In this day and age where screens dominate our lives The appeal of tangible printed materials hasn't faded away. In the case of educational materials such as creative projects or simply adding an individual touch to the home, printables for free can be an excellent source. This article will dive into the world of "Can Encrypted Data Be Hacked," exploring their purpose, where they can be found, and how they can enrich various aspects of your daily life.
What Are Can Encrypted Data Be Hacked?
Can Encrypted Data Be Hacked cover a large array of printable resources available online for download at no cost. They come in many forms, like worksheets templates, coloring pages, and more. The value of Can Encrypted Data Be Hacked lies in their versatility as well as accessibility.
Can Encrypted Data Be Hacked

Can Encrypted Data Be Hacked
Can Encrypted Data Be Hacked -
[desc-5]
[desc-1]
Can Encrypted Data Be Hacked IT Foundations IT Security Edinburgh

Can Encrypted Data Be Hacked IT Foundations IT Security Edinburgh
[desc-4]
[desc-6]
Can Ransomware Be Removed Cyber Security News Daily
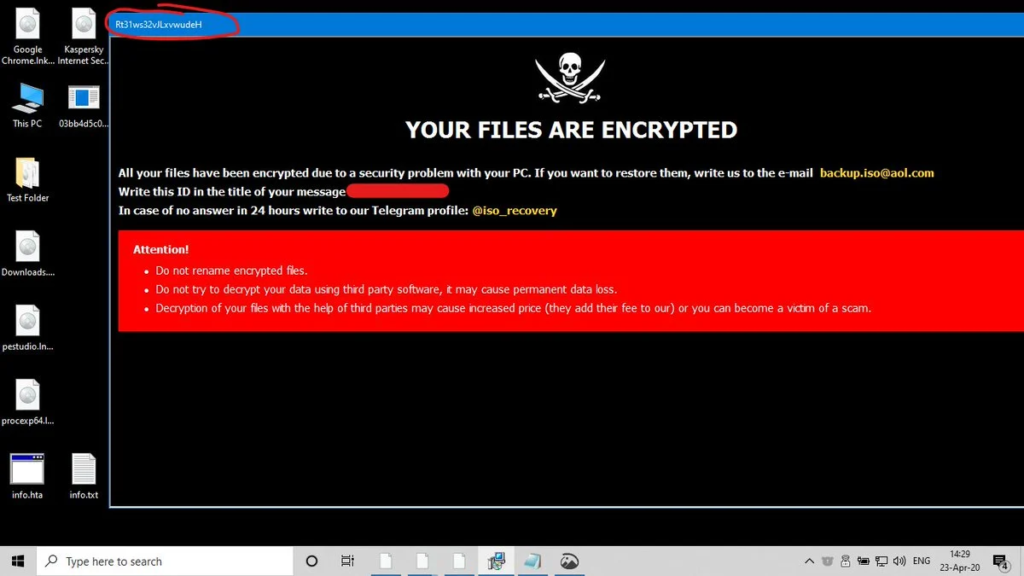
Can Ransomware Be Removed Cyber Security News Daily
[desc-9]
[desc-7]

Can HTML Be Hacked CONQUER CODING
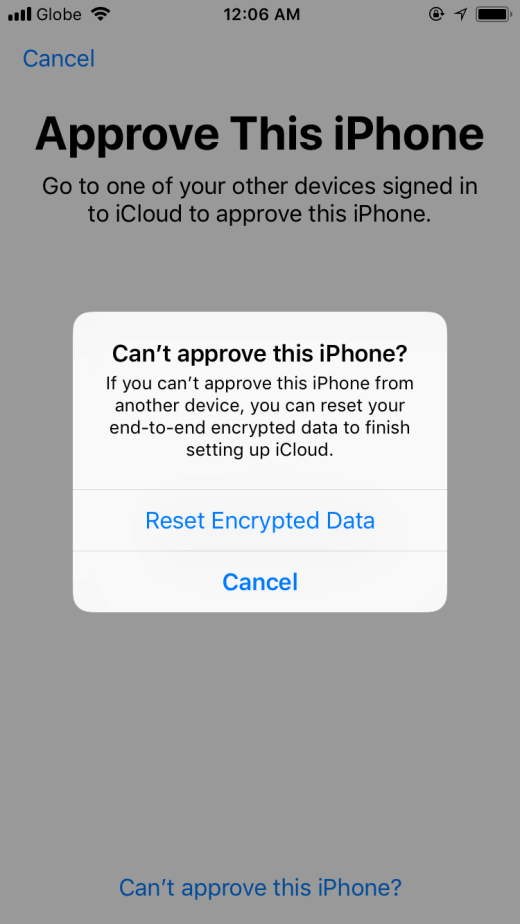
What Happens When Reset End to end Encrypted Data On IPhone Answered
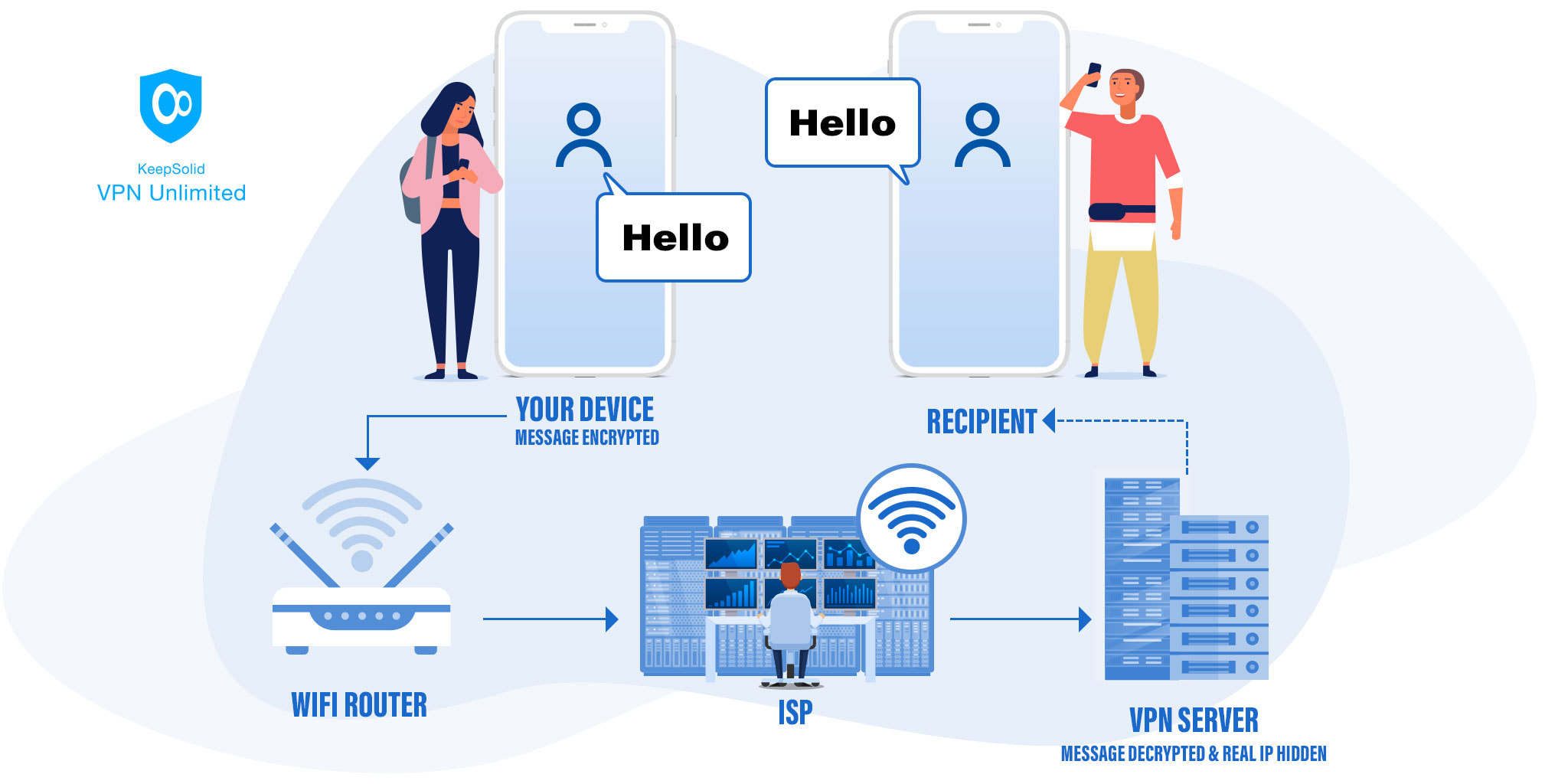
Can VPN And Encrypted Data Be Hacked VPN Unlimited

How Secure Is Your Stolen Encrypted Data Make Tech Easier

Encrypted Traffic Analysis Use Cases Security Challenges ENISA

Texplained EMBEDDED DATA RECOVERY

Texplained EMBEDDED DATA RECOVERY

Can Encrypted Data Be Erased Darwin s Data