In a world with screens dominating our lives and our lives are dominated by screens, the appeal of tangible printed materials isn't diminishing. In the case of educational materials such as creative projects or just adding some personal flair to your home, printables for free are a great resource. For this piece, we'll take a dive deeper into "Asymmetric Cryptography Examples," exploring what they are, where they can be found, and what they can do to improve different aspects of your lives.
Get Latest Asymmetric Cryptography Examples Below
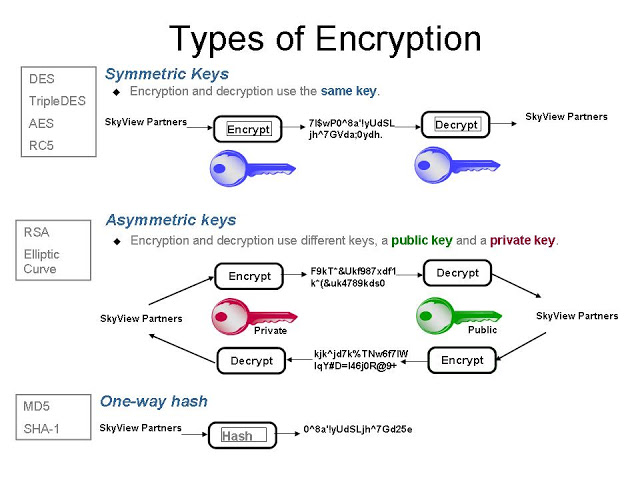
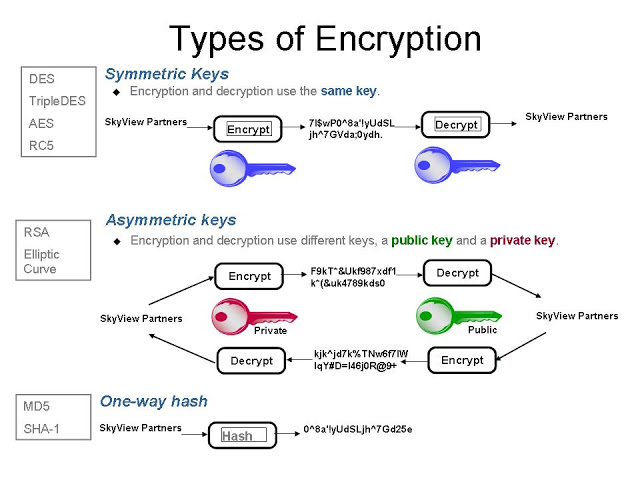
Asymmetric Cryptography Examples
Asymmetric Cryptography Examples -
Gen4 Asymmetric Link Gen4 Gen2 Gen3
Asymmetric Convolution Inception V3 3 3 3 1 1 3
Asymmetric Cryptography Examples include a broad assortment of printable items that are available online at no cost. These printables come in different styles, from worksheets to templates, coloring pages, and more. The benefit of Asymmetric Cryptography Examples lies in their versatility as well as accessibility.
More of Asymmetric Cryptography Examples
Asymmetric Encryption In Nodejs Blog By Marco Melilli

Asymmetric Encryption In Nodejs Blog By Marco Melilli
2011 1
2011 1
Print-friendly freebies have gained tremendous recognition for a variety of compelling motives:
-
Cost-Effective: They eliminate the need to buy physical copies of the software or expensive hardware.
-
customization: The Customization feature lets you tailor designs to suit your personal needs whether you're designing invitations for your guests, organizing your schedule or even decorating your home.
-
Educational Benefits: These Asymmetric Cryptography Examples offer a wide range of educational content for learners of all ages, making them a vital tool for parents and teachers.
-
It's easy: instant access a plethora of designs and templates reduces time and effort.
Where to Find more Asymmetric Cryptography Examples
What Does Encryption Mean And Why Is It Important
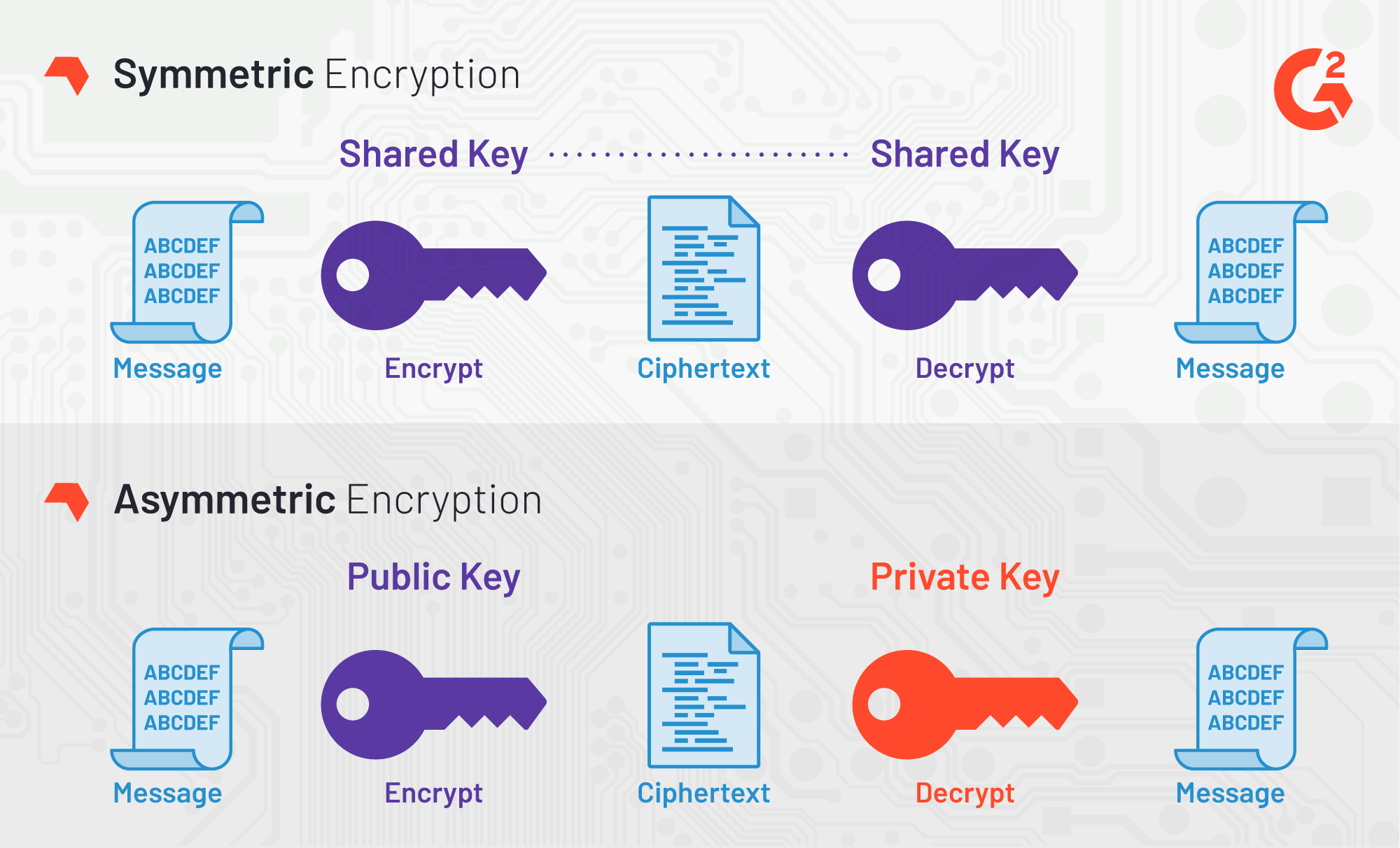
What Does Encryption Mean And Why Is It Important
[desc-9]
EAGLE F1 ASYMMETRIC 5
After we've peaked your interest in printables for free Let's find out where you can locate these hidden treasures:
1. Online Repositories
- Websites such as Pinterest, Canva, and Etsy have a large selection of Asymmetric Cryptography Examples to suit a variety of applications.
- Explore categories like interior decor, education, crafting, and organization.
2. Educational Platforms
- Educational websites and forums typically offer worksheets with printables that are free Flashcards, worksheets, and other educational materials.
- It is ideal for teachers, parents as well as students searching for supplementary sources.
3. Creative Blogs
- Many bloggers offer their unique designs and templates free of charge.
- The blogs are a vast range of topics, everything from DIY projects to party planning.
Maximizing Asymmetric Cryptography Examples
Here are some creative ways of making the most of Asymmetric Cryptography Examples:
1. Home Decor
- Print and frame stunning artwork, quotes, or other seasonal decorations to fill your living spaces.
2. Education
- Utilize free printable worksheets for teaching at-home, or even in the classroom.
3. Event Planning
- Design invitations, banners as well as decorations for special occasions like weddings and birthdays.
4. Organization
- Make sure you are organized with printable calendars for to-do list, lists of chores, and meal planners.
Conclusion
Asymmetric Cryptography Examples are an abundance with useful and creative ideas catering to different needs and preferences. Their accessibility and flexibility make them an essential part of each day life. Explore the many options of Asymmetric Cryptography Examples today and explore new possibilities!
Frequently Asked Questions (FAQs)
-
Are Asymmetric Cryptography Examples truly available for download?
- Yes, they are! You can print and download these materials for free.
-
Can I make use of free printouts for commercial usage?
- It's contingent upon the specific rules of usage. Be sure to read the rules of the creator prior to using the printables in commercial projects.
-
Are there any copyright violations with printables that are free?
- Certain printables could be restricted on their use. Make sure to read the terms and conditions set forth by the designer.
-
How can I print printables for free?
- Print them at home with an printer, or go to any local print store for high-quality prints.
-
What software must I use to open printables free of charge?
- Many printables are offered as PDF files, which can be opened using free software such as Adobe Reader.
Asymmetric Encryption Method Advantages And Disadvantages Electrodummies

Role Of Cryptography In Information Security Cloudkul
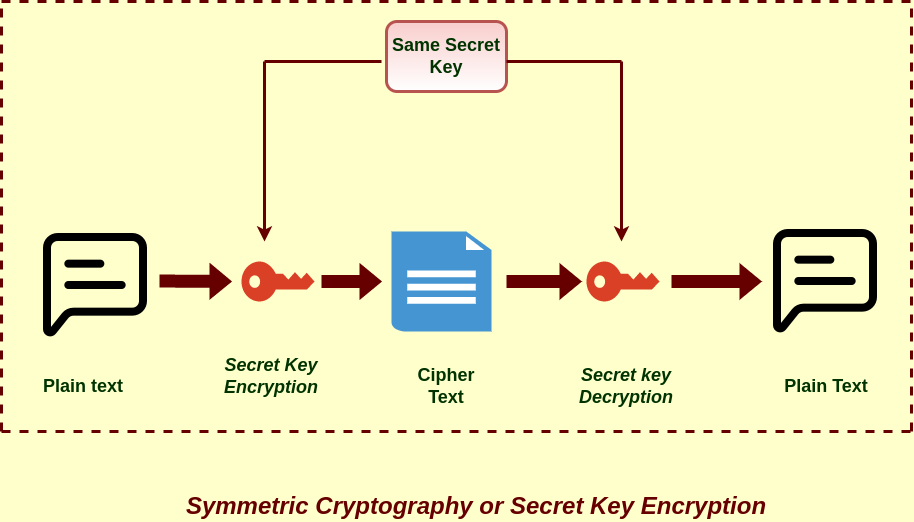
Check more sample of Asymmetric Cryptography Examples below
Asymmetric Key Cryptography RSA Encryption Algorithm Asymmetric

Encryption Choices Rsa Vs Aes Explained Prey

Asymmetric Encryption For Dummies The Signal Chief
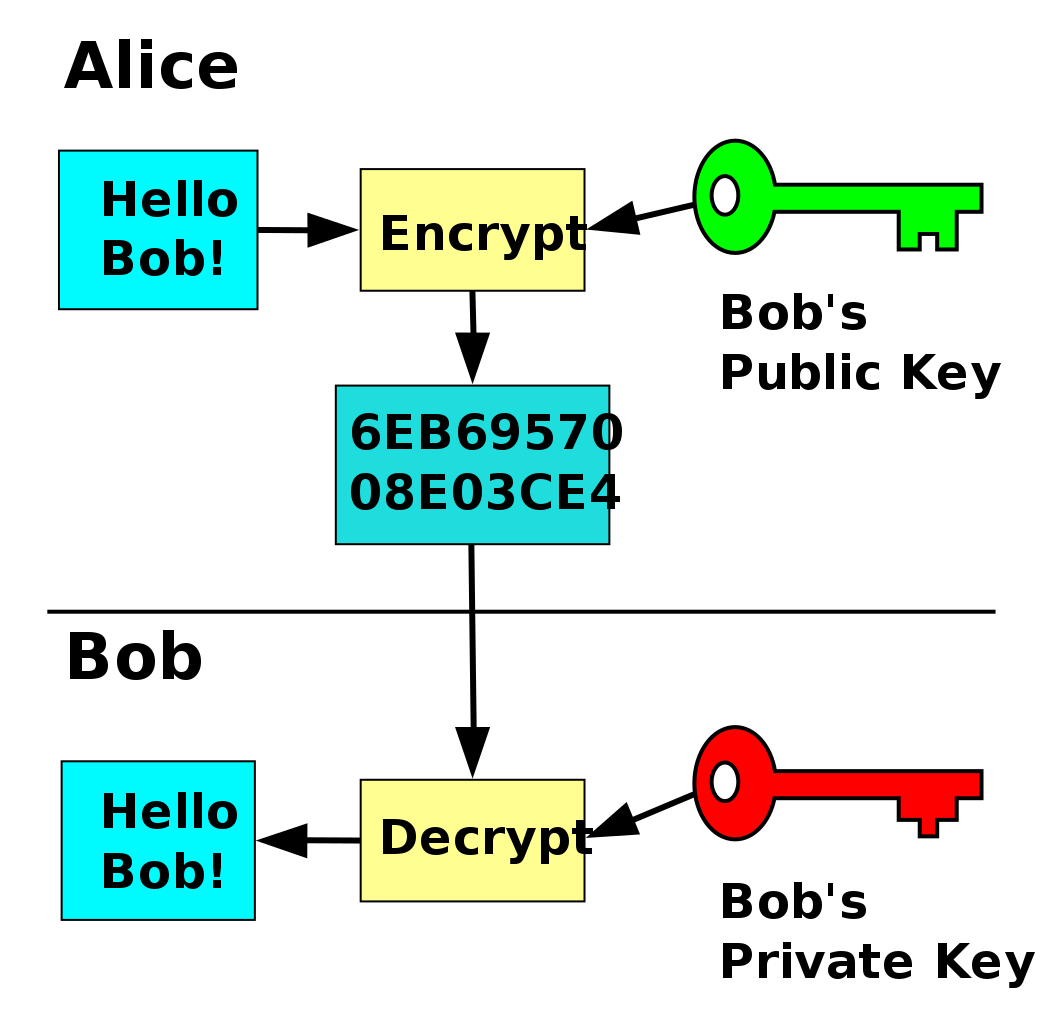
Symmetric Vs Asymmetric Encryption Differences Explained

What Is Asymmetric Encryption Babypips

Difference Between Symmetric Asymmetric Key Cryptography Symmetric

https://www.zhihu.com › question
Asymmetric Convolution Inception V3 3 3 3 1 1 3

https://www.zhihu.com › question
Asymmetric Unit
Asymmetric Convolution Inception V3 3 3 3 1 1 3
Asymmetric Unit

Symmetric Vs Asymmetric Encryption Differences Explained

Encryption Choices Rsa Vs Aes Explained Prey

What Is Asymmetric Encryption Babypips

Difference Between Symmetric Asymmetric Key Cryptography Symmetric

The Basic Art Of Cryptography Coinmonks Medium

Chirag s Blog Difference Between Symmetric And Asymmetric Key

Chirag s Blog Difference Between Symmetric And Asymmetric Key

What Is Asymmetric Encryption Bitpanda Academy