Today, with screens dominating our lives and the appeal of physical, printed materials hasn't diminished. In the case of educational materials and creative work, or just adding an extra personal touch to your home, printables for free are now a useful source. Through this post, we'll dive deep into the realm of "Asymmetric Key Cryptography Example," exploring the benefits of them, where they are available, and ways they can help you improve many aspects of your daily life.
Get Latest Asymmetric Key Cryptography Example Below

Asymmetric Key Cryptography Example
Asymmetric Key Cryptography Example -
Gen4 Asymmetric Link Gen4 Gen2 Gen3
Asymmetric Convolution Inception V3 3 3 3 1 1 3
The Asymmetric Key Cryptography Example are a huge array of printable items that are available online at no cost. The resources are offered in a variety designs, including worksheets templates, coloring pages, and many more. One of the advantages of Asymmetric Key Cryptography Example is their versatility and accessibility.
More of Asymmetric Key Cryptography Example
How To Decrypt Encrypted Schematic Calamity

How To Decrypt Encrypted Schematic Calamity
fermion asymmetric asymmetric operation spin
2011 1
Print-friendly freebies have gained tremendous recognition for a variety of compelling motives:
-
Cost-Efficiency: They eliminate the requirement of buying physical copies of the software or expensive hardware.
-
Personalization They can make printing templates to your own specific requirements be it designing invitations for your guests, organizing your schedule or decorating your home.
-
Educational Impact: Printing educational materials for no cost offer a wide range of educational content for learners of all ages, which makes them a great source for educators and parents.
-
Convenience: instant access many designs and templates, which saves time as well as effort.
Where to Find more Asymmetric Key Cryptography Example
Asymmetric Key Cryptography YouTube

Asymmetric Key Cryptography YouTube
[desc-9]
EAGLE F1 ASYMMETRIC 5
After we've peaked your curiosity about Asymmetric Key Cryptography Example We'll take a look around to see where the hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy offer a huge selection and Asymmetric Key Cryptography Example for a variety uses.
- Explore categories such as decoration for your home, education, organization, and crafts.
2. Educational Platforms
- Educational websites and forums frequently offer free worksheets and worksheets for printing for flashcards, lessons, and worksheets. tools.
- Ideal for parents, teachers and students looking for additional resources.
3. Creative Blogs
- Many bloggers share their imaginative designs and templates for free.
- These blogs cover a broad range of interests, ranging from DIY projects to party planning.
Maximizing Asymmetric Key Cryptography Example
Here are some ways how you could make the most of Asymmetric Key Cryptography Example:
1. Home Decor
- Print and frame gorgeous images, quotes, or seasonal decorations that will adorn your living spaces.
2. Education
- Use free printable worksheets for reinforcement of learning at home for the classroom.
3. Event Planning
- Design invitations and banners and other decorations for special occasions like weddings or birthdays.
4. Organization
- Keep track of your schedule with printable calendars, to-do lists, and meal planners.
Conclusion
Asymmetric Key Cryptography Example are a treasure trove of practical and imaginative resources catering to different needs and passions. Their accessibility and flexibility make them a fantastic addition to the professional and personal lives of both. Explore the vast array of Asymmetric Key Cryptography Example and uncover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables actually completely free?
- Yes, they are! You can download and print the resources for free.
-
Can I utilize free templates for commercial use?
- It's based on the usage guidelines. Always verify the guidelines of the creator prior to using the printables in commercial projects.
-
Do you have any copyright rights issues with Asymmetric Key Cryptography Example?
- Some printables may have restrictions in their usage. Always read the terms and conditions provided by the author.
-
How can I print Asymmetric Key Cryptography Example?
- You can print them at home using either a printer at home or in any local print store for superior prints.
-
What program will I need to access printables free of charge?
- The majority are printed as PDF files, which can be opened using free software, such as Adobe Reader.
Encryption Choices Rsa Vs Aes Explained Prey

What Is Asymmetric Encryption Read Symmetric Vs Asymmetric Encryption

Check more sample of Asymmetric Key Cryptography Example below
Cryptography Different Types Tools And Its Applications

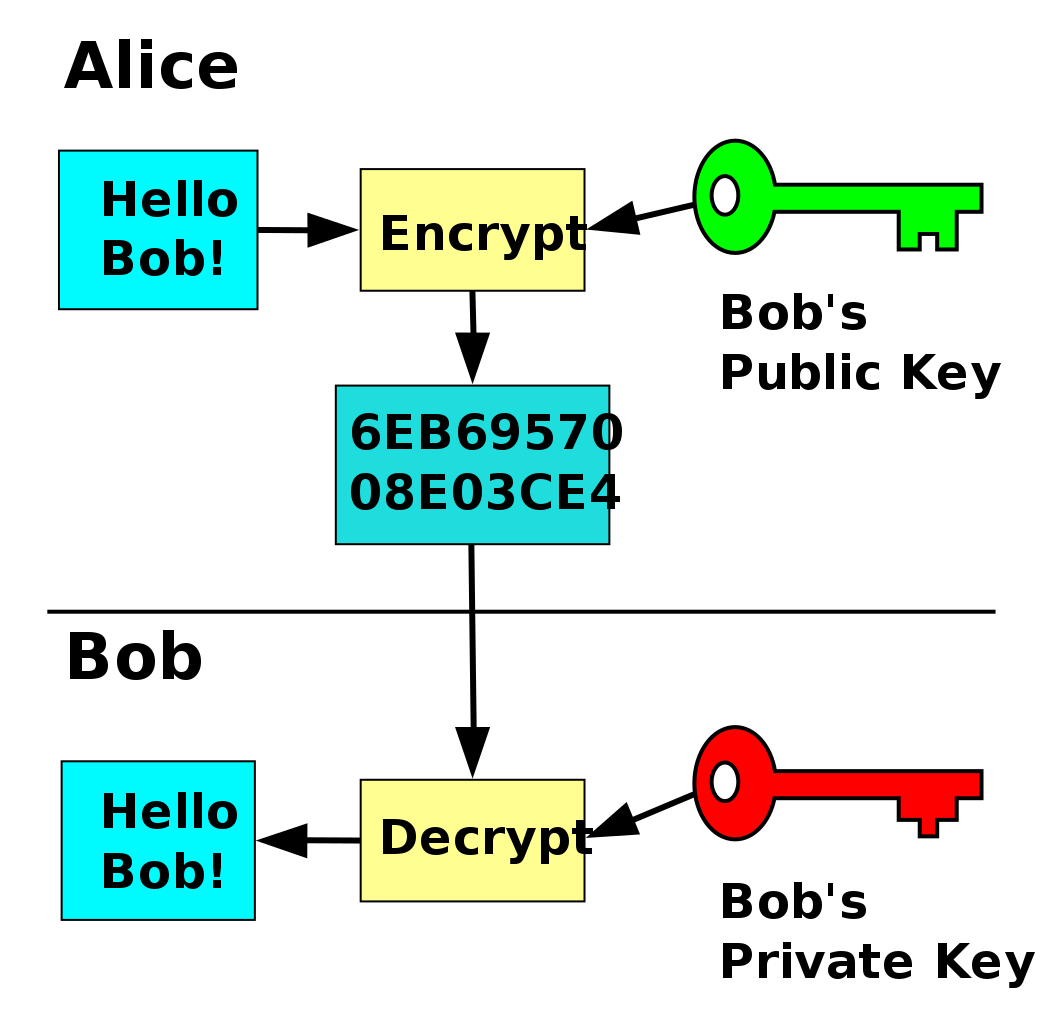
Asymmetric Encryption How Asymmetric Encryption Works

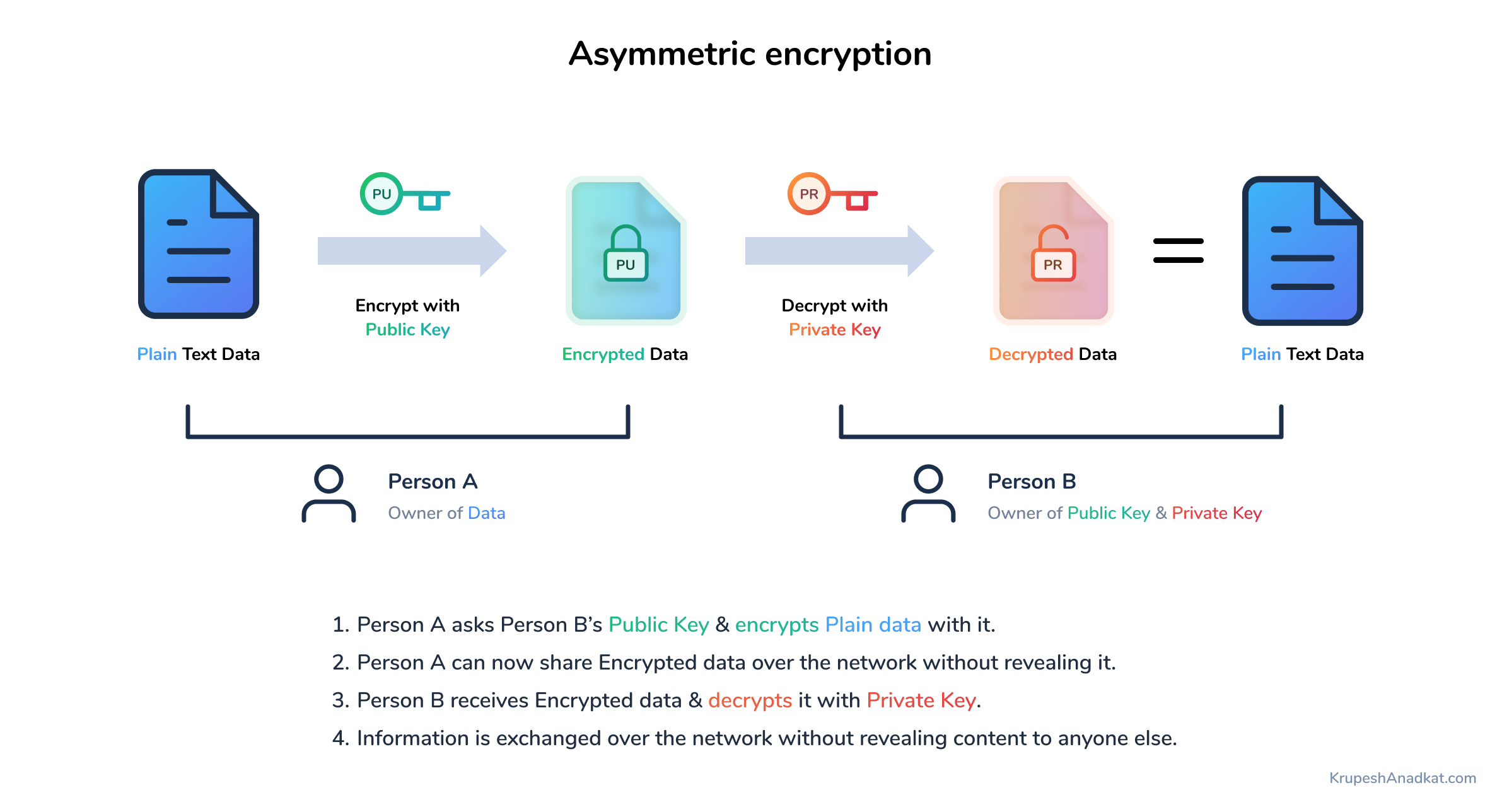
Asymmetric Key Encryption How Your Public Key And Private Keys Are

Public Key Cryptography Decoded What Is Cryptography Ntirawen

Asymmetric Key Cryptography RSA Encryption Algorithm Asymmetric

Asymmetric Encryption For Dummies The Signal Chief

https://www.zhihu.com › question
Asymmetric Convolution Inception V3 3 3 3 1 1 3
https://www.zhihu.com › question
Asymmetric Unit
Asymmetric Convolution Inception V3 3 3 3 1 1 3
Asymmetric Unit

Public Key Cryptography Decoded What Is Cryptography Ntirawen

Asymmetric Encryption How Asymmetric Encryption Works

Asymmetric Key Cryptography RSA Encryption Algorithm Asymmetric

Asymmetric Encryption For Dummies The Signal Chief

Concept Of Cryptography In Blockchain
How To Survive An InfoSec Job Interview cryptography

How To Survive An InfoSec Job Interview cryptography

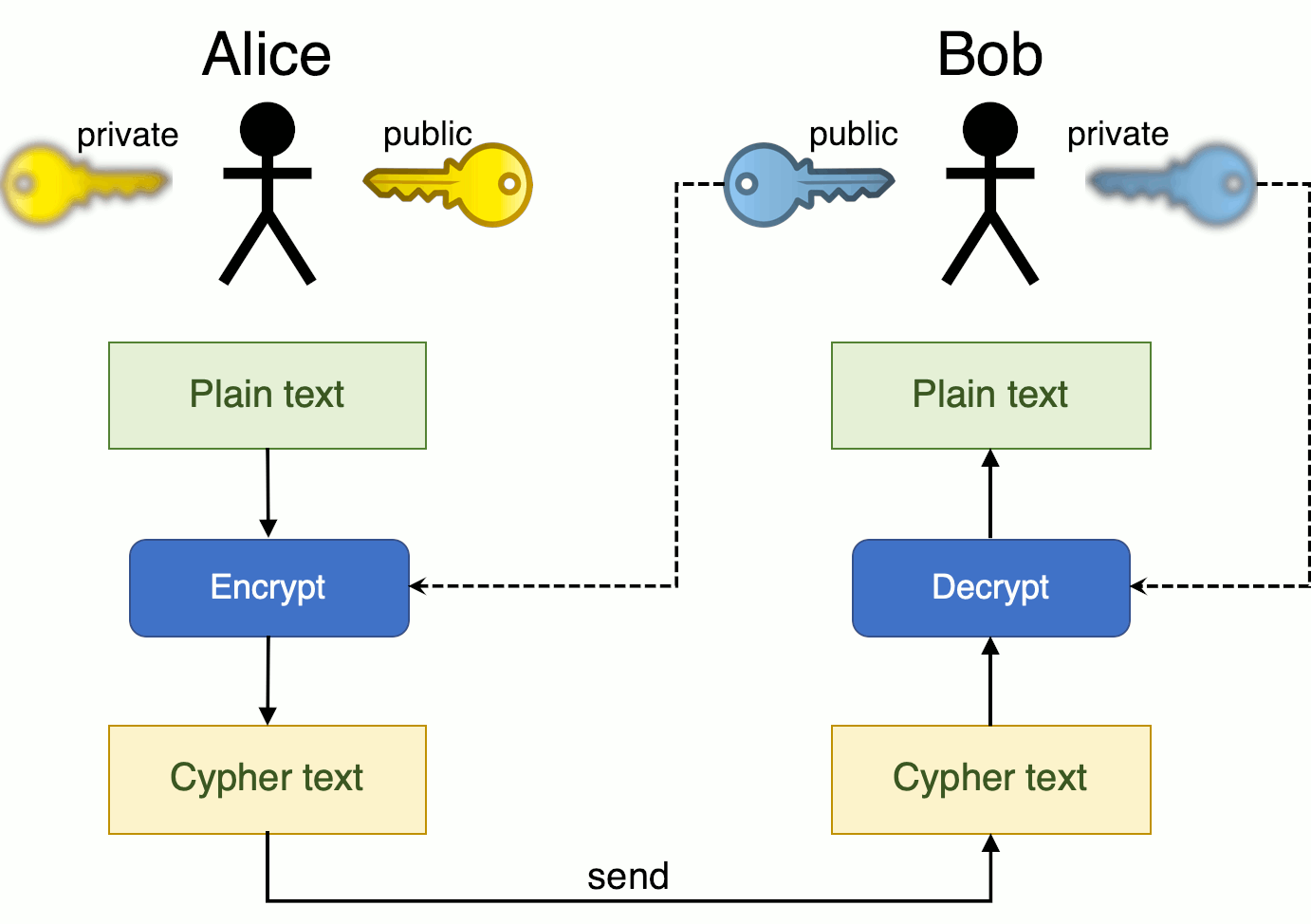
Difference Between Symmetric Asymmetric Key Cryptography Symmetric