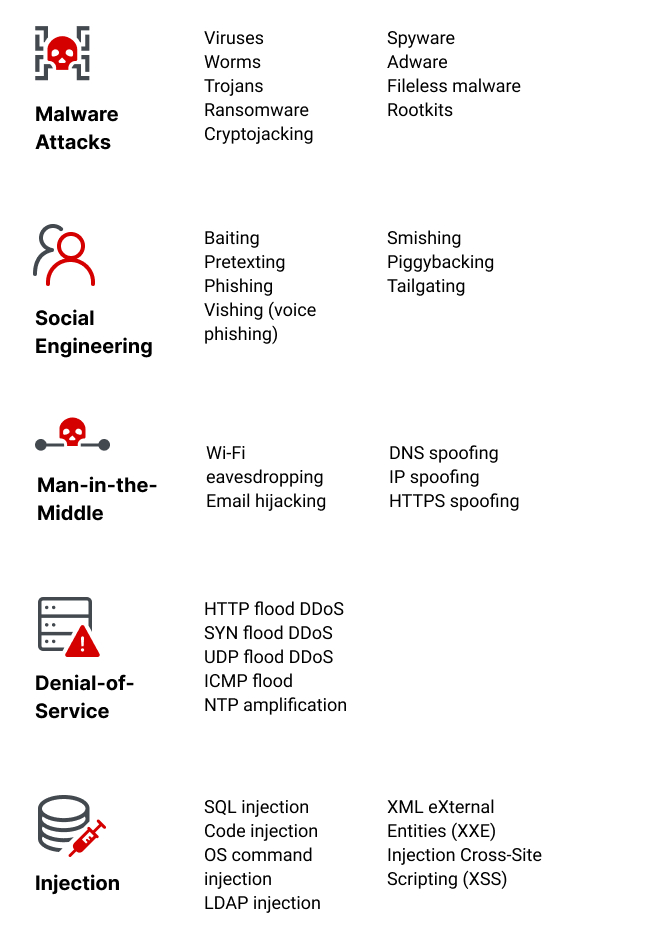
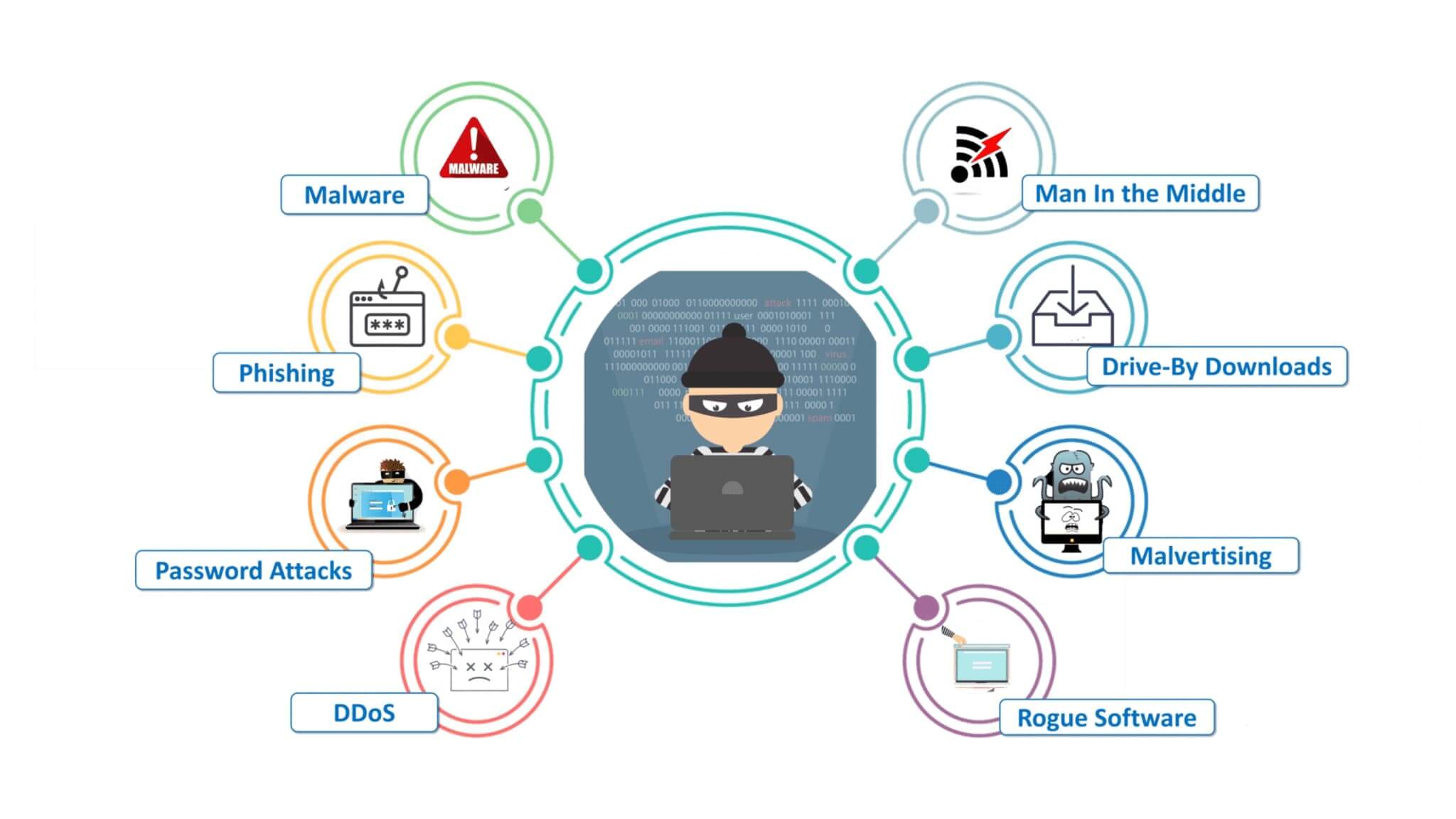
Types Of Cybersecurity Threats
2024 Complete Guide To SHA Encryption Types
2024 Complete Guide To SHA Encryption Types
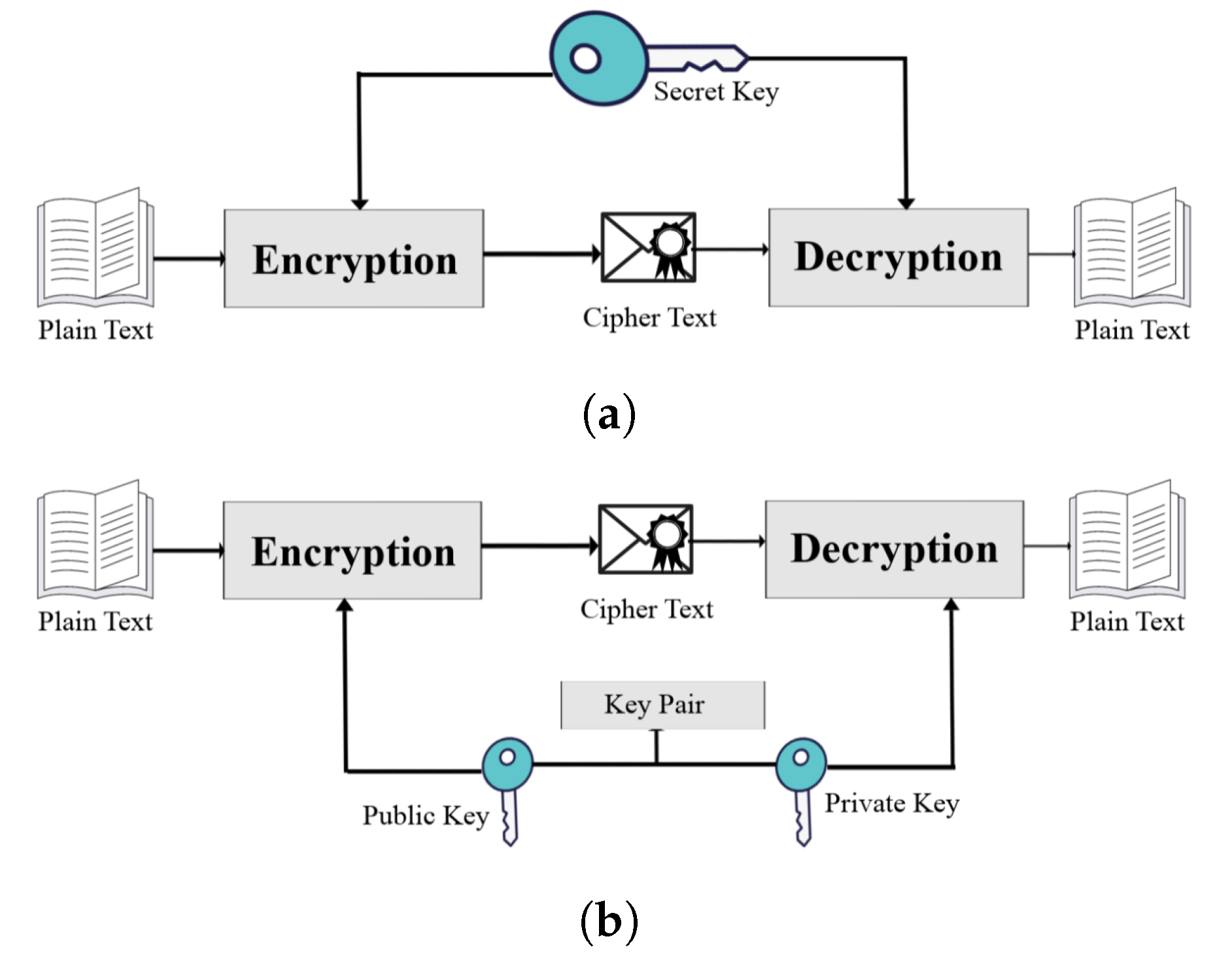
Sensors Free Full Text Resilience Optimization Of Post Quantum