In a world when screens dominate our lives yet the appeal of tangible printed materials isn't diminishing. Whether it's for educational purposes or creative projects, or just adding some personal flair to your area, Asymmetric Key Cryptography Examples have become a valuable resource. We'll dive in the world of "Asymmetric Key Cryptography Examples," exploring the different types of printables, where to locate them, and how they can enhance various aspects of your daily life.
Get Latest Asymmetric Key Cryptography Examples Below

Asymmetric Key Cryptography Examples
Asymmetric Key Cryptography Examples -
Cek video bokep terbaru Cewek indonesia di xHamster Tonton semua video XXX terbaru Cewek indonesia sekarang juga
Watch Bokep Indo porn videos for free here on Pornhub Discover the growing collection of high quality Most Relevant XXX movies and clips No other sex tube is more popular and
Asymmetric Key Cryptography Examples encompass a wide variety of printable, downloadable materials available online at no cost. They are available in numerous kinds, including worksheets templates, coloring pages and much more. The value of Asymmetric Key Cryptography Examples is in their versatility and accessibility.
More of Asymmetric Key Cryptography Examples
What Is Asymmetric Encryption Bitpanda Academy

What Is Asymmetric Encryption Bitpanda Academy
Situs Streaming Bokep Indo Terbaru 2025 Kumpulan Bokep Lokal Trending Viral Hanya di BOKEPTOKET COM Update Setiap Hari Gratis Download Ribuan Film Bokep dengan Koleksi
Streaming Video Bokep Terbaru Reset Password Enter the username or e mail you used in your profile A password reset link will be sent to you by email
Printables for free have gained immense popularity because of a number of compelling causes:
-
Cost-Efficiency: They eliminate the need to buy physical copies or costly software.
-
customization It is possible to tailor printing templates to your own specific requirements for invitations, whether that's creating them or arranging your schedule or decorating your home.
-
Educational Value: The free educational worksheets can be used by students of all ages, making the perfect tool for parents and educators.
-
Accessibility: Quick access to the vast array of design and templates will save you time and effort.
Where to Find more Asymmetric Key Cryptography Examples
Role Of Cryptography In Information Security Cloudkul
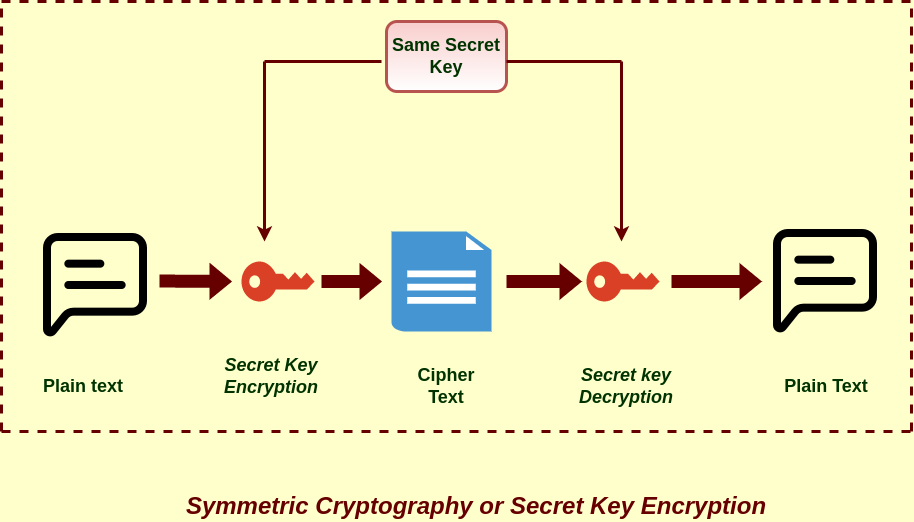
Role Of Cryptography In Information Security Cloudkul
Watch Indonesia Sma porn videos for free here on Pornhub Discover the growing collection of high quality Most Relevant XXX movies and clips No other sex tube is more popular and
Bokep Indo Ngentot Di Malam Malam Kondisi Kosan Sepi 16817 15 Jun 2025 13 13 Bokep Indo Desahan Cewek Putih Cantik Mulus 29637 15 Jun 2025 06 57 Bokep
If we've already piqued your curiosity about Asymmetric Key Cryptography Examples Let's take a look at where the hidden gems:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy offer an extensive collection of Asymmetric Key Cryptography Examples for various purposes.
- Explore categories such as home decor, education, craft, and organization.
2. Educational Platforms
- Forums and educational websites often provide free printable worksheets with flashcards and other teaching tools.
- This is a great resource for parents, teachers as well as students searching for supplementary resources.
3. Creative Blogs
- Many bloggers share their innovative designs with templates and designs for free.
- The blogs covered cover a wide selection of subjects, from DIY projects to party planning.
Maximizing Asymmetric Key Cryptography Examples
Here are some ideas of making the most of printables for free:
1. Home Decor
- Print and frame beautiful art, quotes, or other seasonal decorations to fill your living areas.
2. Education
- Use these printable worksheets free of charge to build your knowledge at home as well as in the class.
3. Event Planning
- Designs invitations, banners and decorations for special events such as weddings or birthdays.
4. Organization
- Make sure you are organized with printable calendars along with lists of tasks, and meal planners.
Conclusion
Asymmetric Key Cryptography Examples are an abundance of useful and creative resources that satisfy a wide range of requirements and preferences. Their access and versatility makes them a great addition to each day life. Explore the wide world that is Asymmetric Key Cryptography Examples today, and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables actually for free?
- Yes, they are! You can print and download these materials for free.
-
Can I make use of free printables in commercial projects?
- It's contingent upon the specific usage guidelines. Always consult the author's guidelines before using their printables for commercial projects.
-
Do you have any copyright problems with Asymmetric Key Cryptography Examples?
- Certain printables could be restricted regarding usage. Make sure you read the conditions and terms of use provided by the creator.
-
How can I print Asymmetric Key Cryptography Examples?
- Print them at home with either a printer or go to a local print shop to purchase superior prints.
-
What software do I need to run printables at no cost?
- The majority of printed documents are in PDF format. These can be opened using free software such as Adobe Reader.
Asymmetric Key Cryptography RSA Encryption Algorithm Asymmetric

Public Key Cryptography Decoded What Is Cryptography Ntirawen

Check more sample of Asymmetric Key Cryptography Examples below
Asymmetric Encryption For Dummies The Signal Chief
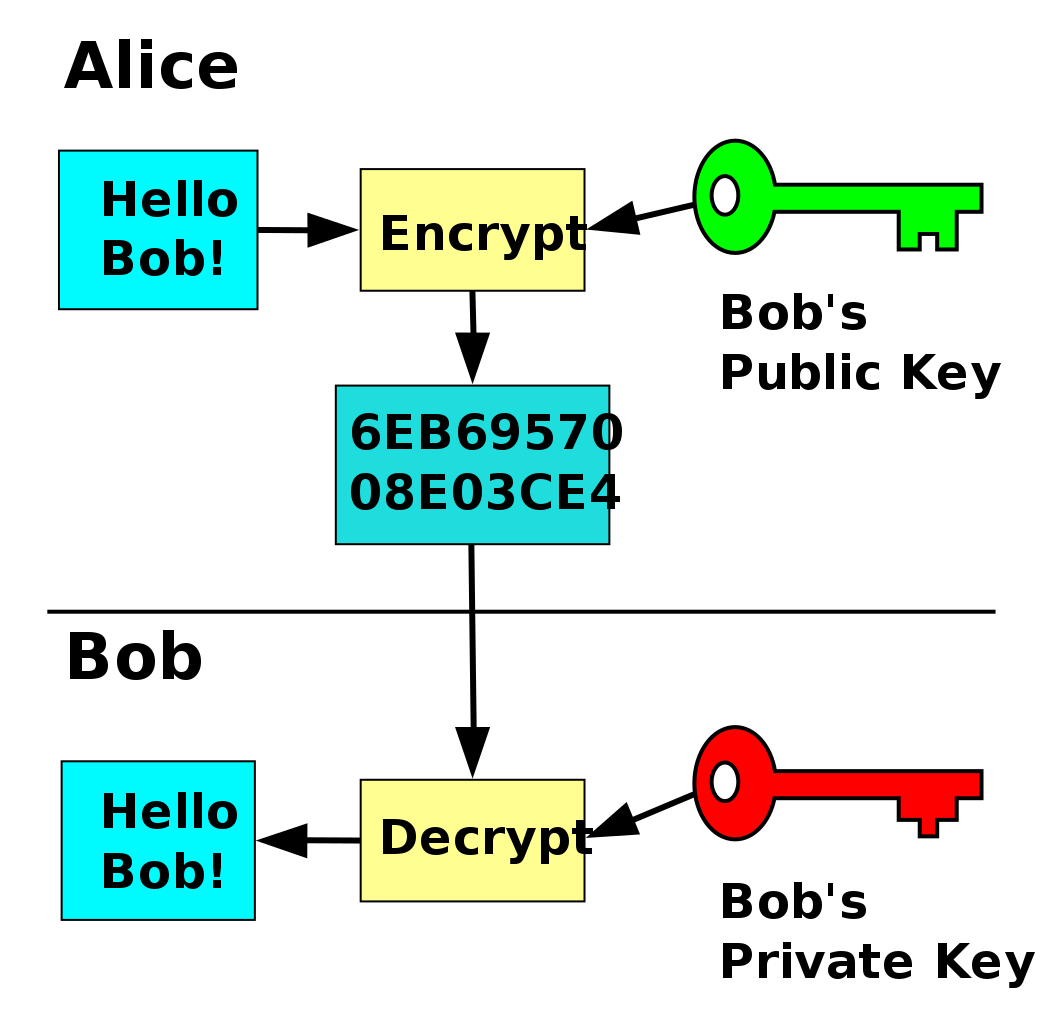
Difference Between Symmetric Asymmetric Key Cryptography Symmetric

Symmetric Vs Asymmetric Encryption Differences Explained

What Is Asymmetric Encryption Babypips

Chirag s Blog Difference Between Symmetric And Asymmetric Key

Asymmetric Encryption How Asymmetric Encryption Works

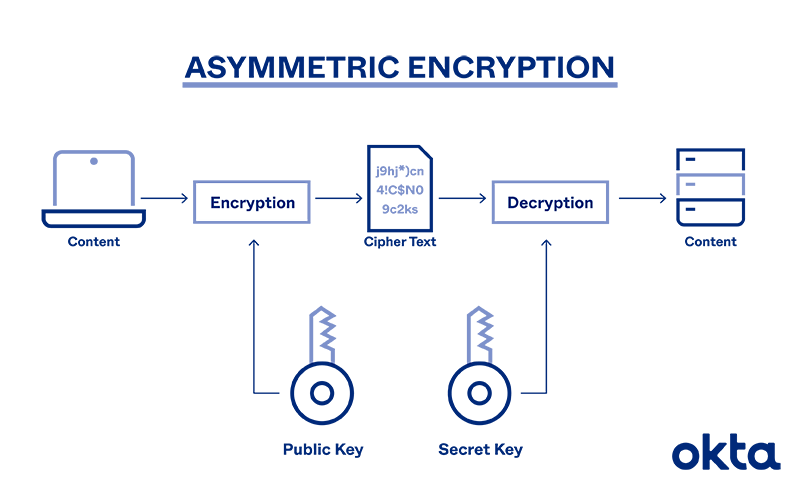
https://www.pornhub.com › video › search
Watch Bokep Indo porn videos for free here on Pornhub Discover the growing collection of high quality Most Relevant XXX movies and clips No other sex tube is more popular and

https://xhamster.com › categories › indonesian
Open Bo Indonesia Indonesian Celebrity Indonesia a country comprised of thousands of islands has the world s fourth highest population with more than 252 million people calling it
Watch Bokep Indo porn videos for free here on Pornhub Discover the growing collection of high quality Most Relevant XXX movies and clips No other sex tube is more popular and
Open Bo Indonesia Indonesian Celebrity Indonesia a country comprised of thousands of islands has the world s fourth highest population with more than 252 million people calling it

What Is Asymmetric Encryption Babypips

Difference Between Symmetric Asymmetric Key Cryptography Symmetric

Chirag s Blog Difference Between Symmetric And Asymmetric Key

Asymmetric Encryption How Asymmetric Encryption Works

Public Key Cryptography Basics Site Reliability Engineering

A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

A Practical Guide To Asymmetric Encryption Part 1 Krupesh Anadkat

What Is Symmetric Key Cryptography Encryption Security Wiki