In this age of electronic devices, in which screens are the norm and the appeal of physical printed material hasn't diminished. Be it for educational use project ideas, artistic or just adding an extra personal touch to your space, Asymmetric Cryptographic Algorithms List have proven to be a valuable source. Here, we'll dive into the world "Asymmetric Cryptographic Algorithms List," exploring the benefits of them, where to get them, as well as how they can improve various aspects of your lives.
Get Latest Asymmetric Cryptographic Algorithms List Below

Asymmetric Cryptographic Algorithms List
Asymmetric Cryptographic Algorithms List -
Gen4 Asymmetric Link Gen4 Gen2 Gen3
Asymmetric Convolution Inception V3 3 3 3 1 1 3
Printables for free include a vast assortment of printable materials online, at no cost. They are available in numerous formats, such as worksheets, coloring pages, templates and many more. The appealingness of Asymmetric Cryptographic Algorithms List is their versatility and accessibility.
More of Asymmetric Cryptographic Algorithms List
Public Key Cryptography Decoded What Is Cryptography Ntirawen

Public Key Cryptography Decoded What Is Cryptography Ntirawen
2011 1
2011 1
Asymmetric Cryptographic Algorithms List have gained a lot of popularity due to numerous compelling reasons:
-
Cost-Efficiency: They eliminate the need to buy physical copies or expensive software.
-
customization: You can tailor the design to meet your needs for invitations, whether that's creating them to organize your schedule or decorating your home.
-
Education Value Education-related printables at no charge cater to learners of all ages, making them a useful resource for educators and parents.
-
Affordability: Quick access to a plethora of designs and templates cuts down on time and efforts.
Where to Find more Asymmetric Cryptographic Algorithms List
Most Popular Optimization Algorithms Download Scientific Diagram

Most Popular Optimization Algorithms Download Scientific Diagram
[desc-9]
EAGLE F1 ASYMMETRIC 5
We've now piqued your interest in printables for free Let's look into where you can find these hidden treasures:
1. Online Repositories
- Websites like Pinterest, Canva, and Etsy provide a wide selection and Asymmetric Cryptographic Algorithms List for a variety goals.
- Explore categories such as decorating your home, education, crafting, and organization.
2. Educational Platforms
- Educational websites and forums often provide worksheets that can be printed for free for flashcards, lessons, and worksheets. tools.
- The perfect resource for parents, teachers, and students seeking supplemental sources.
3. Creative Blogs
- Many bloggers are willing to share their original designs and templates at no cost.
- These blogs cover a wide array of topics, ranging starting from DIY projects to party planning.
Maximizing Asymmetric Cryptographic Algorithms List
Here are some inventive ways in order to maximize the use use of printables for free:
1. Home Decor
- Print and frame stunning images, quotes, or seasonal decorations that will adorn your living areas.
2. Education
- Use printable worksheets from the internet for teaching at-home also in the classes.
3. Event Planning
- Invitations, banners as well as decorations for special occasions like birthdays and weddings.
4. Organization
- Stay organized with printable calendars for to-do list, lists of chores, and meal planners.
Conclusion
Asymmetric Cryptographic Algorithms List are an abundance of fun and practical tools that cater to various needs and desires. Their accessibility and flexibility make them an invaluable addition to both professional and personal lives. Explore the vast array of Asymmetric Cryptographic Algorithms List to discover new possibilities!
Frequently Asked Questions (FAQs)
-
Are printables that are free truly cost-free?
- Yes, they are! You can download and print these materials for free.
-
Can I download free printouts for commercial usage?
- It's dependent on the particular conditions of use. Always read the guidelines of the creator before using any printables on commercial projects.
-
Are there any copyright issues when you download printables that are free?
- Certain printables may be subject to restrictions on usage. Make sure to read the conditions and terms of use provided by the author.
-
How do I print Asymmetric Cryptographic Algorithms List?
- Print them at home with an printer, or go to any local print store for better quality prints.
-
What software must I use to open printables that are free?
- Most PDF-based printables are available in the format PDF. This can be opened with free programs like Adobe Reader.
Symmetric Vs Asymmetric Encryption Differences Explained

Cryptographic Algorithms List

Check more sample of Asymmetric Cryptographic Algorithms List below
What Is Asymmetric Cryptography Definition From SearchSecurity
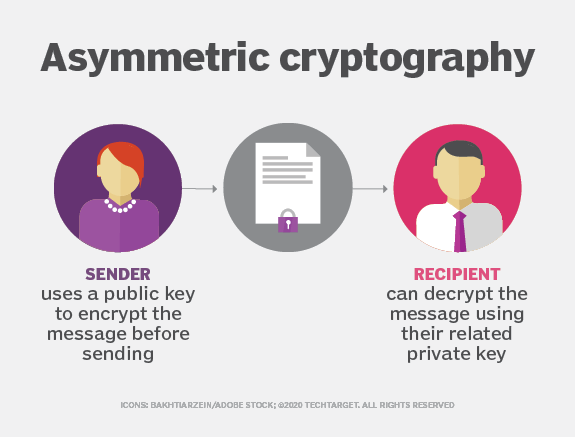
What Are The Three Types Of Cryptography BEST GAMES WALKTHROUGH
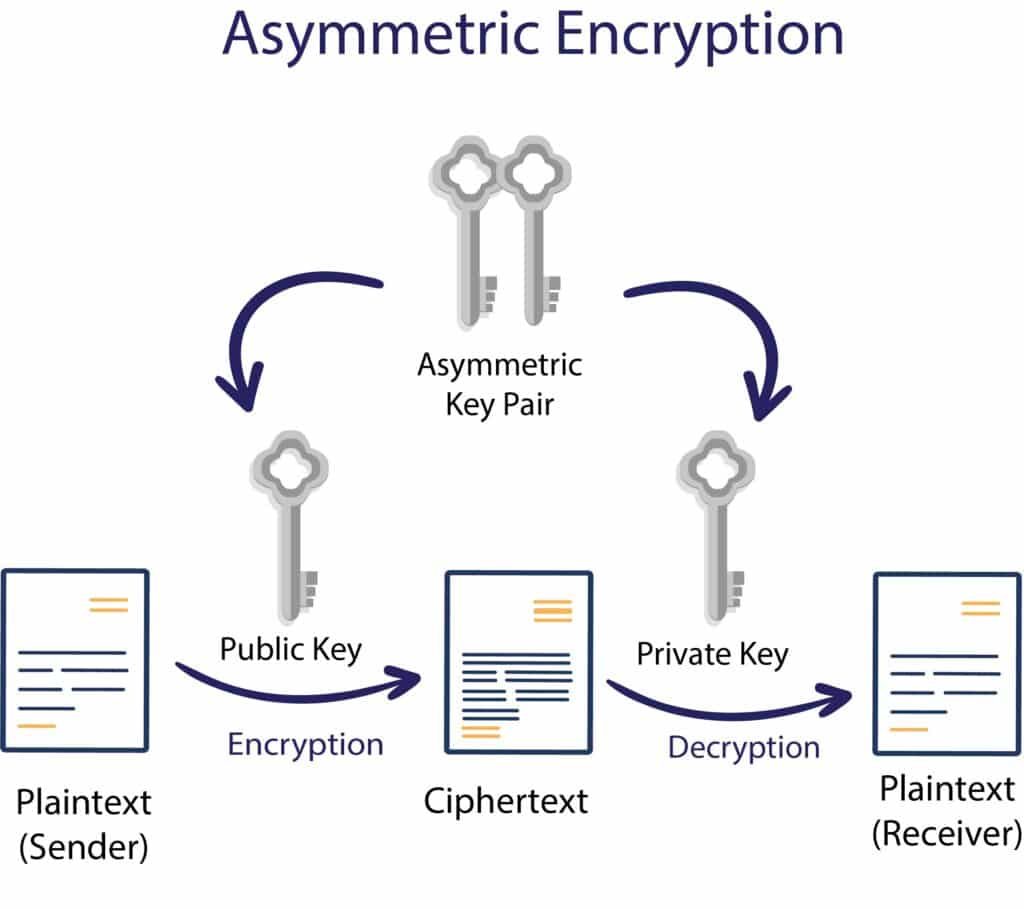
Cryptography CyberSecurity Studio
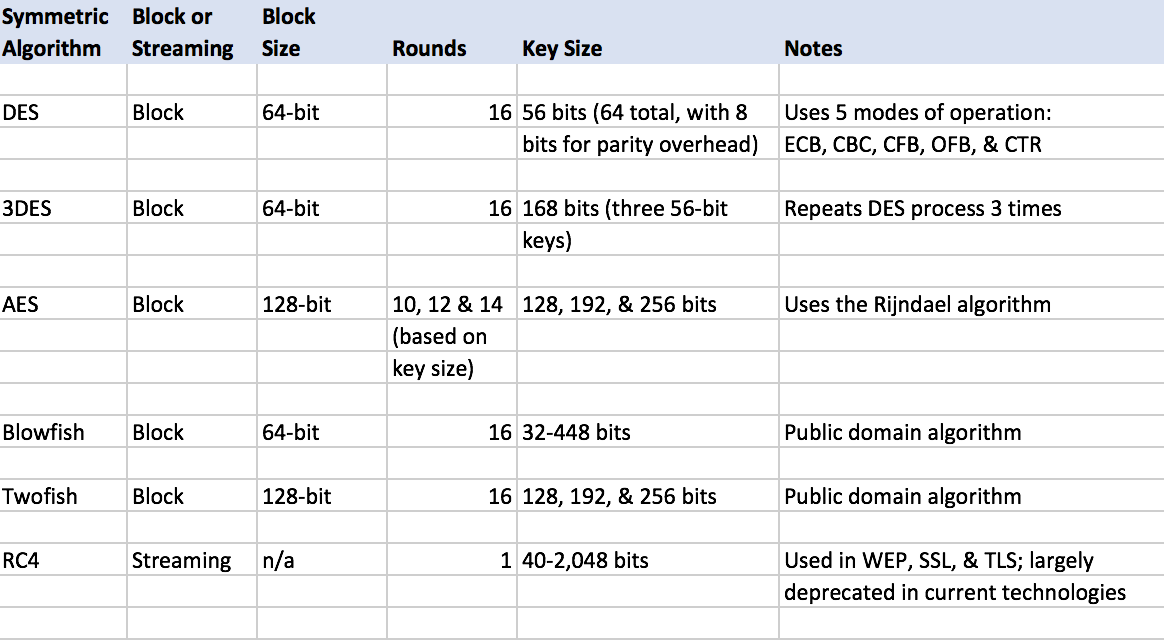
Asymmetric Cryptographic Algorithms Ppt Download

Types Of Cryptography Download Scientific Diagram

Cryptographic Algorithms List


https://www.zhihu.com › question
Asymmetric Convolution Inception V3 3 3 3 1 1 3
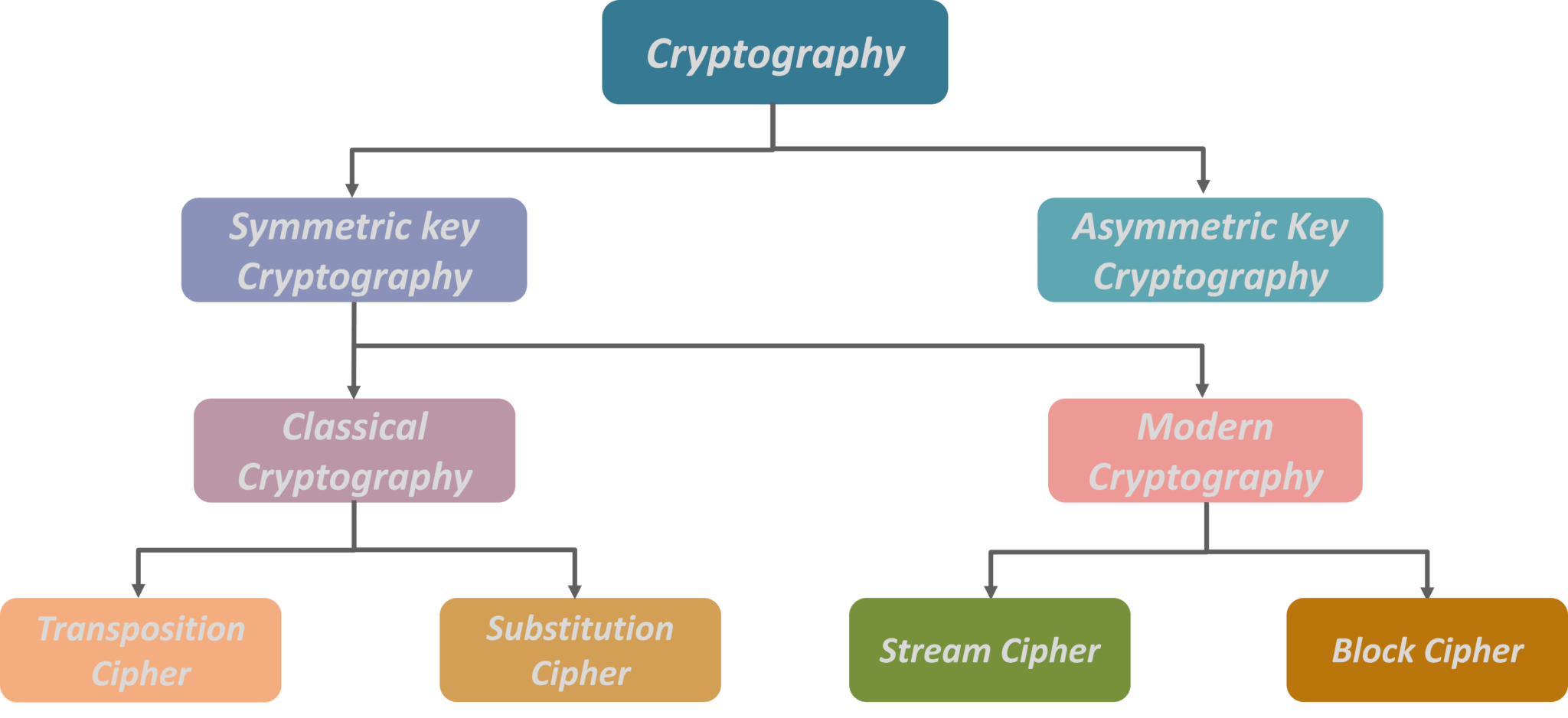
https://www.zhihu.com › question
Asymmetric Unit
Asymmetric Convolution Inception V3 3 3 3 1 1 3
Asymmetric Unit

Asymmetric Cryptographic Algorithms Ppt Download

What Are The Three Types Of Cryptography BEST GAMES WALKTHROUGH

Types Of Cryptography Download Scientific Diagram

Cryptographic Algorithms List

Encryption Choices Rsa Vs Aes Explained Prey

Difference Between Symmetric And Asymmetric Encryption Encryption

Difference Between Symmetric And Asymmetric Encryption Encryption
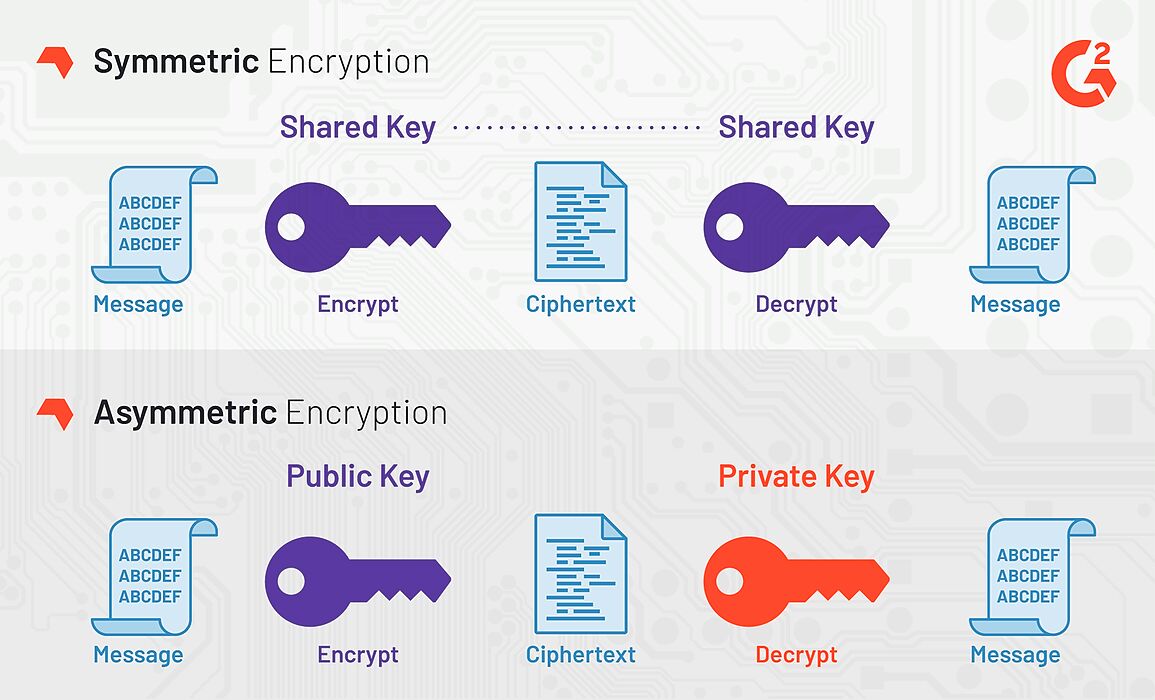
Cryptographic Algorithms Deep Notes